Industrial OT Security
- What are examples of cyber-physical systems?
- What is the difference between a cyber-physical system and an Internet of Things (IoT) device?
- Why is cyber-physical system security important?
- What are the common cyber-physical system security challenges?
- What to look for in a CPS protection platform
- Cyber-physical systems security FAQs
What Is Cyber-Physical Systems Security (CPSSEC)? | Overview
Cyber-physical systems security (CPSSEC) involves protecting the integration of computational algorithms with physical processes in systems that monitor, control, and optimize real-world activities.
CPS security secures the devices and networks that link physical systems with computing resources, addressing risks that could compromise operations or cause physical damage. CPSSEC is necessary for ensuring the reliability and security of cyber-physical systems.
- What are examples of cyber-physical systems?
- What is the difference between a cyber-physical system and an Internet of Things (IoT) device?
- Why is cyber-physical system security important?
- What are the common cyber-physical system security challenges?
- What to look for in a CPS protection platform
- Cyber-physical systems security FAQs
- 1. What are examples of cyber-physical systems?
- 2. What is the difference between a cyber-physical system and an Internet of Things (IoT) device?
- 3. Why is cyber-physical system security important?
- 4. What are the common cyber-physical system security challenges?
- 5. What to look for in a CPS protection platform
- 6. Cyber-physical systems security FAQs
What are examples of cyber-physical systems?
Cyber-physical systems (CPS) are integrated systems that combine computing, networking, and physical processes. They’re used across various industries to improve efficiency, safety, and productivity.
As CPSs continue to evolve, security is becoming exponentially important. Organizations have to be able to effectively protect critical infrastructure, prevent operational disruptions, and ensure safety.
Let’s take a look at some examples of CPS systems and their security implications, including:
- Operational technology (OT)
- Industrial Internet of Things (IIoT)
- Industrial control systems (ICS)
- Building management systems (BMS)
- Smart grids
- Smart buildings
- Robotics
- Smart transportation systems
- Medical devices
- Smart manufacturing
Operational technology (OT)
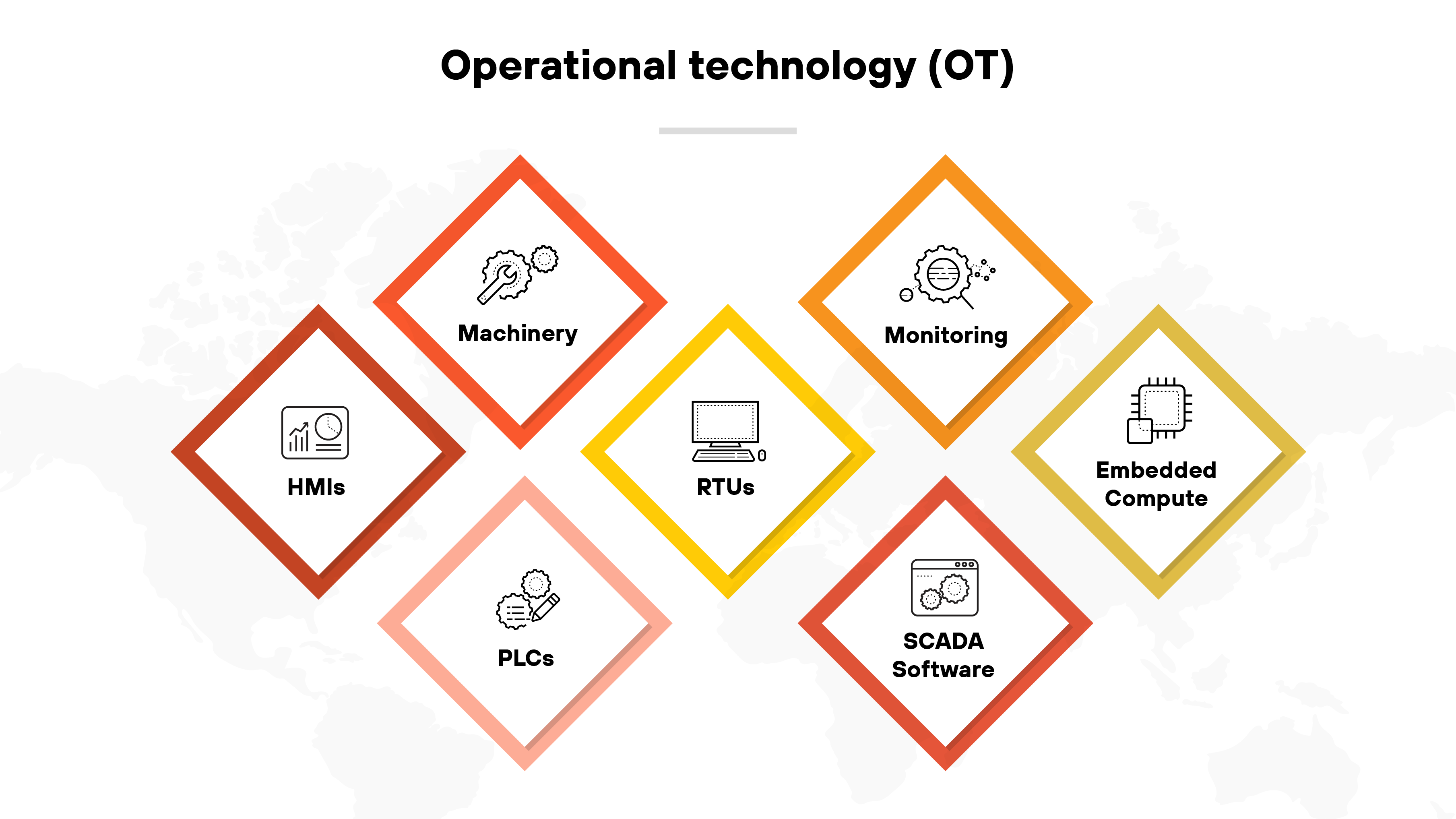
Operational technology refers to hardware and software systems that monitor and control physical devices and processes in industries like manufacturing and power generation, for instance.
OT systems help manage critical infrastructure such as power plants and transportation systems. Securing OT is crucial because vulnerabilities can lead to disruptions in essential services, including safety hazards and potential damage to physical assets.
Industrial Internet of Things (IIoT)
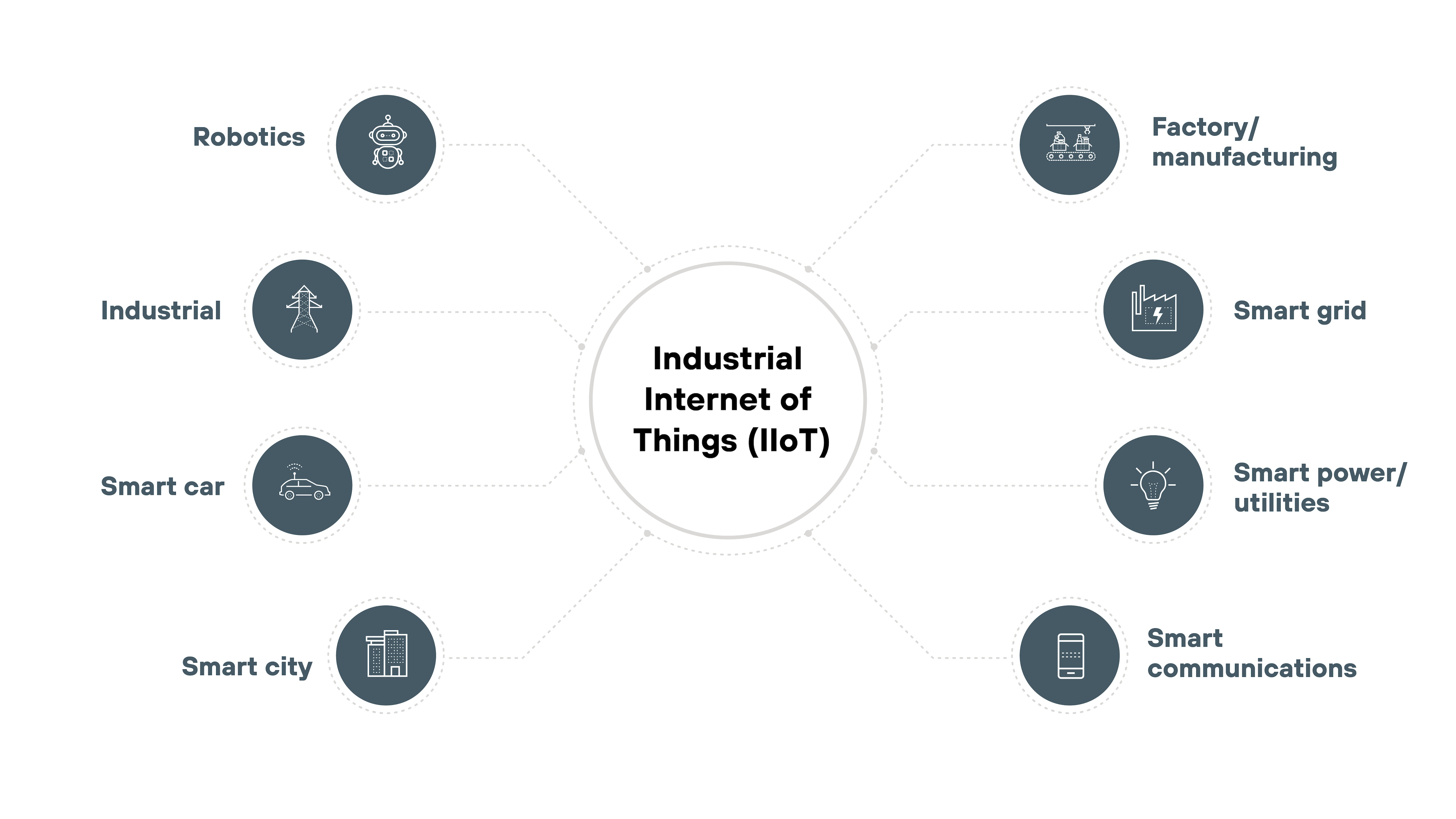
IIoT involves a network of interconnected devices designed to enhance industrial operations through real-time data collection and automation.
These systems improve productivity and safety in sectors like manufacturing and logistics. However: The vast number of connected devices increases the attack surface, making cybersecurity essential to protect sensitive industrial data and prevent unauthorized access to control systems.
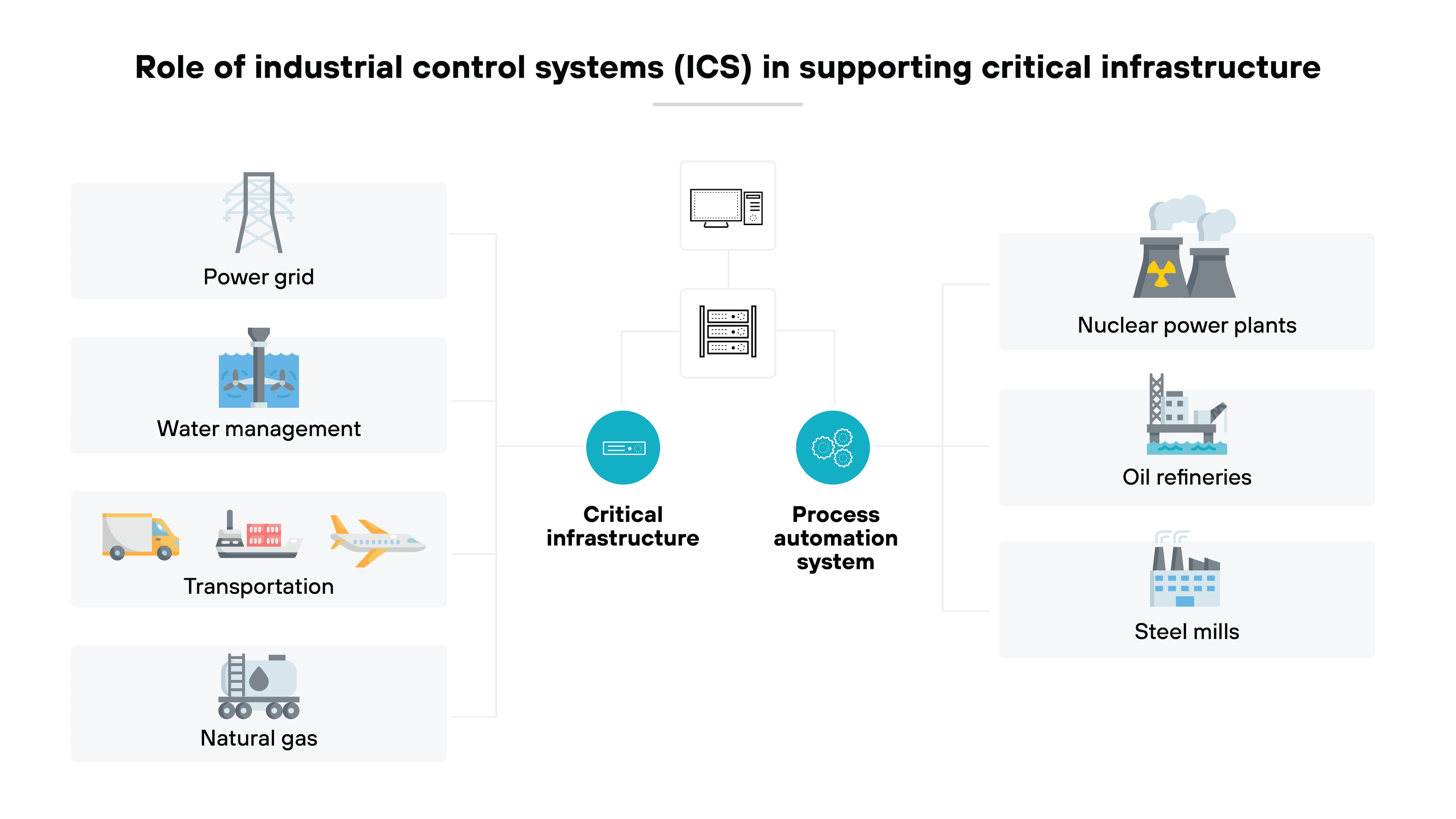
Industrial control systems (ICS)
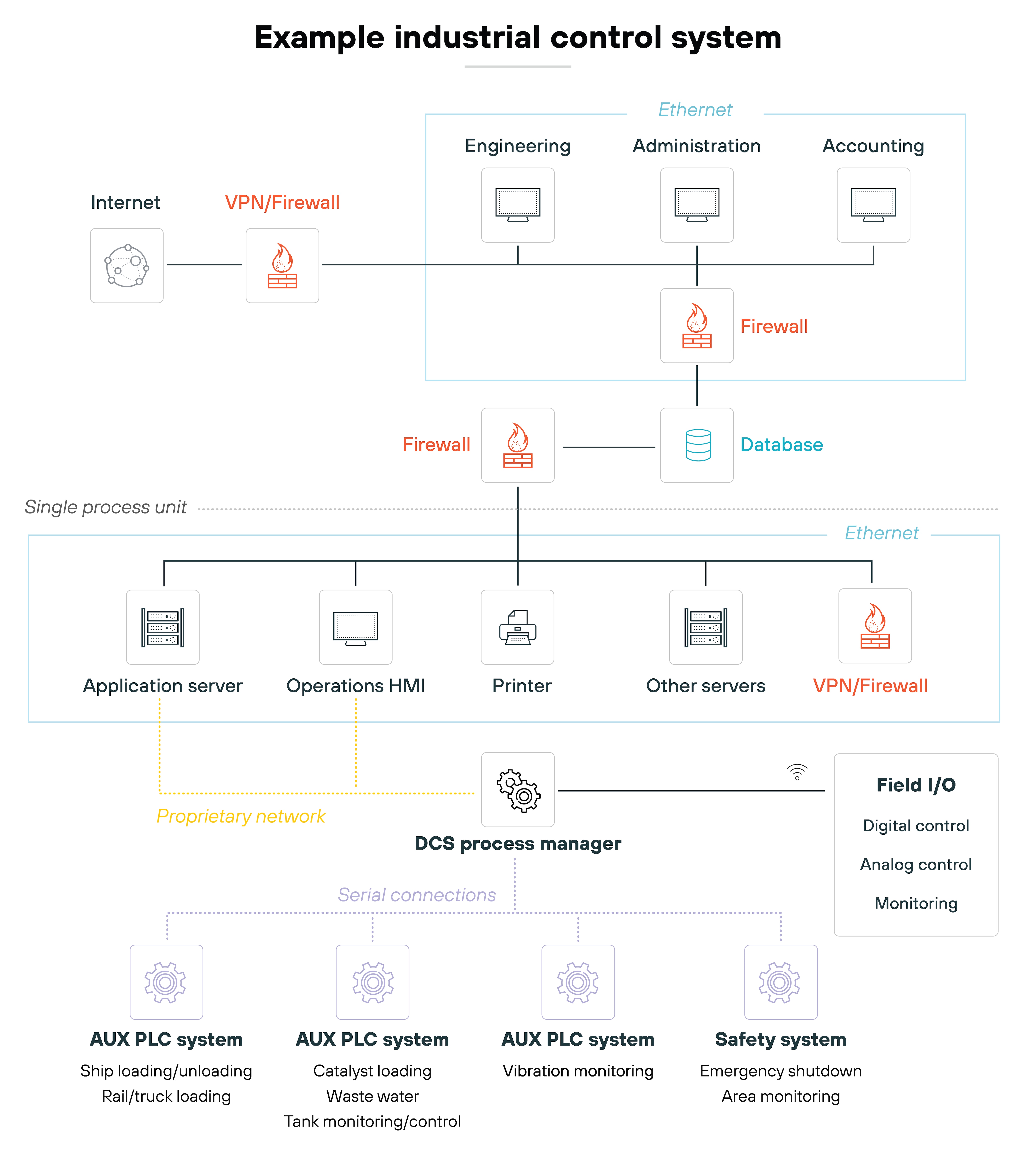
ICSs are used to monitor and control industrial processes in sectors like energy and manufacturing.
These systems are crucial for the safe and efficient operation of industrial facilities. The security of ICS is especially vital because cyberattacks can result in physical damage, operational disruption, or even endanger human lives.
Smart buildings
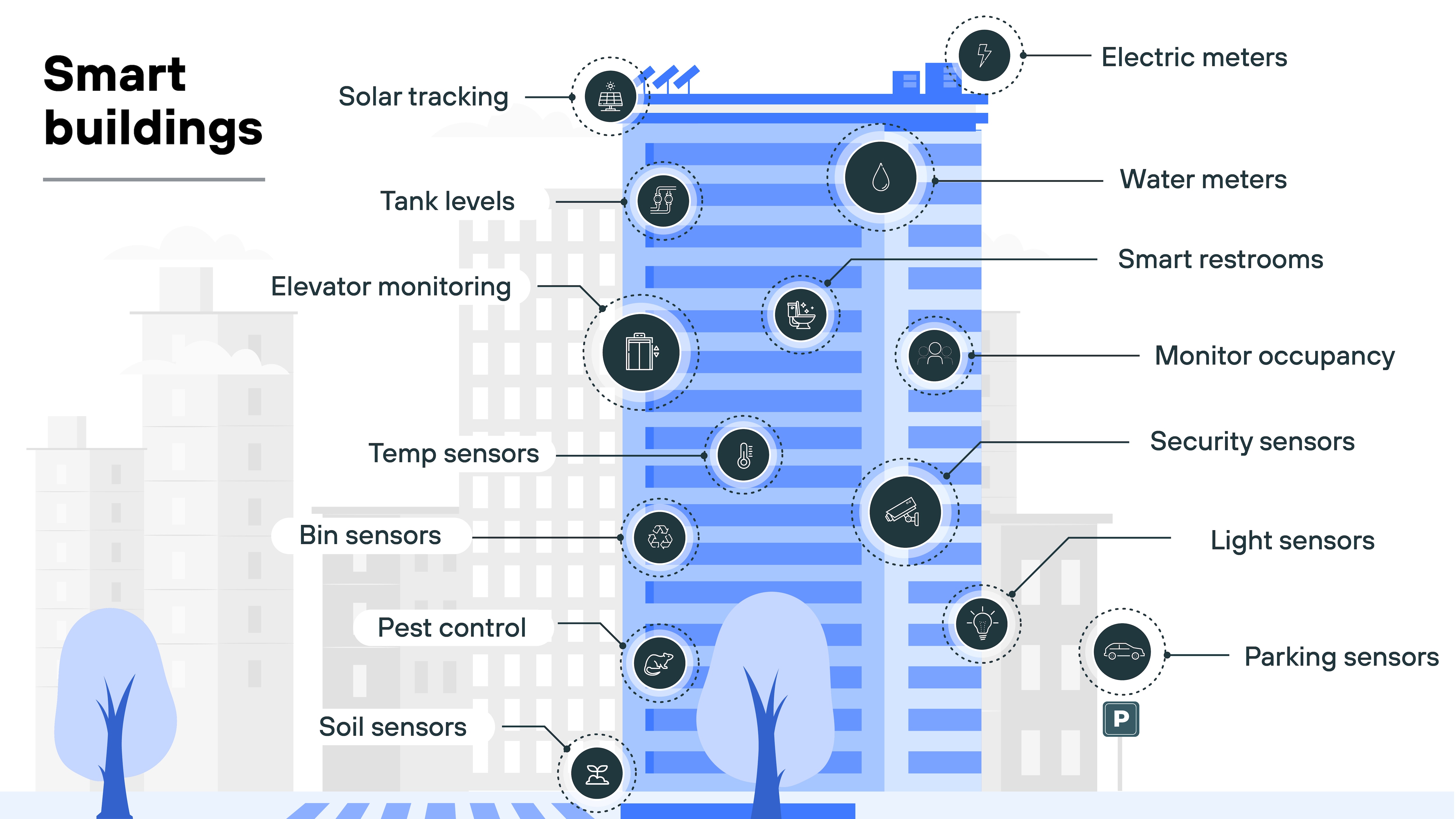
Smart buildings integrate various sensors and control systems to optimize energy usage, security, and comfort.
By monitoring and controlling lighting, HVAC, and other systems, these buildings offer sustainable living environments. Securing smart buildings focuses on making sure that the systems remain functional and that unauthorized users can’t interfere with critical building functions.
Building management systems (BMS)

BMSs are systems used to monitor and control various building operations, including HVAC, lighting, and security.
They improve energy efficiency and comfort within a building. Since BMSs connect to physical infrastructure, they’re vulnerable to cyber threats that could compromise both building operations and the safety of its occupants.
Smart grids
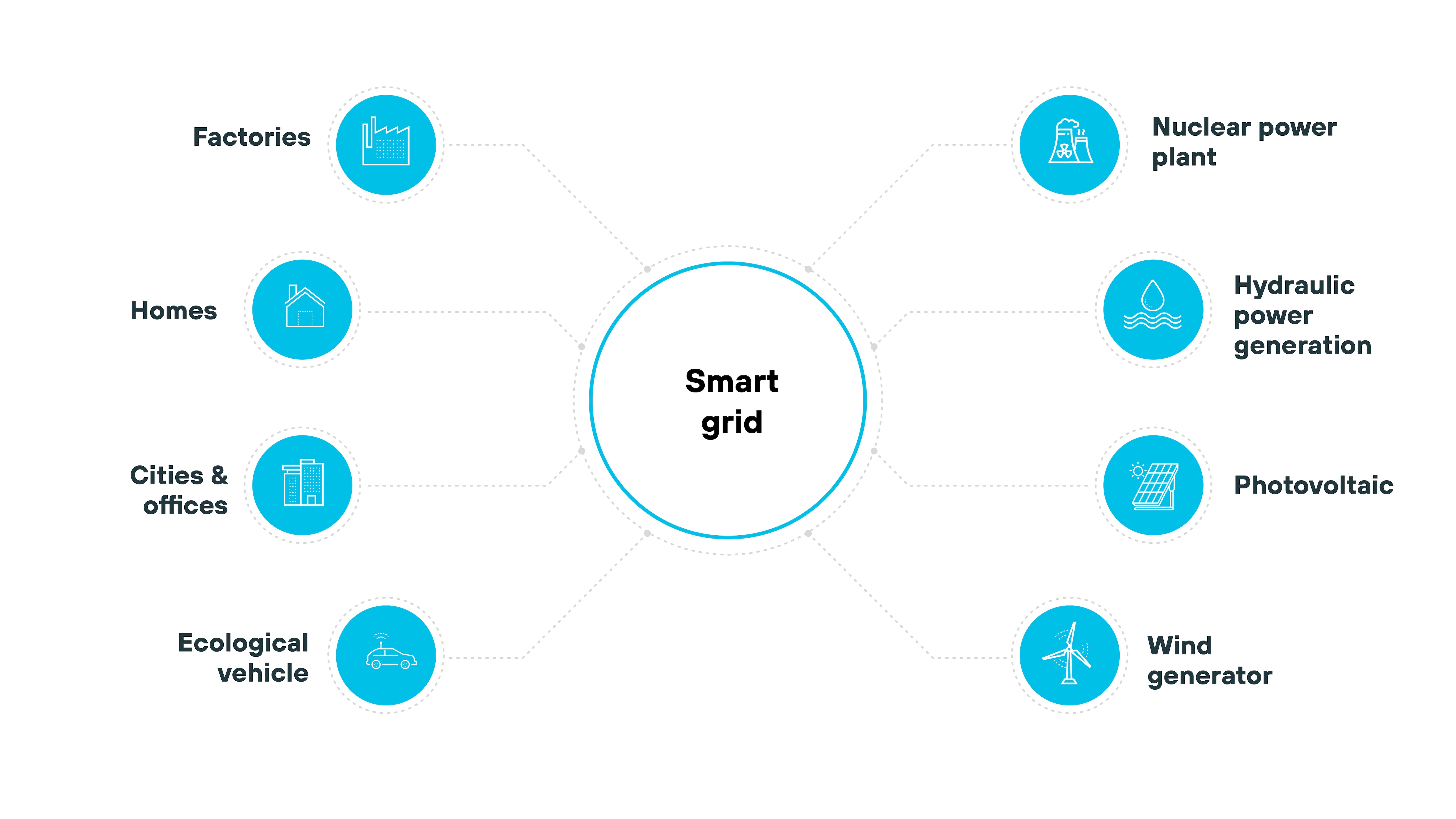
Smart grids use information technology to enhance electrical power distribution management.
They offer real-time monitoring and automated decision-making. Which makes energy distribution more efficient and reliable. Protecting smart grids is critical—cyberattacks can lead to widespread power outages or manipulation of energy flow, affecting entire regions.
Robotics
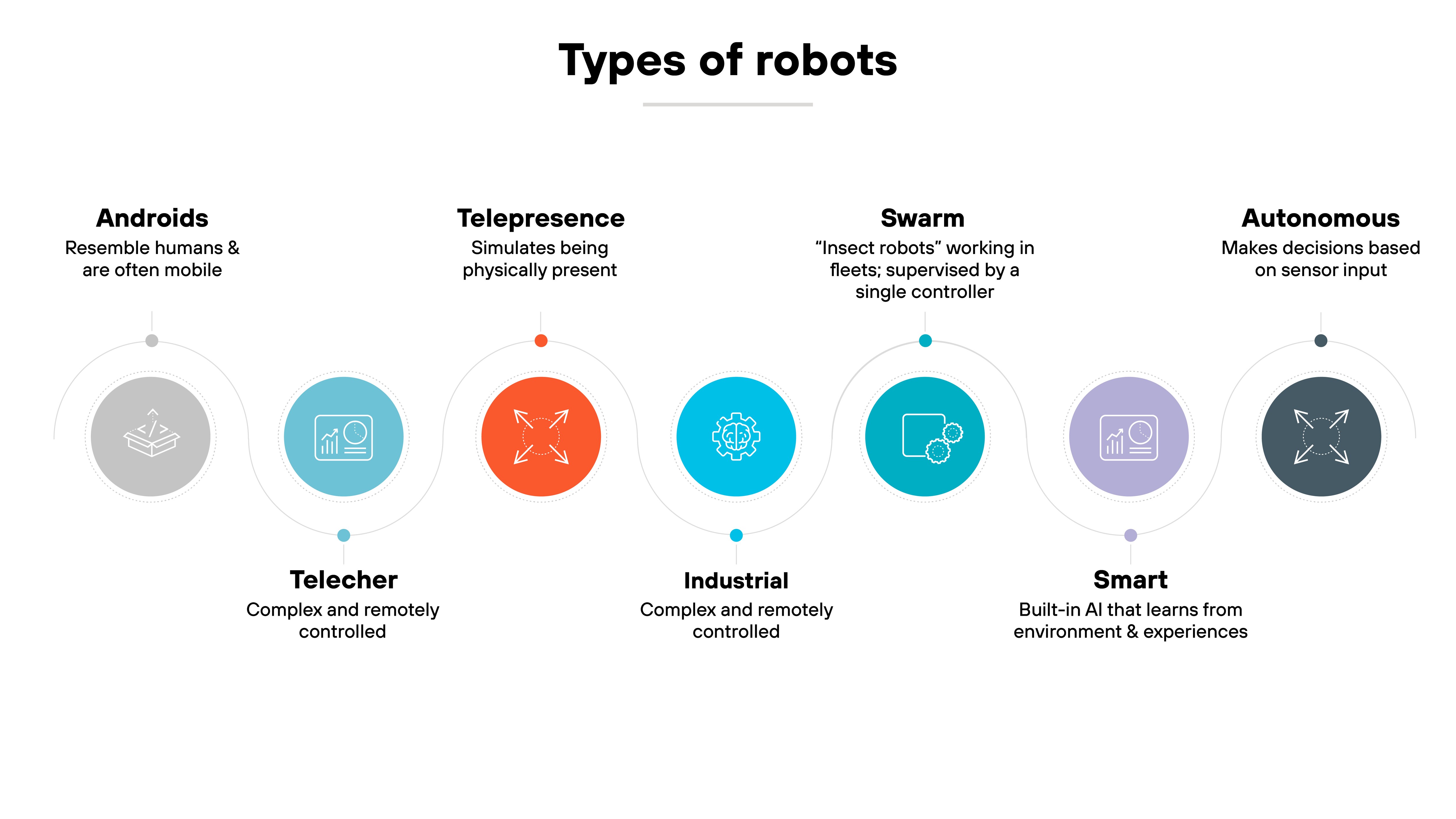
Robotics involves using automated machines to perform tasks, often in manufacturing and healthcare.
These CPSs provide precision, improve safety, and increase productivity. Securing robots is essential to prevent manipulation because it can compromise operations or cause safety risks to workers or patients.
Smart transportation systems
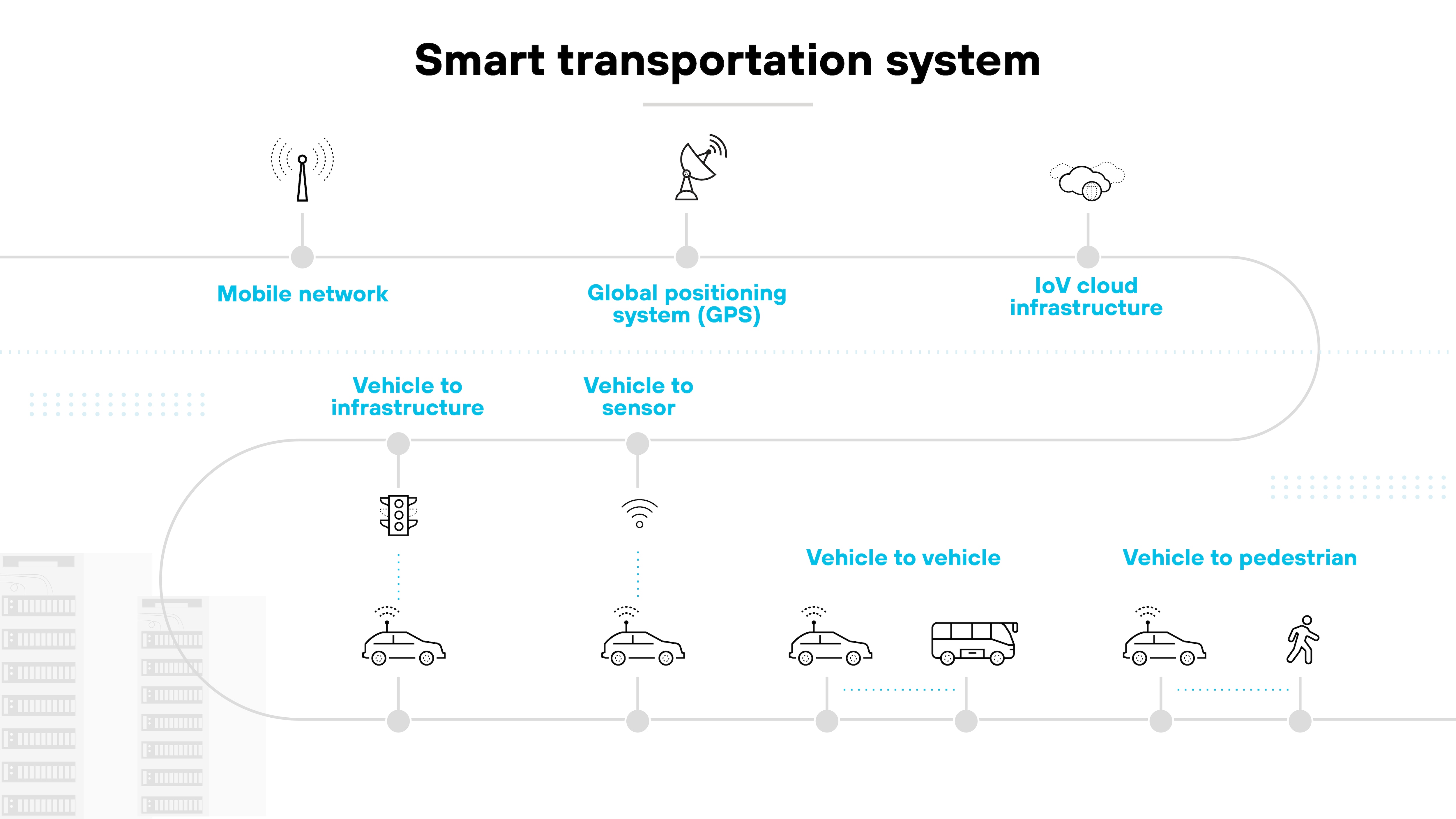
Smart transportation systems improve the efficiency and safety of transportation networks through CPS.
They include autonomous vehicles, real-time traffic monitoring, and optimized route planning. Smart transportation systems rely heavily on accurate data and secure communication. And that makes cybersecurity a top priority to prevent malicious interference with traffic flow or vehicle operations.
Medical devices
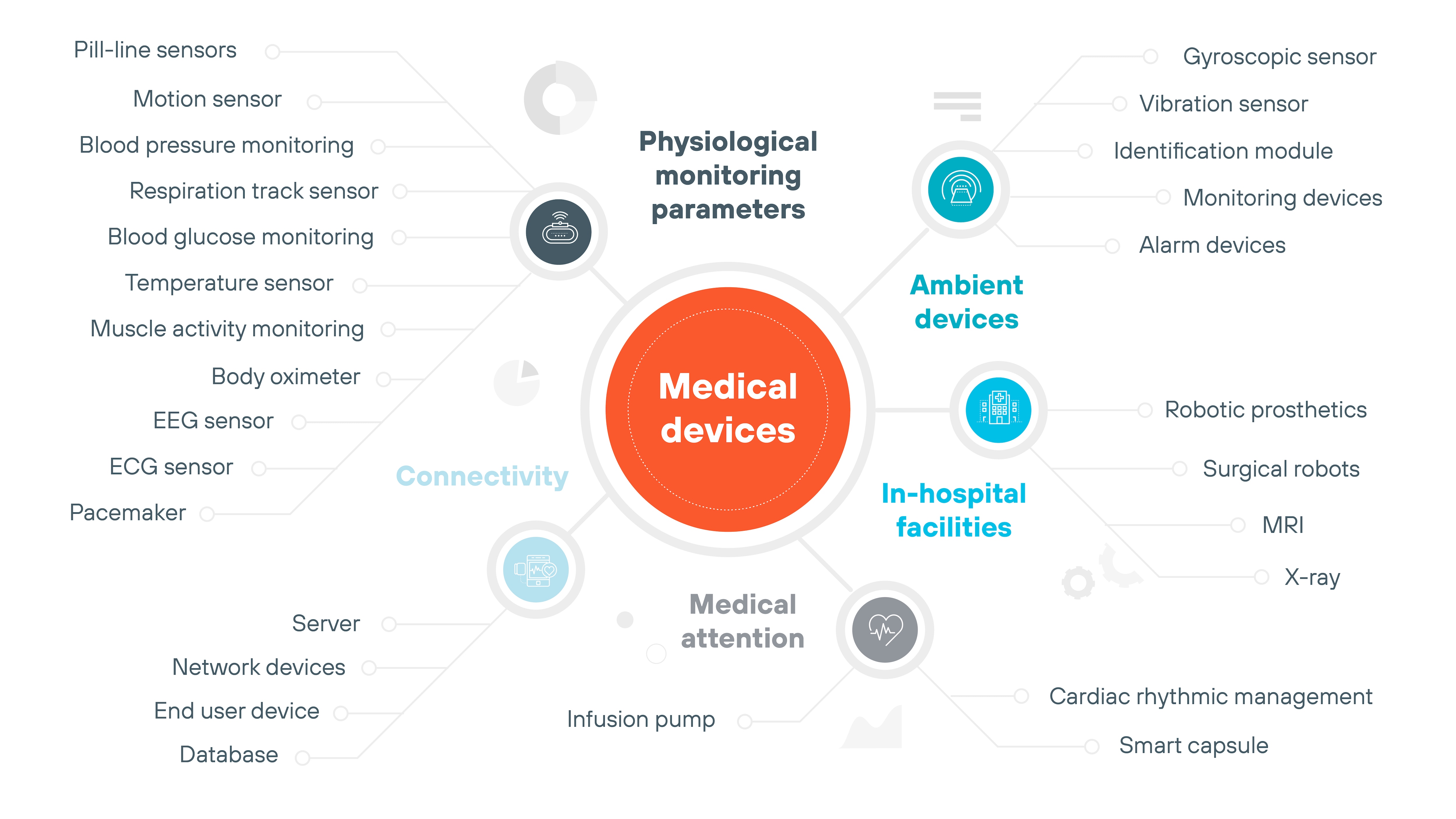
Medical devices, like pacemakers or infusion pumps, use CPSs to monitor and adjust patient health in real time.
These devices help improve patient outcomes by providing continuous monitoring and delivering care when needed.
Cybersecurity is critical in medical devices to protect patient safety and ensure devices operate as intended without interference from external threats.
Smart manufacturing
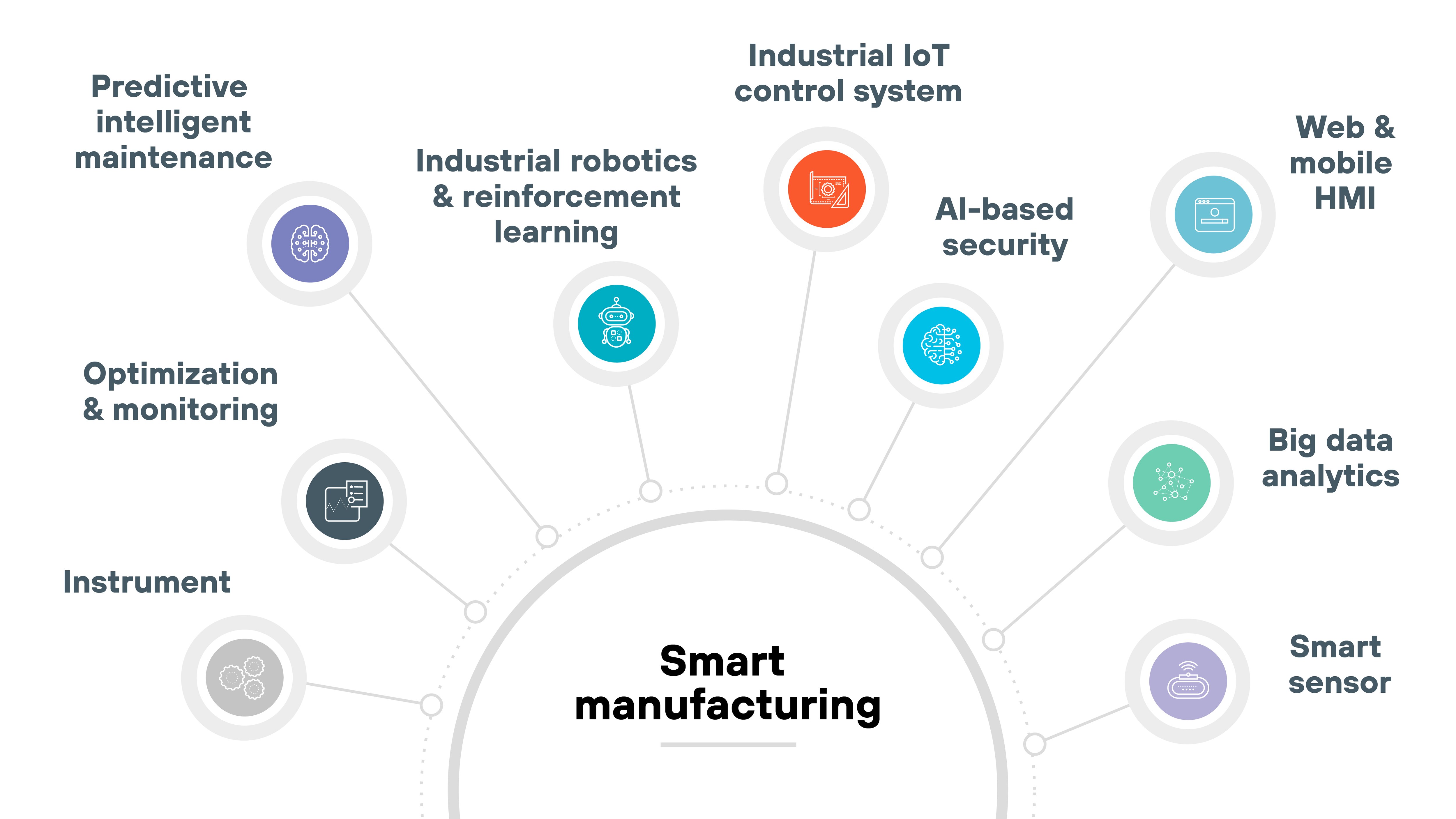
Smart manufacturing involves the use of CPSs to optimize production processes and improve efficiency.
Sensors, robots, and real-time analytics help manufacturers adapt to changing conditions and prevent failures. Securing smart manufacturing systems is about making sure that sensitive production data remains private and that the manufacturing process remains uninterrupted by cyber threats.
What is the difference between a cyber-physical system and an Internet of Things (IoT) device?
The difference between a cyber-physical system and an Internet of Things (IoT) device is that a CPS integrates computation, control, and physical processes to interact with and control real-world environments, while IoT devices focus on collecting and transmitting data with limited control over physical systems.
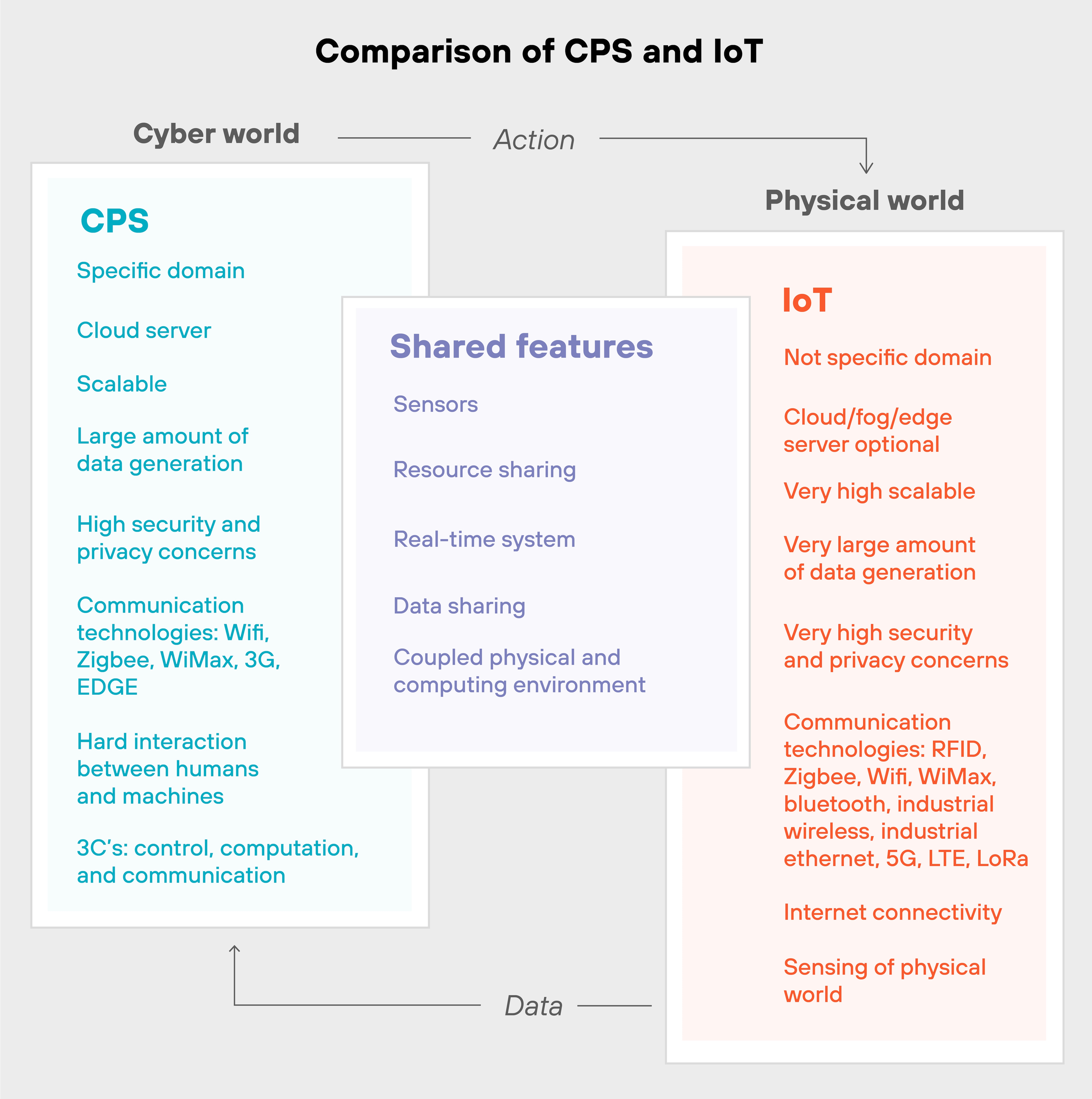
IoT devices connect everyday objects to the internet for tasks like sensing or transmitting data.
For example: A smart thermostat adjusts room temperature based on occupancy, without much interaction beyond the data exchange.
These devices are primarily concerned with connectivity and monitoring.
CPS, on the other hand, is more complex and combines real-time data processing with physical actions.
For instance: A self-driving car makes decisions by analyzing data from sensors and interacting with its environment to navigate.
Basically, CPS systems have greater control over physical processes. They use feedback mechanisms to adapt and make decisions.
The key distinctions are complexity and control: IoT devices handle simpler tasks with limited control, whereas CPS provides deeper integration between computational and physical systems, making decisions and acting on them in real time.
Why is cyber-physical system security important?
Cyber-physical system security is important because CPSs integrate physical processes with computing, creating an expanded attack surface that increases the risk of cyberattacks.
Since CPSs often control critical infrastructure, breaches can lead to severe disruptions, physical damage, or even harm to individuals.
With the growing number of interconnected devices, the risks associated with CPSs continue to rise.
Attacks like ransomware can shut down essential operations, while more sophisticated methods, such as GPS spoofing, can compromise navigation and control.
Ensuring the security of cyber-physical systems is essential to (1) preventing those types of incidents and (2) protecting the physical world and the data that powers CPSs.
What are the common cyber-physical system security challenges?
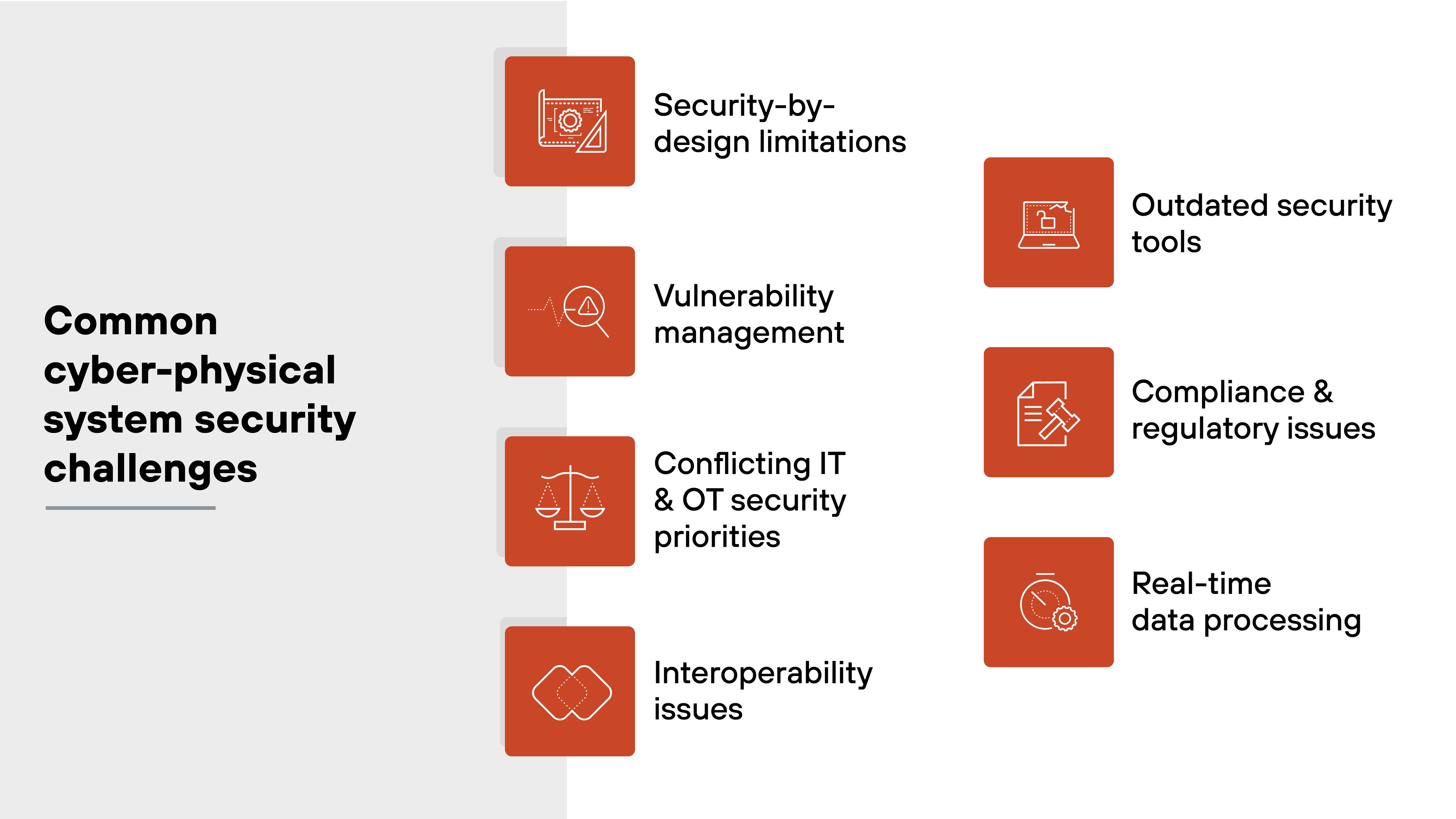
CPS safety and security comes with a unique set of challenges because of the complexity, interconnectedness, and the integration of physical and computational elements.
Cyber-physical systems demand specialized security measures that address both the cyber and physical aspects, which traditional IT security methods often fail to cover.
Common cyber-physical system security challenges include:
- Security-by-design limitations
- Vulnerability management
- Conflicting IT and OT security priorities
- Interoperability issues
- Outdated security tools
- Scalability challenges
- Compliance and regulatory issues
- Real-time data processing
Security-by-design limitations
One of the major challenges in CPS security is the lack of built-in security in many devices.
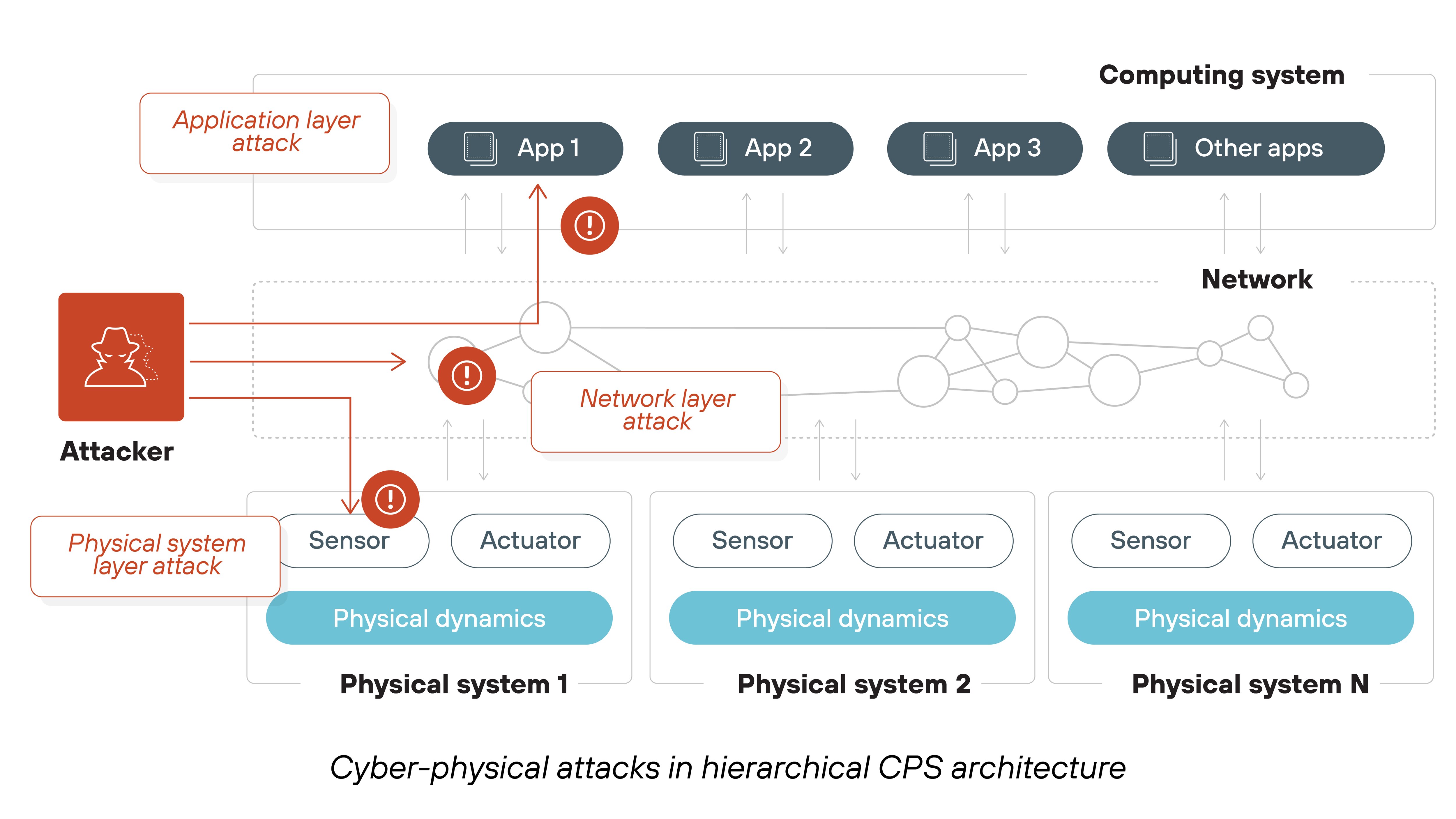
Most cyber-physical systems were initially designed without considering cybersecurity, often operating in isolated environments.
But as CPSs become more interconnected, their security vulnerabilities grow. And that exposes them to cyberattacks that can cause physical harm.
Which is why addressing these issues early in the design phase is crucial to ensure long-term security.
Vulnerability management
Another big CPSSEC challenge is vulnerability management.
CPS environments usually include a mix of new and legacy devices, each using different protocols. Identifying which devices need patching can be tough. Plus, testing patches on individual devices requires a lot of time and resources.
Not to mention: The shortage of specialized security skills further complicates the process of effectively managing vulnerabilities across diverse systems.
Conflicting IT and OT security priorities
The different priorities between IT and operational technology (OT) security teams present a major hurdle.
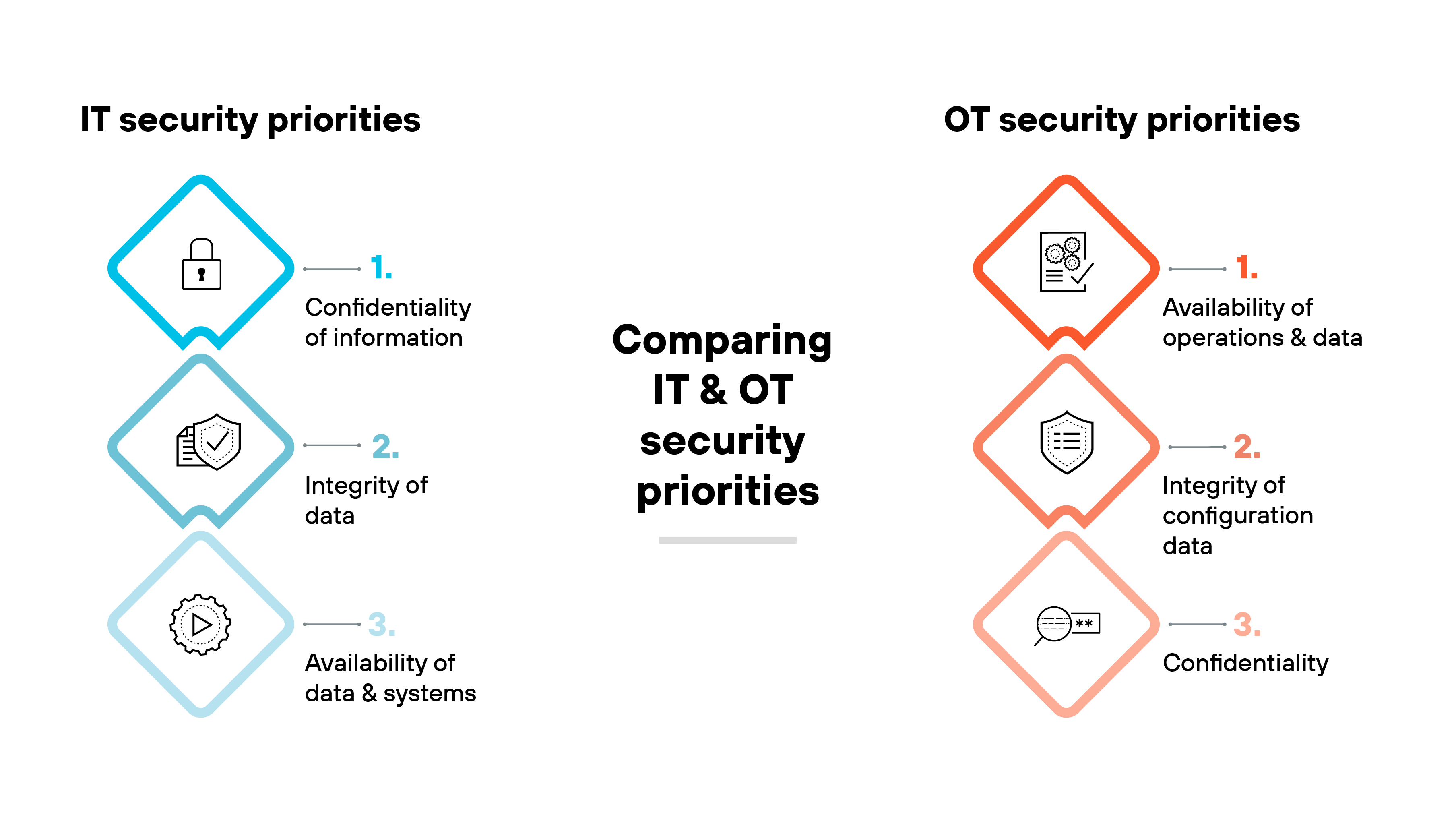
IT teams generally prioritize data confidentiality, while OT teams emphasize data availability. These differing focuses can lead to fragmented security strategies, leaving gaps that adversaries could exploit.
Organizations need a unified approach to address these challenges comprehensively.
Interoperability issues
CPSs often involve various devices and systems that have to work together.
The problem is this: These systems often use incompatible protocols, which complicates integration.
Achieving interoperability while maintaining security becomes more difficult as the number of connected devices increases. Organizations have to balance the benefits of interconnected systems with the security risks they bring.
Outdated security tools
Traditional IT security tools are often unsuitable for CPS environments.
Since they’re designed for IT systems, they don’t account for the unique needs of CPSs—like fragility and proprietary protocols, for instance.
Using IT-centric security solutions in CPS environments could impair sensitive devices, leaving systems vulnerable. Specialized tools tailored to the needs of CPS are necessary for effective protection.
Compliance and regulatory issues
The evolving regulatory landscape for cyber-physical systems adds another layer of complexity.
Organizations have to keep current with changing data protection laws, industry-specific safety standards, and other compliance requirements. Staying compliant and secure requires continuous effort and adjustment.
Real-time data processing
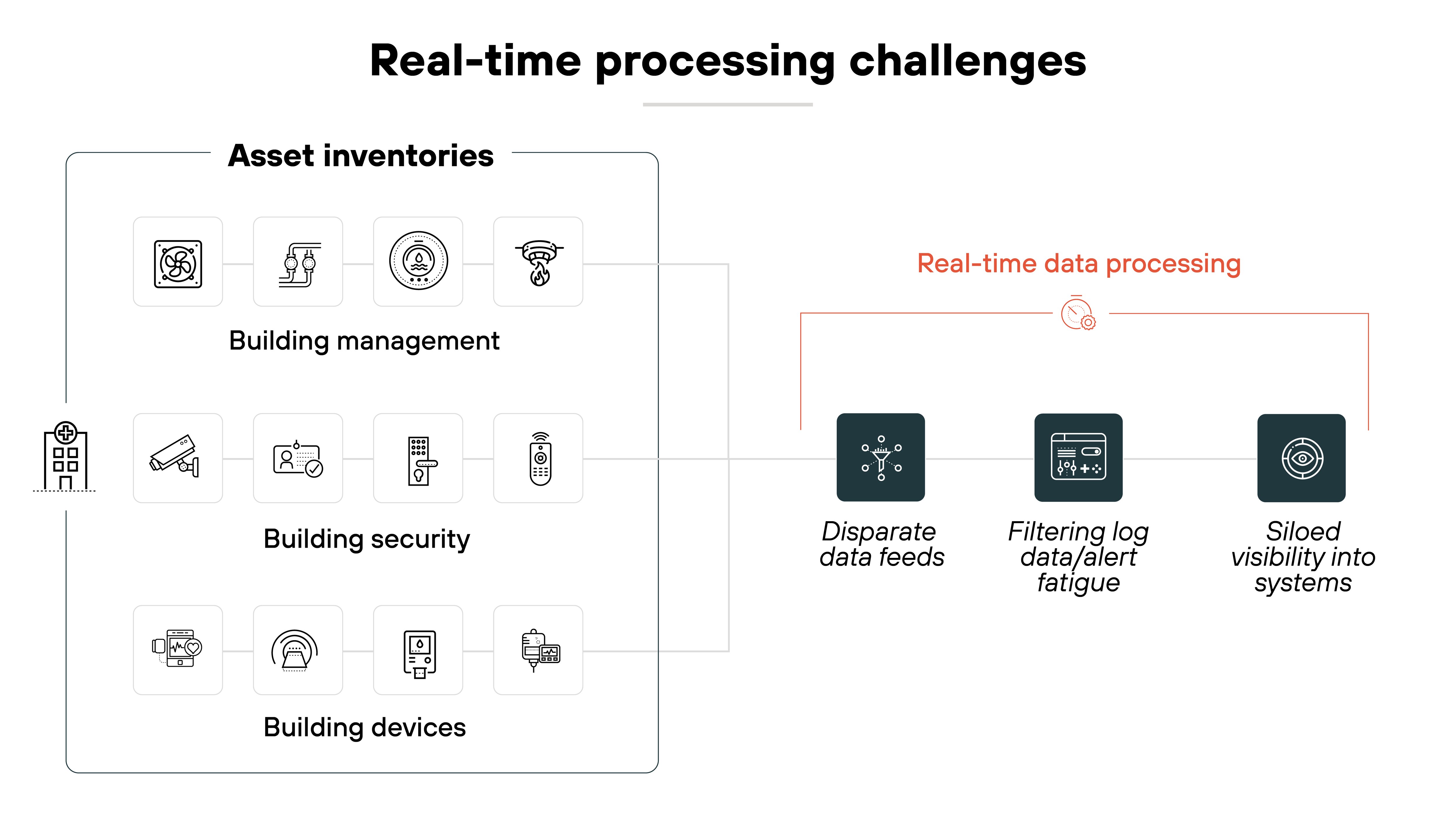
Again, cyber-physical systems require continuous real-time data processing to work properly.
Processing delays can result in inaccurate insights and poor decision-making, affecting both the digital and physical components of the system.
Which is why real-time visibility into asset inventories and threats is crucial for effective security. Unfortunately, many CPSs lack the tools necessary for full visibility and actionable insights.
What to look for in a CPS protection platform
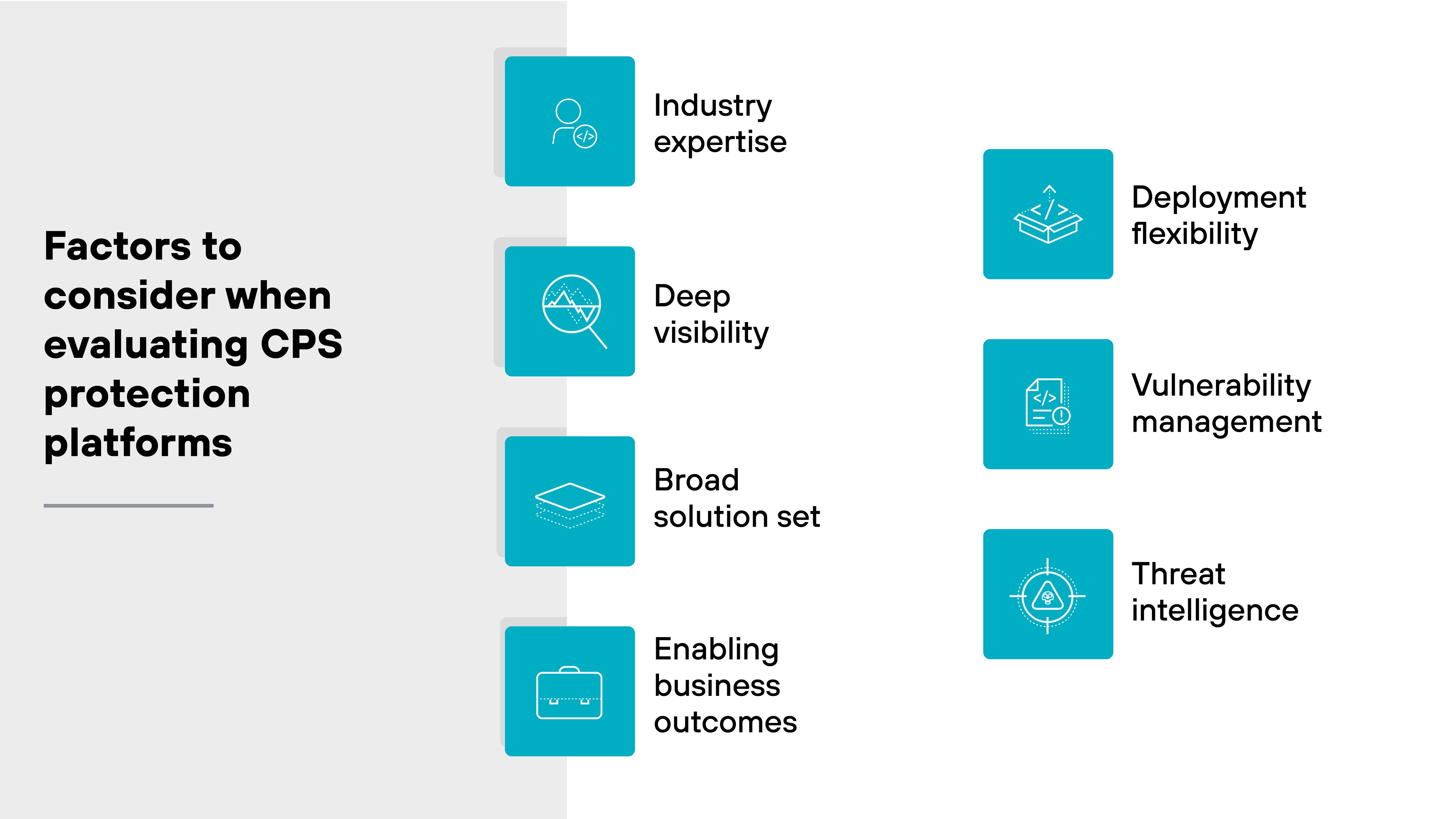
When selecting a platform to secure your cyber-physical systems (CPS), it’s essential to consider several key factors that ensure comprehensive protection.
A CPS protection platform must address the unique complexities of CPS and offer solutions tailored to the diverse devices and systems they encompass.
Here are the factors to consider in the search for a CPS protection platform:
- Industry expertise
- Deep visibility
- Broad solution set
- Enabling business outcomes
- Deployment flexibility
- Vulnerability management
- Threat intelligence
Industry expertise
Industry expertise is a crucial aspect to consider when choosing a CPS protection platform.
A CPS platform should have a proven track record in CPS security. It should also be able to demonstrate its capability to handle the specific challenges of protecting interconnected systems.
Look for platforms that actively work with manufacturers to identify vulnerabilities and provide customers with robust defense mechanisms.
Deep visibility
Achieving deep visibility within CPS devices is vital for understanding potential threats.
Choose a platform that employs both active and passive discovery methods.
This includes techniques capable of accessing devices using unique protocols, proprietary systems, or air-gapped networks that may not be reachable through passive-only methods.
The ability to uncover every asset connected to the network is essential for managing security effectively.
Broad solution set
A platform with a broad solution set can address a wide range of CPS security needs.
When evaluating options, ensure the platform supports a variety of CPS across different deployment needs, network architectures, and device types.
A vendor with a versatile portfolio should be able to meet your unique environmental and operational requirements—and ensure that all components of your systems are covered.
Enabling business outcomes
It’s important to select a CPS protection platform that’s focused on better business outcomes.
A comprehensive solution should allow you to manage, monitor, and control all aspects of your CPS security from one interface.
The right platform will streamline risk management, provide actionable insights, and enable faster responses to threats.
Deployment flexibility
Flexibility in deployment is another key feature to look for in a CPS protection platform.
The ability to deploy the platform on-premises, in the cloud, or in hybrid environments allows you to choose the best option for your organization.
Plus, the flexibility can help reduce costs associated with hardware and infrastructure while meeting the specific deployment needs of your network.
Vulnerability management
Effective vulnerability management is key to CPS security.
A good platform should correlate asset discovery with databases of known vulnerabilities, allowing for quick identification of risks.
The ability to prioritize vulnerabilities based on asset criticality and the likelihood of exploitation, along with detailed remediation guidance, will allow you to act swiftly to minimize threats.
Threat intelligence management
The platform you choose should also offer robust threat intelligence management. This will help you stay ahead of emerging threats and ensure your CPS remains secure in the face of evolving cyber risks.
This includes integrating indicators of compromise (IoCs), tactics, techniques, and procedures (TTPs) from threat intelligence feeds, as well as signature-based detections.
Advanced solutions can usually provide in-depth telemetry for analytics, perform attack simulations, and support machine-readable threat intelligence formats.