What Is IKEv2 (Internet Key Exchange version 2)?
IKEv2 is a key management protocol that facilitates secure internet connections by managing the encryption and authentication processes in IPsec security associations.
Developed by Cisco and Microsoft, IKEv2 provides strong encryption and supports protocols such as IPsec for secure data transit. Because of its efficiency in re-establishing dropped connections, the protocol is favored for maintaining stable VPN sessions, especially when the network environment is changing, such as transitioning from Wi-Fi to mobile data.
How Does IKEv2 Work?
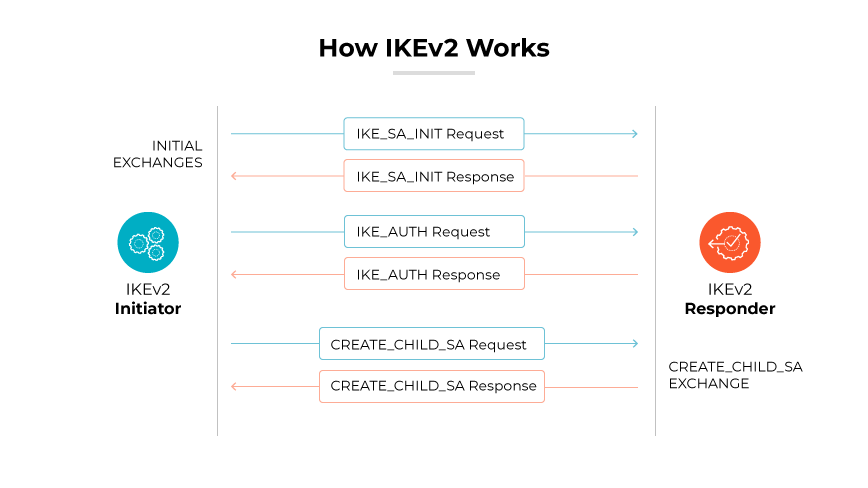
IKEv2 (Internet Key Exchange version 2) works as a tunneling protocol to establish a secure connection over the internet. Developed jointly by Cisco and Microsoft, it ensures that both VPN client and server authenticate each other and agree upon encryption methods for secure communication. Its operation involves a two-phase exchange process. Phase one establishes the secure channel to negotiate the methods and keys for encryption. Phase two manages the actual data transfer. The protocol is responsible for managing the IP addresses during the establishment of the VPN connection.
The protocol begins with the IKE SA (Security Association) initiation, where the VPN client and server exchange proposals for how to encrypt and authenticate the connection. They agree upon which encryption and authentication methods to use, often relying on a Diffie-Hellman key exchange to create a shared secret key without it being transmitted over the internet. This phase results in the establishment of the IKE SA, a secure channel through which the VPN client and server can safely communicate.
In the second phase, IKEv2 works with IPsec to transport data securely. IPsec encapsulates the data packets, encrypting them to maintain confidentiality, and authenticates them to ensure data integrity and origin verification. Internet Key Exchange version 2 manages the IPsec SAs which dictate the specifics of the encryption and authentication, including the use of cryptographic algorithms and keys.
The protocol is flexible, supporting rekeying operations which renew encryption keys to maintain security over the connection lifetime. It also quickly re-establishes VPN tunnels when temporary connectivity issues occur, making it reliable for mobile users who may switch between different networks. IKEv2's support for MOBIKE (Mobility and Multihoming Protocol) enhances its performance in mobile environments.
Internet Key Exchange version 2’s efficiency is heightened because of its support for multiple encryption standards, and mechanisms like Perfect Forward Secrecy (PFS), which frequently changes encryption keys to prevent data compromise. It uses X.509 certificates for server authentication, verifying the server's identity to the client, and securing the connection against potential man-in-the-middle attacks.
Overall, Internet Key Exchange version 2 is recognized for strong security, reliability, and compatibility with major operating systems. It balances performance and security, providing a secure and stable VPN experience, especially for users requiring constant connectivity across various networks.
What Is the Difference Between IKEv1 and IKEv2?
| IKEv1 vs. IKEv2 | |
|---|---|
| IKEv1 | IKEv2 |
| Less efficient in establishing secure connections. | More efficient with faster setup of secure VPN connections. |
| Limited support for modern encryption and authentication methods. | Supports advanced encryption algorithms like AES and uses EAP for authentication. |
| Does not support Perfect Forward Secrecy. | Implements Perfect Forward Secrecy, enhancing security for session keys. |
| Prone to instability with network changes. | Improved stability, handling network changes and interruptions efficiently. |
| Designed for less dynamic network environments. | Optimized for modern dynamic internet use and supports seamless network transitions. |
IKEv1 and IKEv2 are both protocols used to establish a secure, encrypted VPN connection. They differ significantly in their efficiency and security features. The more recent protocol offers improvements which allow users to maintain VPN connections while changing networks. The newer version also features built-in support for NAT traversal, facilitating connections behind NAT devices. The current protocol also uses fewer messages to establish a connection, reducing the time it takes to set up a VPN.
The IKEv2 VPN protocol is superior in terms of security enhancements, including the use of stronger encryption algorithms like AES, and the implementation of Extensible Authentication Protocol (EAP) for authentication purposes. The protocol also supports Perfect Forward Secrecy, providing additional protection by ensuring the compromise of one encryption key will not lead to the compromise of others.
Internet Key Exchange version 2’s architecture is more resistant to network changes and interruptions, offering a more stable VPN experience compared to IKEv1. It has been designed to handle the dynamics of modern internet use, without dropping the secure VPN tunnel established between the client and the server.
Overall, Internet Key Exchange version 2 offers enhancements which make it more suited for current VPN needs, delivering faster, more secure, and more reliable connections. Its backward compatibility with IKEv1 ensures it can be integrated into existing infrastructures while providing the option to upgrade to more secure connections.
What Is IKEv2 Used For?
Internet Key Exchange version 2 is commonly used in enterprise environments where robust security and seamless connectivity across various networks are paramount. Its ability to maintain stable VPN connections while transitioning between different networks, such as from wired to wireless, makes it ideal for mobile users who require consistent access to enterprise resources. This protocol is particularly useful for employees who frequently travel or work remotely since it supports the Mobility and Multi-homing (MOBIKE) protocol.
In scenarios where secure, site-to-site connections are needed, Internet Key Exchange version 2 facilitates the establishment of VPN tunnels that ensure encrypted communication between corporate branches. It is an effective solution for creating a secure bridge between headquarters and remote locations, protecting data integrity and confidentiality over potentially insecure networks. The protocol's efficiency in handling network changes without dropping connections also makes it suitable for dynamic business environments where network reliability is critical for operations.
Internet Key Exhange version 2 is also advantageous for organizations that manage a diverse array of devices and operating systems. Given its native support across many platforms, the protocol allows for straightforward implementation, reducing complexity in VPN deployments. Its support for a variety of authentication methods enhances security, providing flexibility in aligning with an organization's specific authentication policies.
Pros and Cons of IKEv2
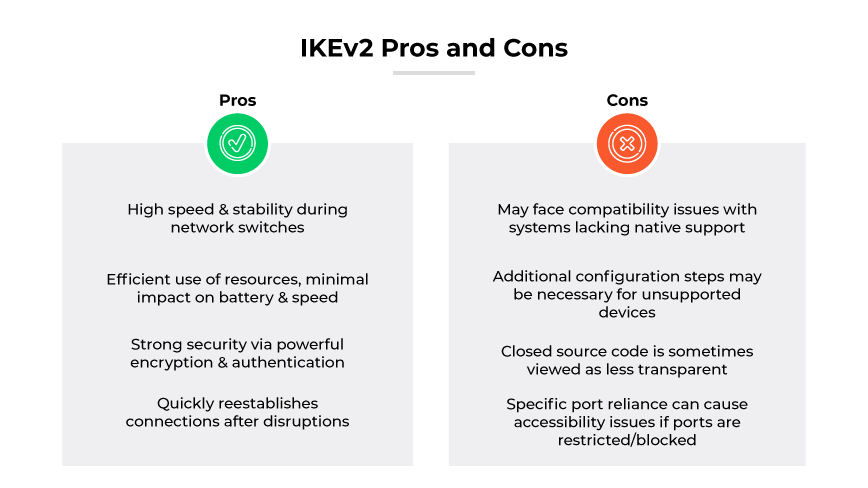
The Internet Key Exchange version 2 (IKEv2) protocol is lauded for speed and stability, especially when maintaining VPN connections during network switches. IKEv2 offers efficient use of resources which ensures high performance, with minimal impact on device battery life and speed. Security is a notable strength, with support for powerful encryption algorithms and robust authentication methods. The protocol's ability to quickly reestablish connections after temporary disruptions contributes to a seamless user experience.
However, the protocol is not without drawbacks. It may face compatibility issues with devices or systems that lack native support, potentially necessitating additional configuration steps. While its encryption is strong, the closed nature of its source code could be a concern for those who prefer open source transparency. Reliance on specific ports for communication can lead to accessibility issues if these ports are restricted or blocked by network administrators.
Is IKEv2 Secure?
IKEv2 is regarded as a secure VPN protocol. It incorporates methods like Diffie-Hellman key exchange to establish safe connections, ensuring that each session has unique encryption keys. Perfect Forward Secrecy (PFS) provides an additional layer of security by generating new keys for each session. Internet Key Exchange version 2 uses asymmetric authentication methods, such as X.509 certificates, to securely validate the identities of the VPN client and server.
Despite robust security features, questions about Internet Key Exchange version 2’s impenetrability have been raised. There are concerns which suggest entities with significant resources may potentially breach the protocol’s defenses. However, when correctly implemented by a VPN provider, it is still considered to offer strong protection for digital communications. The protocol is widely viewed as suitable for most users and use cases in an enterprise environment.
Why Is IKEv2 Always Combined with IPsec?
IKEv2 is invariably paired with IPsec to provide a complete suite for secure network communications. This partnership uses the strengths of both protocols—IKEv2's efficient management of security associations and IPsec's robust payload encryption. Internet Key Exchange version 2 facilitates negotiation of the security attributes that IPsec will use, ensuring data passes through encrypted tunnels with agreed upon cryptographic parameters. IPsec, working at the kernel level, is responsible for the encryption and decryption of the actual data, providing a secure path for transmission of sensitive information.
The combination of Internet Key Exchange version 2 and IPsec allows for features like automatic VPN reconnection after temporary network disruptions. It also supports configurations that enable the connection to remain active. The pair is widely used across various platforms because of proven reliability, flexibility in supporting different encryption algorithms, and consistent connections. Their joint operation is a standard, creating a dependable foundation for secure enterprise level VPN deployments.
Comparing IKEv2 with Other Protocols
IKEv2 vs. L2TP/IPsec
L2TP/IPsec is a widespread protocol because of its native support across various platforms. However, it falls short of Internet Key Exchange version 2’s performance benchmarks, which offer improved negotiation of security associations and quicker, more reliable connections. Its support for the MOBIKE protocol makes it superior in maintaining VPN connections while switching networks, a feature L2TP/IPsec lacks.
IKEv2 vs. OpenVPN
OpenVPN offers a versatile and strong security posture, being open source and auditable. Internet Key Exchange version 2 matches OpenVPN in security but generally exceeds in speed, thanks to its efficient use of network resources. While OpenVPN has better firewall traversal capabilities because of its use of TCP port 443, Internet Key Exchange version 2 is often favored for mobile devices because of its quick reconnection capabilities.
IKEv2 vs. WireGuard
WireGuard offers simplicity and performance. It shares many of Internet Key Exchange version 2’s advantages, such as a lean codebase and strong encryption standards. WireGuard is still undergoing extensive security audits, making Internet Key Exchange version 2 a more established choice for now.
IKEv2 vs. SSTP and PPTP
While SSTP provides reliable security, It is predominantly bound to Windows environments, limiting its deployment. PPTP, on the other hand, is widely considered obsolete because of several known security vulnerabilities. Internet Key Exchange Version 2’s advantage over both is its platform agnosticism and robust security features without the vulnerabilities associated with PPTP or the platform limitations of SSTP.