What is Multi-Extortion Ransomware?
Multi-extortion ransomware, sometimes called multifaceted extortion, uses multiple layers of attack to persuade victims to pay a ransom to the attacker. In addition to encrypting files, this type of cybersecurity attack might include additional attack methods, such as file exfiltration, distributed denial of service (DDoS) attacks or extending ransoms to third-party associates.
What Is Ransomware?
Ransomware is a type of malicious software that blocks access to a computer system or set of data until a sum of money is paid. When the ransomware infects a victim's computer, it typically begins by encrypting specific files on the victim's system, making them inaccessible.
The malware operator then issues a ransom demand to the victim, usually delivered via a message on their computer screen or a separate communication channel, such as email. The message will often include a deadline for payment and a threat to delete the victim's encrypted files if the ransomware payment is not made within the specified time frame.
Ransomware attacks can financially devastate individuals and organizations, losing valuable data and disrupting critical systems. Organizations must remain aware of the latest threats and implement ransomware protection strategies.
What Is Double Extortion Ransomware?
In addition to encrypting the victim's files, double extortion ransomware adds a second layer to the cyberattack involving the ransomware operator exfiltrating files and threatening to publicly release the victim's data unless the ransom is paid. The added threat increases the pressure on the victim to pay the ransom quickly and makes it more difficult for them to refuse to pay.
Double extortion ransomware attacks can be particularly damaging because they disrupt the victim's ability to access their own data while also potentially exposing sensitive or confidential information to the public.
What Is Triple Extortion Ransomware?
As the name suggests, triple extortion ransomware attacks involve another layer of attack on top of file encryption and data theft. Depending on the type of ransomware, this could take various forms. One popular attack vector is service disruption (for example, a DDoS attack). In addition to the loss of data and data exposure, the victim might additionally experience a threat to critical operations.
Another attack layer growing in popularity among ransomware groups is third-party associate attacks. In this example of triple extortion tactics, the attacker extends threats and ransom demands to the original victim's clients, suppliers or other associates.
The Evolution of Modern Ransomware Attacks

Modern ransomware attacks have seen a variety of shifts as they advance in both scope and complexity. In the past, attacks were generally indiscriminate, using email phishing and malvertisements as the primary attack vector. These days, threat actors are more likely to select their victims carefully, leveraging specialized exploit kits to infiltrate networks.
The nature of ransomware execution has changed, too. As organizations implement ransomware protection strategies, malicious actors develop increasingly sophisticated attacks. Advanced techniques have paved the way for multi-extortion ransomware that can include several complex attack layers.
What Are the Phases of Ransomware Extortion?
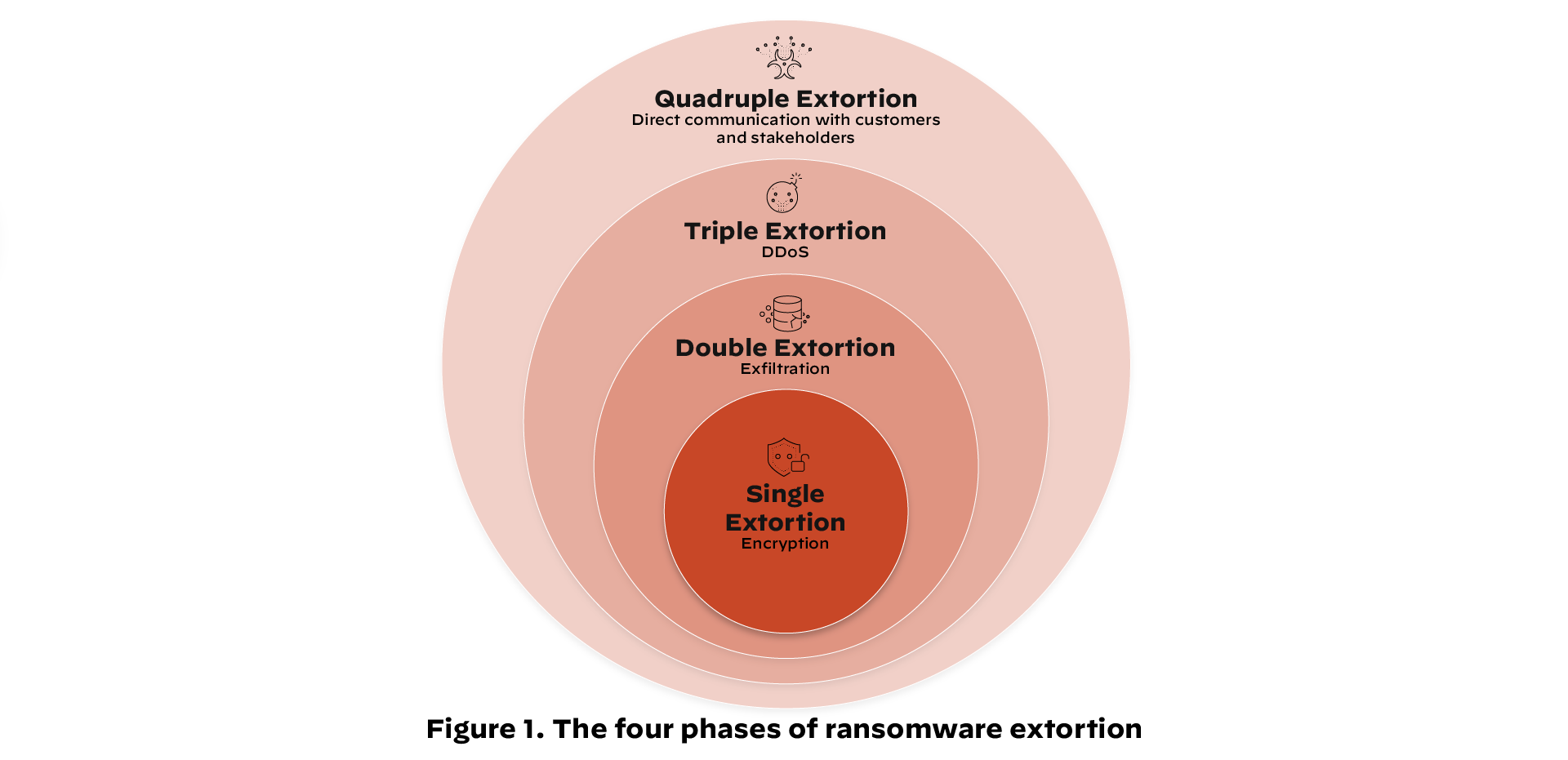
A multi-extortion ransomware attack initially involves the installation of malware on the victim's system. Cyberattackers achieve this through a variety of methods, such as malicious email attachments, malvertisements, exploit kits or unauthorized RDP access.
The installation is followed by several phases of execution.
Single Extortion
Single extortion ransomware (the first multi-extortion ransomware phase ) involves encryption. Attackers either encrypt whole systems or select files deemed highly important. Single Extortion is the sole method of attack for some types of ransomware, such as WannaCry and CryptoLocker.
Double Extortion
Many organizations overcome the threat of file encryption with a simple up-to-date backup system. To combat this trend, malware operators have added another phase of extortion, which involves data exfiltration, a tactic made popular through malware such as Maze and DoppelPaymer. Attackers steal sensitive data and threaten to leak it to the public (often via dark web leak sites) or sell it on the black market.
Triple Extortion
A triple extortion attack can take different forms, but it typically expands the playing field further for attackers. For example, if the victim refuses to pay the ransom even after the threat of information disclosure, the cyberattacker might use a service disruption attack to exert additional pressure. AvosLocker is one type of ransomware that uses DDoS attacks as part of its triple extortion toolkit.
Quadruple Extortion
Threat actors can also expand their gains with quadruple extortion ransomware that adds an additional layer, often involving contacting third-party associates with ransom demands or other underhanded tactics. For example, when hardware supplier Quanta failed to pay the REvil ransomware group, the attackers turned their sights to Apple, one of Quanta's clients.
Four New Multi-Extortion Methods
Ransomware attackers continuously modify and adjust their extortion schemes. Organizational leaders must understand and manage protections for the following new extortion techniques.
DDoS Extortion Attacks
In a DDoS attack, threat actors attempt to disrupt a website's function or online service by flooding it with traffic from multiple sources and demanding payment from the victim in exchange for stopping the attack. These attacks can cause a website or service to become unavailable to legitimate users, seriously harming businesses that rely on the internet.
Contacting a Business's Customers and Partners
Threat actors may extend attacks to third-party associates, such as clients, patients, vendors, partners and affiliates. Attackers communicate with these parties directly, often threatening to leak sensitive information unless they receive the ransom. For example, an attacker might contact a victim organization's patients and threaten to publish sensitive health data.
Short Selling Stocks
Another tactic, first used by the DarkSide ransomware group, is threatening publicly traded companies by offering short stock opportunities to unscrupulous traders. In this type of attack, the gang threatens to publicly list the victim organization's name, which could cause the stock price to fall. With insider knowledge of the attack, a trader could stand to make a hefty profit.
Disrupting Critical Infrastructure Systems
Of particular concern is the increasing ability of ransomware groups to infiltrate and disrupt critical infrastructure systems. The increasing reliance of these systems on information technology opens them up to vulnerabilities such as ransomware attacks. A 2022 US Homeland Security Report states that "ransomware gangs constantly attack critical infrastructure." Examples include attacks against Colonial Pipeline Co. and JBS Foods.
How to Protect Your Organization from Ransomware Attacks
Cybersecurity is important for all businesses, and ransomware attacks can have serious consequences. Here are four key ransomware protection strategies that can help prevent attacks or minimize their impact:
- Establish Policies: Put in place strong policies governing computer access and the handling of sensitive information.
- Protect Your Systems: Protect your systems with robust firewalls, encrypted networks, malware prevention software and regular updates.
- Monitor for Malicious Activity: Monitoring for any malicious activity must be a top priority in any ransomware protection strategy. Quickly investigate any suspicious activities to limit potential damage caused by an attack and prevent bad actors from infiltrating your systems.
- Respond to Attacks: A swift and effective ransomware incident response plan in reaction to threats or breaches is crucial.
Putting these measures in place will help protect your business from ransomware attacks and give your security team peace of mind that you're doing everything possible to prevent them.