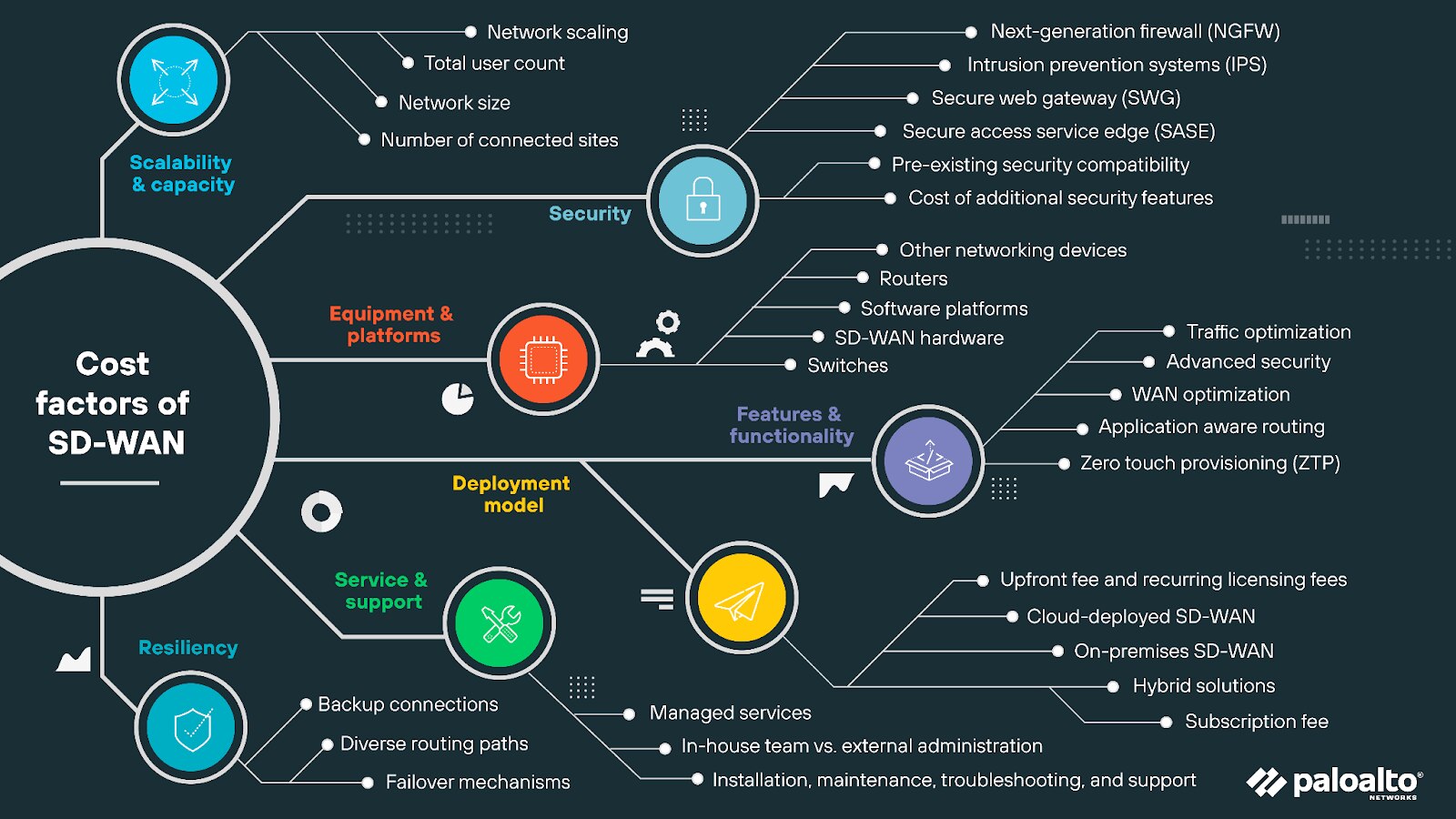
Top 7 SD-WAN Challenges: SD-WAN Risks, Issues, & Solutions
The top SD-WAN challenges include:
- Finding the right vendor
- Determining underlay provisioning needs
- Navigating cloud connectivity options
- Quantifying cost reduction accurately
- Troubleshooting issues
- Addressing security and visibility limitations
- Choosing the right management model
While SD-WAN can potentially come with obstacles as all technologies do, organizations shouldn't be dissuaded from investing in it. With the right plan, knowledge, and resources, challenges associated with deploying SD-WAN can be overcome.
Finding the right vendor
One of the main hurdles in implementing SD-WAN is simply finding the right vendor.
The market is filled with options, each offering a suite of features that promise to revolutionize your network. But here’s the catch: not all vendors are created equal.
Because it’s not just about choosing a great product. It’s about finding a partner who understands your organization’s specific needs and can integrate seamlessly with existing infrastructure.
Here are some of the factors you’ll need to consider:
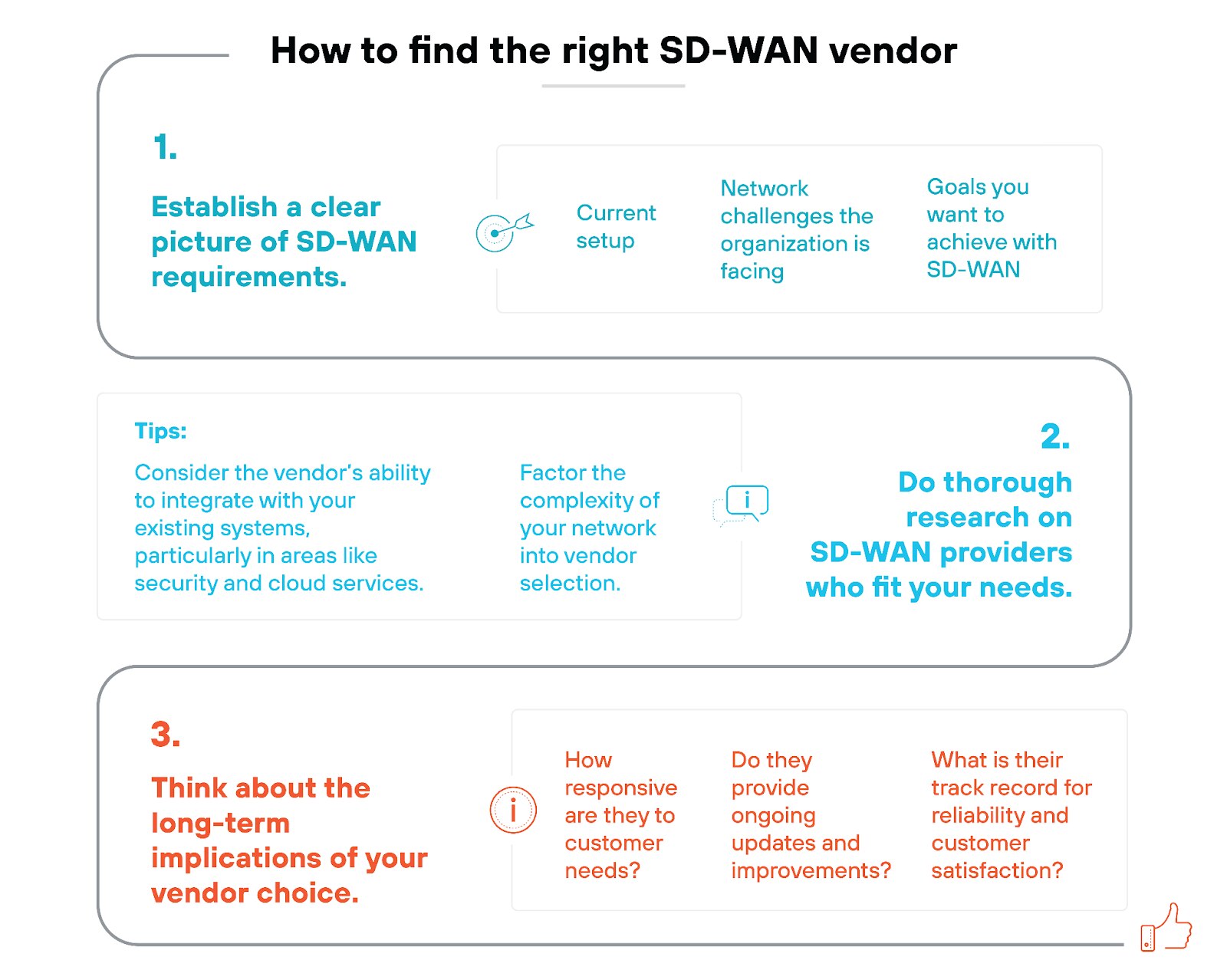
The first hurdle in the selection process is probably cutting through the marketing noise. Most vendor solutions come with impressive claims. Which makes it difficult to distinguish which product truly meets your business needs.
To address this, network teams should start by taking a close look at:
- The current setup
- Network challenges the organization is facing
- Goals you want to achieve with SD-WAN
Once you’ve got a clear picture of requirements, you can begin to evaluate vendors.
Next, conduct thorough research into the top SD-WAN providers.
Dive deep into how each vendor’s offerings align with your needs. Look at case studies, customer reviews, and independent evaluations to get a sense of how these solutions perform in real-world scenarios.
Tip: Consider the vendor’s ability to integrate with your existing systems, particularly in areas like security and cloud services.
Another critical factor is understanding the complexity of your network and how it might impact vendor selection.
For example: If your network includes multiple third-party security solutions, you’ll want to find a vendor that can integrate smoothly with those systems. On the other hand, if you’re looking for a simpler, more streamlined approach, you might opt for a vendor offering a more comprehensive, all-in-one solution.
Don’t forget to think about the long-term implications of your vendor choice, too.
SD-WAN is not a one-time purchase. It’s a long-term partnership. So be sure to evaluate the product and the support and services the vendor offers.
- How responsive are they to customer needs?
- Do they provide ongoing updates and improvements?
- What is their track record for reliability and customer satisfaction?
Determining underlay provisioning needs
At its core, underlay provisioning refers to the selection and configuration of the underlying network infrastructure that SD-WAN uses to connect various locations. This is where the decision between private WAN technologies, like MPLS, and public internet options comes into play.
Given the impacts of digital transformation, including most businesses adopting a cloud-first approach, this decision has become even more complex—and even more important.
But here’s the problem.
A lot of current SD-WAN solutions are built for a time when most applications were hosted in data centers. Back then, routing traffic through data centers for security inspections and using network SLAs for decisions made sense.
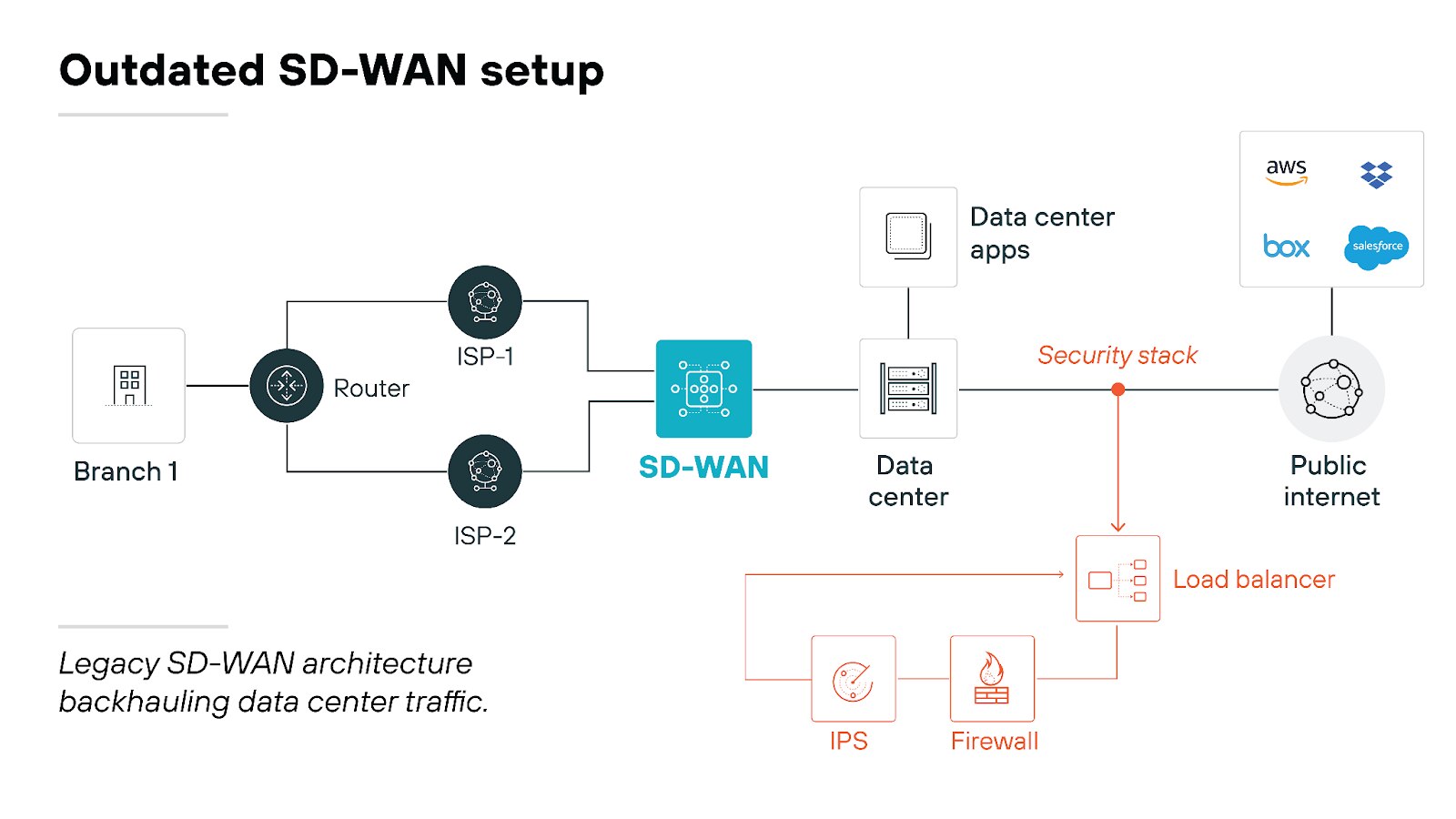
Times have changed, though. Cloud migration and SaaS adoption have skyrocketed.
Now, branches need uninterrupted access to applications from any source. They also need better traffic intelligence to keep employees productive. Unfortunately, the old SD-WAN architecture just can’t keep up.
The outdated SD-WAN setup tends to lead to issues like latency and downtime. These problems frustrate employees and flood IT teams with support tickets. Networking teams struggle to deliver the performance branches need. Meanwhile, security teams are left worrying about the surge in internet-bound traffic.
Modern applications obviously need acceleration. But plenty of current SD-WAN solutions still rely on traditional methods like network SLAs and outdated remediation techniques. And that hampers application performance and causes slow-downs or even unavailability. Which means employee productivity suffers.
Choosing the right underlay directly impacts the performance, reliability, and security of your SD-WAN deployment.
For example: Large enterprises with global operations might benefit from using a single IP backbone. This approach keeps all traffic within one autonomous system, which can help maintain consistent latency and reduce jitter. However, this isn't a one-size-fits-all solution. National networks, which may not be as concerned about round-trip delays, might find a multi-ISP strategy more suitable. This allows them to select providers based on specific geographic needs, optimizing cost and coverage.
On top of these considerations, the traditional strengths of MPLS—such as its focused troubleshooting capabilities and end-to-end management—add another layer of complexity.
An ISP doesn't typically offer the same level of dedicated service. Which means that IT teams need to carefully evaluate how well a potential underlay provider can manage and troubleshoot network connectivity issues.
Note: This is particularly important if you're considering a DIY approach to SD-WAN management, where the burden of maintaining network health falls squarely on your team.
So, how do you address this challenge?
- Start by thoroughly assessing your organization’s specific needs. Consider factors like the scale of operations, the geographic distribution of sites, and SD-WAN performance requirements.
- Then, evaluate potential underlay providers based on how well they can meet these needs. Look into their service-level agreements (SLAs) to ensure they offer adequate support for troubleshooting and monitoring.
- It’s also wise to consider a mix of strategies.
For example: You might use a single IP backbone for global operations but supplement it with regional ISPs where it makes sense. This hybrid approach can offer the best of both worlds—ensuring stability and performance while optimizing costs.
Navigating cloud connectivity options
Everything is in the cloud now, and it’s led to a host of cloud connectivity challenges for organizations:
- Legacy SD-WAN architecture backhauls traffic to the data center, which is expensive and impacts both user experience and productivity.
- Manual operations to deliver cloud connectivity require significant expertise and operational complexity.
- As applications have moved to the cloud, so does the need for security. To ensure security, cloud applications need to be inspected where they’re running—something that can’t be done with traditional security tools.
- Also, it isn’t just communication applications that are moving to the cloud. Now, enterprise applications live in the cloud, making user experience and connectivity more critical.
As businesses increasingly move their operations to the cloud, ensuring that your SD-WAN solution can effectively connect to major cloud providers like AWS, Microsoft Azure, or Google Cloud Platform is essential.
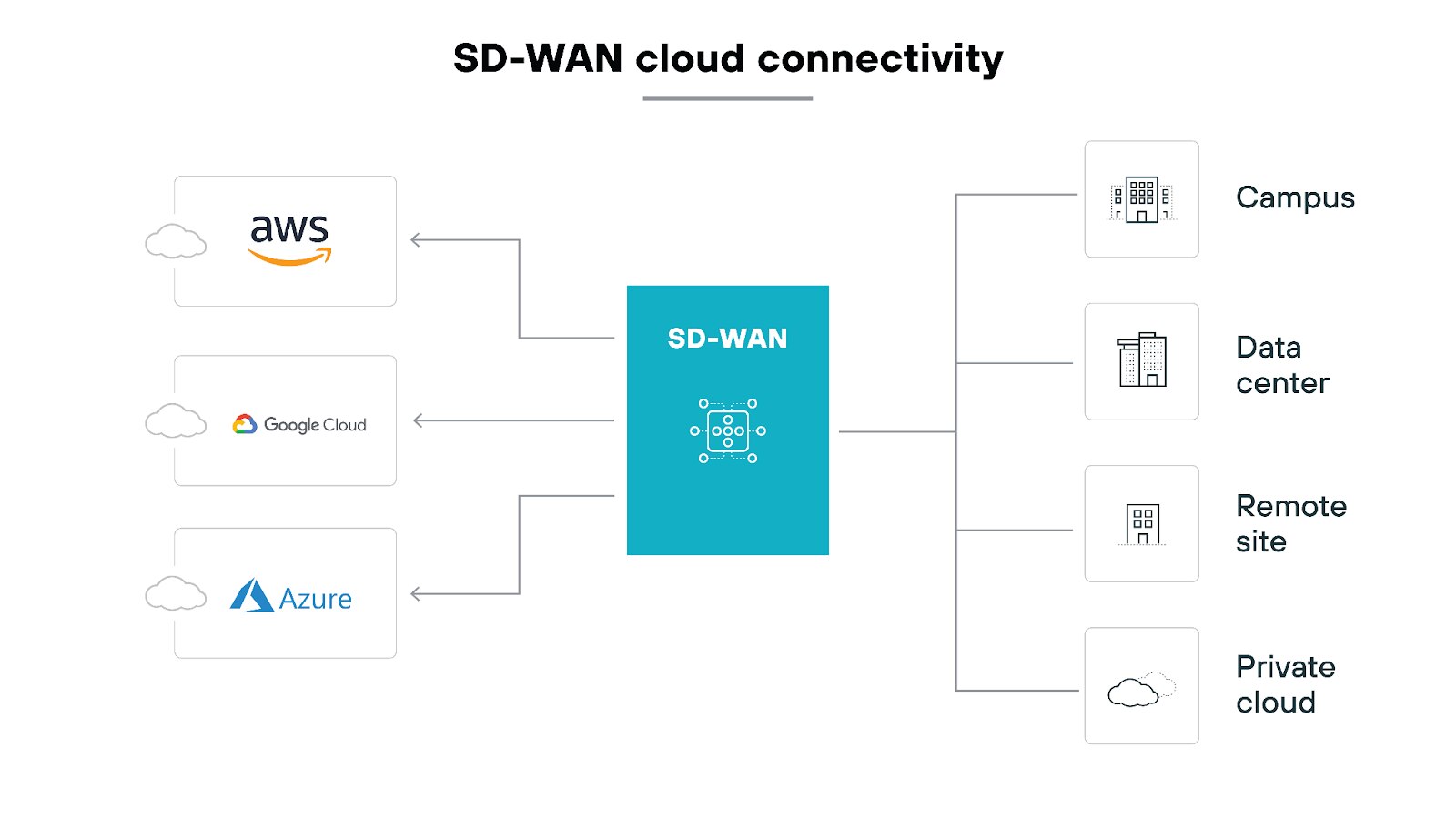
The challenge lies in understanding the different connectivity options provided by various SD-WAN vendors and determining which one aligns best with your organization's needs.
SD-WAN vendors typically offer three main types of cloud connectivity:
- Cloud native cloud connectivity
Some vendors integrate native cloud access into their architecture. This means they use the cloud’s backbone infrastructure to connect branch office sites directly.
A cloud native approach is ideal for businesses that prioritize seamless, high-performance cloud connectivity and need a robust, global backbone to support their operations.
Note: While this is a great option for businesses who need seamless, high-performance cloud connectivity, it isn't yet commonly available from all vendors.
- Vendor provided cloud connectivity
Other vendors deliver SD-WAN appliances into the cloud environment using public gateways or private backbones.
This method offers flexibility. Businesses can choose between public and private paths for their traffic.
Public gateways can be cost-effective, but they may introduce variability in performance. Private backbones, on the other hand, offer more consistent performance—but might come at a higher cost.
- Self-managed cloud connectivity
Some vendors require customers to manage cloud connectivity by deploying SD-WAN appliances within their local cloud data centers.
This option provides more control over the deployment but also requires a higher level of expertise from the IT team.
It can be beneficial for businesses that already have strong internal IT capabilities and prefer to maintain direct oversight of their cloud infrastructure.
Further reading: What Is SD-WAN Multicloud?
Quantifying cost reduction accurately
Quantifying cost reduction is a common challenge when implementing SD-WAN.
While the promise of reducing costs is often a driving factor in SD-WAN adoption, accurately measuring those savings can be more complicated than it seems.
Here’s why:
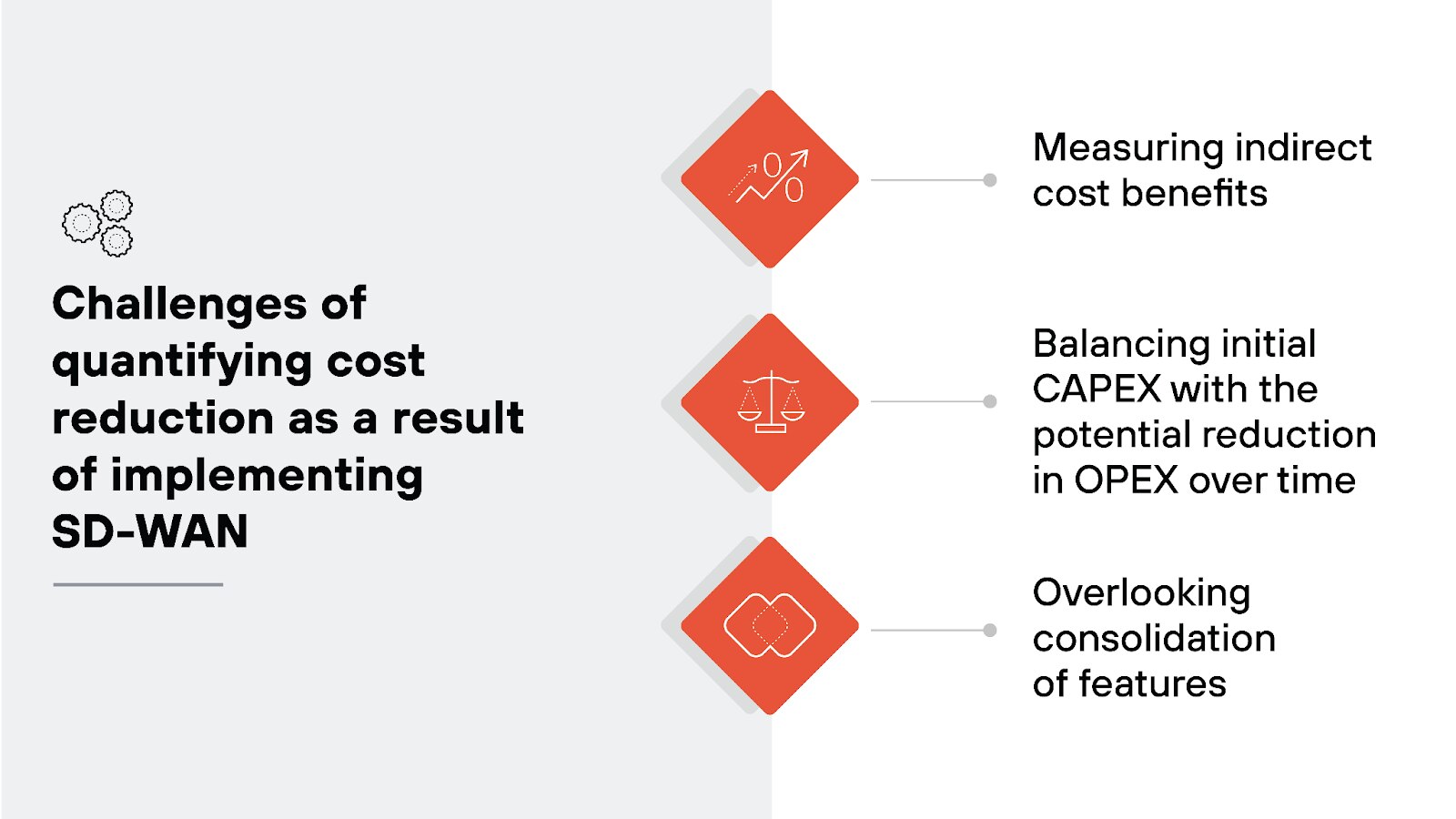
It's not just about comparing the cost of SD-WAN with traditional MPLS circuits. There are multiple factors at play that can make or break the anticipated cost benefits.
One of the first challenges is determining what "cost reduction" actually means for your organization:
- Are you looking solely at the direct costs, like replacing expensive MPLS circuits with cheaper internet connections?
- Or are you also factoring in indirect benefits like improved network performance, increased employee productivity, and reduced downtime?
These indirect benefits can be harder to quantify but are essential in understanding the true value of your SD-WAN investment.
Another challenge is the initial capital expenditure. Implementing SD-WAN typically involves upfront costs for new hardware, software, and possibly network redesign.
These costs can make it difficult to see immediate savings. Which is why it's important to consider the long-term return on investment (ROI) rather than focusing solely on short-term expenditures.
Tip: Always include the expected savings on network costs and the potential reduction in operational expenses over time in your ROI analysis.
The consolidation of features is another major factor in cost reduction, but it can be easily overlooked.
Many SD-WAN solutions offer integrated features like security and cloud access, which can eliminate the need for separate appliances and services. However, if your organization doesn’t wind up using added features as much as anticipated, or they’re not aligned with your organization's needs, anticipated savings might not materialize.
Tip: Carefully evaluate which features are essential and which are "nice to have" to avoid overspending on unnecessary functionalities.
Approach cost reduction with a comprehensive strategy:
- Start by clearly defining cost reduction goals and which metrics you’ll use to measure success. This could include direct cost savings on network infrastructure, reduced downtime, or lower operational costs due to improved efficiency.
- Next, conduct a detailed ROI analysis that accounts for both immediate and long-term costs and benefits.
- Finally, choose an SD-WAN solution that aligns with your specific needs and offers the right mix of features without overcomplicating your network.
Further reading: How Much Does SD-WAN Cost?
Troubleshooting issues
Troubleshooting SD-WAN issues can be tough because its configurations are both complex and constantly changing.
When something goes wrong—like a user experiencing lag or application slowness—it can be difficult to determine the root cause.
The problem might stem from network related issues, incorrect deployment, insufficient system resources, or other factors. The complexity makes the troubleshooting process more intricate compared to traditional WAN setups.
One of the main reasons troubleshooting is so hard is because SD-WAN architectures vary significantly among vendors.
Each vendor may have a unique way of implementing their solution. And that means that network teams need to be familiar with the specific architecture they are working with. This can create a steep learning curve. Especially if your organization uses multiple vendors, or network staff isn’t fully trained on the nuances of the chosen SD-WAN solution.
As a result, distinguishing between application performance issues and broader network problems becomes a significant challenge.
To effectively troubleshoot SD-WAN issues, it's crucial to implement a few strategic measures:
Deploy monitoring agents across all network locations
This can provide the visibility needed to identify where problems are occurring. Monitoring agents help gather the necessary data, allowing the network team to pinpoint issues more accurately.
Like this:
![Prisma SD-WAN site summary dashboard titled 'Prisma SD-WAN Site Summary Dashboard.' The main section of the dashboard features a performance graph displaying data over time, labeled with site health metrics for the past 1 hour, 3 hours, 12 hours, 24 hours, 7 days, and 30 days. To the left of the graph, numerical health scores for the site are presented, along with a vertical line indicating site events on the timeline. Above the graph, a status summary highlights site details such as branches, circuits, secure fabrics, and devices, with certain items marked as 'ADM Enabled' or indicated as active/inactive. A filter menu on the right side allows for reset options. The entire dashboard is laid out for quick site health monitoring.]()
In this example of the Prisma SD-WAN Site Summary Dashboard, you can see a dashboard that provides an information-rich display of branch-related metrics. These include new metrics such as network health as well as existing network, device and application metrics.
This particular tool allows administrators to monitor network performance across all sites in real time, troubleshoot issues based on network and application data, and optimize network paths by evaluating metrics like packet loss, latency, and jitter.
All SD-WAN vendors offer different SD-WAN monitoring tools and features. Regardless of which product you use, you’re definitely going to need access to a monitoring function that provides clear insights into SD-WAN health metrics.
Without this visibility, troubleshooting can easily wind up turning into a guessing game. And that only leads to longer downtime and frustrated users.
Choose an SD-WAN provider that offers centralized management and configuration
Centralized management tools allow for easier monitoring and troubleshooting across the entire network.
![The diagram illustrates centralized management in SD-WAN. It shows an SD-WAN controller at the center, managing data flows between the MPLS network, the internet, and cloud services. On the left, a branch office connects to the SD-WAN controller through traditional WAN routers. The middle section displays various types of connectivity, including fiber, dedicated internet access, MPLS, and 4G, all managed by the SD-WAN controller. On the right, the HQ/DC/DR is also connected via traditional WAN routers. Control plane data paths are indicated by yellow dashed lines, while data plane paths are shown as solid red lines.]()
A single pane of glass allows network staff to view and manage network performance. Which simplifies the process and reduces the time it takes to resolve issues because all the necessary information and controls are in one place.
It’s worth noting that most enterprise-grade solutions offer this. Centralized management is a key feature of the vast majority of SD-WAN platforms. It allows network admins to configure, monitor, and manage network policies across multiple sites from a single interface. However, some basic or lower-end SD-WAN solutions might require more manual, site-specific configurations.
Develop standardized troubleshooting procedures
Standardizing troubleshooting is extremely helpful when it comes to managing the complexity of SD-WAN environments.
![Flow diagram outlining a process titled 'How to troubleshoot SD-WAN.' It features seven steps connected by lines in a flowchart format. The first step, in a red box labeled '1,' is titled 'Check the basics' and advises determining whether the SD-WAN node connects to the controller and downloads configuration. The second step, in a yellow box labeled '2,' is titled 'Test interface operations' and involves checking if interfaces communicate with devices and the SD-WAN controller. The third step, in a blue box labeled '3,' is titled 'Examine routing structure' and focuses on verifying correct routing setup and accessible links. The fourth step, in a green box labeled '4,' is titled 'Validate VPN operation' and suggests ensuring the VPN functions properly. The fifth step, in a purple box labeled '5,' is titled 'Review forwarding rules' and involves verifying if packets follow the optimal path. The sixth step, in a light blue box labeled '6,' is titled 'Troubleshoot link performance' and advises diagnosing network link issues. The seventh and final step, in a teal box labeled '7,' is titled 'Troubleshoot app performance' and suggests addressing application-specific performance issues related to SD-WAN configuration or traffic management.]()
By having clear, documented processes for diagnosing and resolving common issues, the network team can respond way faster and more consistently.
Addressing security and visibility limitations
Security and visibility are critical concerns when implementing SD-WAN.
Unlike traditional WAN setups, SD-WAN often requires direct internet access at branch locations. This can potentially introduce security vulnerabilities if not properly configured and monitored. Which creates a dual challenge for network teams: ensuring robust security measures are in place while maintaining comprehensive visibility into network traffic.
With this being the case, it’s no surprise that a common security concern when it comes to SD-WAN is the potential loss of visibility.
When traffic is dynamically routed across various pathways, it becomes difficult to monitor and secure every data packet effectively. This can lead to blind spots, where malicious activities or network issues go undetected.
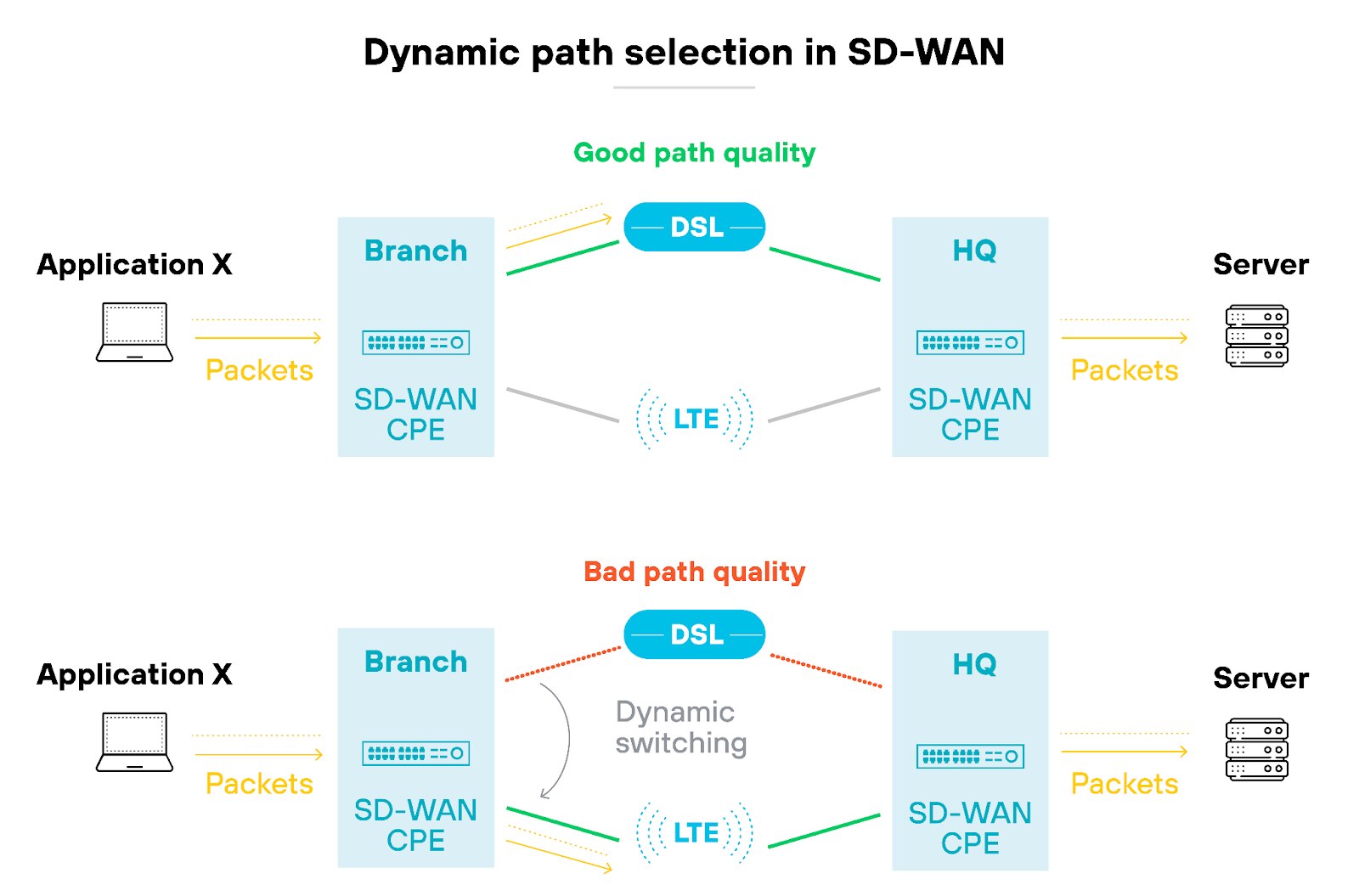
Here are a few effective ways to address security and visibility concerns in SD-WAN environments:
- Deploy a secure access service edge (SASE) framework
![Diagram titled 'Secure Access Service Edge (SASE)' showing the integration of networking and security services. At the top, four icons represent different cloud environments: SaaS Applications, Public Cloud, Private Cloud, and HQ/Data Center. Below, a horizontal bar labeled 'Security as a Service Layer' includes five components: FwaaS, CASB, ZTNA, and Cloud SWG. Another bar labeled 'Network as a Service Layer' contains SD-WAN. The bottom section shows three icons representing different locations: Branch/Retail, Home, and Mobile, connected by a red horizontal line. The diagram illustrates how SASE integrates security and networking services across various environments and locations.]()
SASE combines networking and security functions into a single cloud-based service. Which means that traffic is secured at every endpoint. And visibility is maintained across the network.
- Implement network segmentation
Network segmentation is another crucial strategy for addressing security and visibility limitations.
Separating critical assets and sensitive data from the rest of the network creates isolated zones that help contain potential security breaches.
For example:
![Architecture titled 'Network segmentation with security zones using Prisma SD-WAN & Prisma Access.' It shows a centralized Prisma Access cloud surrounded by shield icons, indicating security. To the left, labeled 'Prisma Access west location,' a building icon connects to 'Data center-1' with an IP address range of 10.5.0.0/16. To the right, labeled 'Prisma Access east location,' a 'Branch ION' connects to 'Data center-2' with an IP address range of 10.6.0.0/16. Each data center shows server icons representing their contents. Lines connect the locations and data centers through Prisma Access. A legend on the bottom right lists five security zones labeled 'Private,' 'Privileged,' 'IoT,' 'Services,' and 'Guest.' These zones are depicted with different colors, although the colors themselves are not specified in the text.]()
Here you can see a Prisma SD-WAN Instant-On (ION) network device in the east region with four zones on one LAN port, and the guest zone on another LAN port, in a typical branch location. Note: This process will be different depending on the SD-WAN solution, in addition to the network environment.
Each zone is associated with a single subnet in the LAN switch. The non-guest devices in the zone have access to the rest of the network through the sub-interface on the ION. The guest users only have access to the internet.
This design model uses the following zones as examples:
- Private: General users at the remote site
- Privileged: Privileged users who manage the remote site
- IoT: IoT devices at the remote site
- Services: Devices that provide network services to the remote site
- Guest: Guest users at the remote site
Segmentation makes traffic monitoring simpler. It also makes it possible to apply targeted security policies, which strengthen the overall security posture.
- Use automated security and monitoring tools
Automation plays a significant role in maintaining both security and visibility.
Automated monitoring and reporting tools can help reduce the burden on network and security teams by identifying and mitigating threats in real time. These tools can also help filter out false positives so that staff aren’t overwhelmed by constant alerts that turn out to be non-issues.
This way, teams can focus on addressing genuine threats, improving the overall security of the network.
Tip: Not all providers include substantial built-in SD-WAN security features. Be sure to choose a solution that integrates well with your existing security infrastructure.

SD-WAN requires ongoing management, troubleshooting, and updates.
This isn’t generally a problem for organizations who have sufficient internal resources. For those that don’t, it can potentially strain the internal team and lead to increased operational costs over time.
Choosing the right management model for your SD-WAN deployment can significantly impact network performance and efficiency. Unlike traditional WANs, SD-WAN offers flexible management options—ranging from DIY to fully managed solutions.
DIY SD-WAN
First, let's consider the DIY approach.
Managing SD-WAN in-house gives you complete control over the network. It’s ideal if your network team has the necessary expertise and resources. You can make changes on the fly, customize configurations, and directly address any issues.
However, this level of control requires a significant investment in time and skills. If your team is already stretched thin, a DIY approach will probably lead to delays and operational headaches.
Fully managed SD-WAN
On the other hand, fully managed SD-WAN services take the load off your internal team.
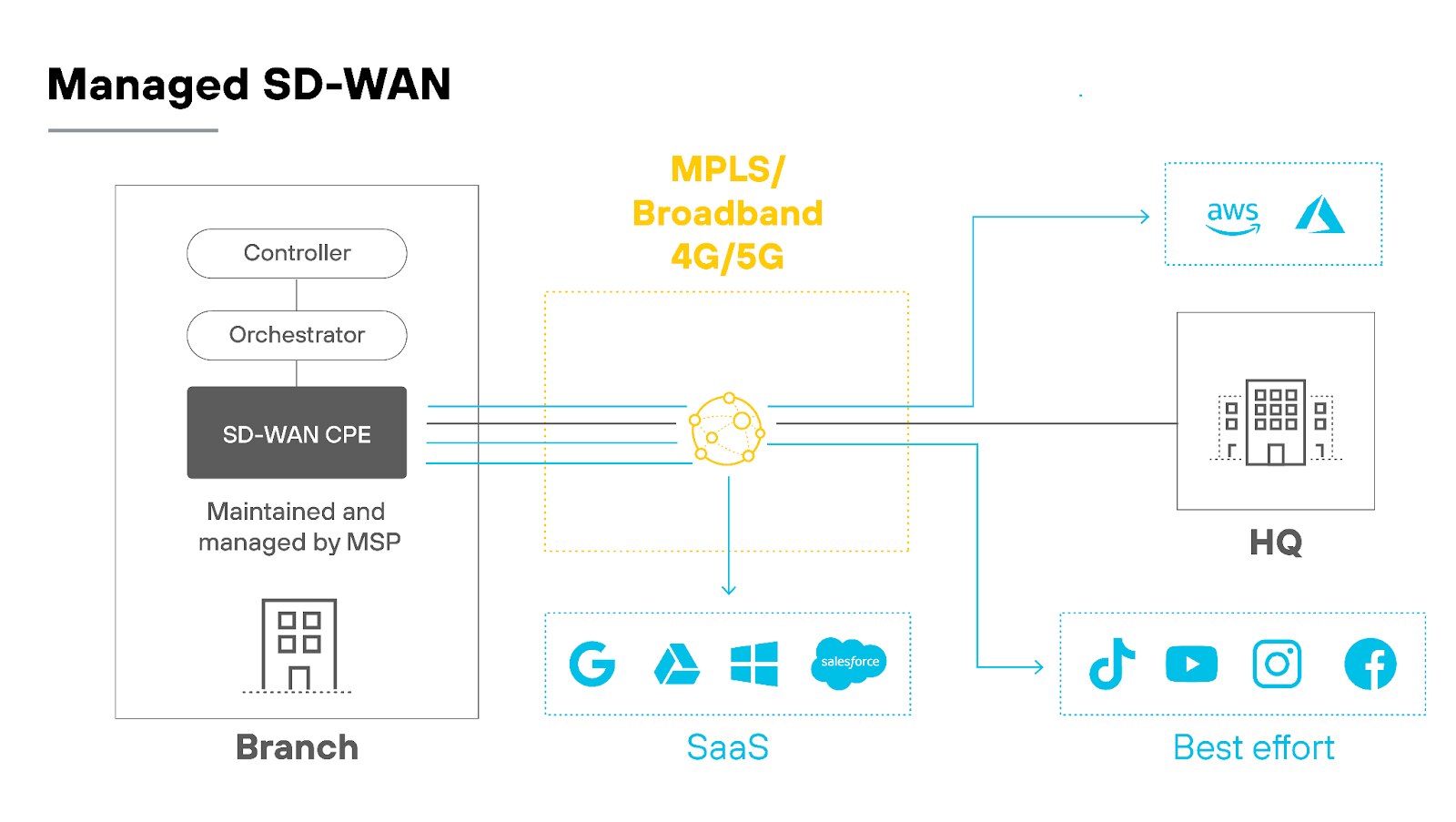
The provider handles setup, configuration, monitoring, and troubleshooting. This option is appealing for organizations that lack the bandwidth or expertise to manage SD-WAN themselves.
The downside? You might lose some control and flexibility, depending on the provider's responsiveness and the level of service they offer.
Co-managed SD-WAN
There’s also a middle ground: co-managed SD-WAN.
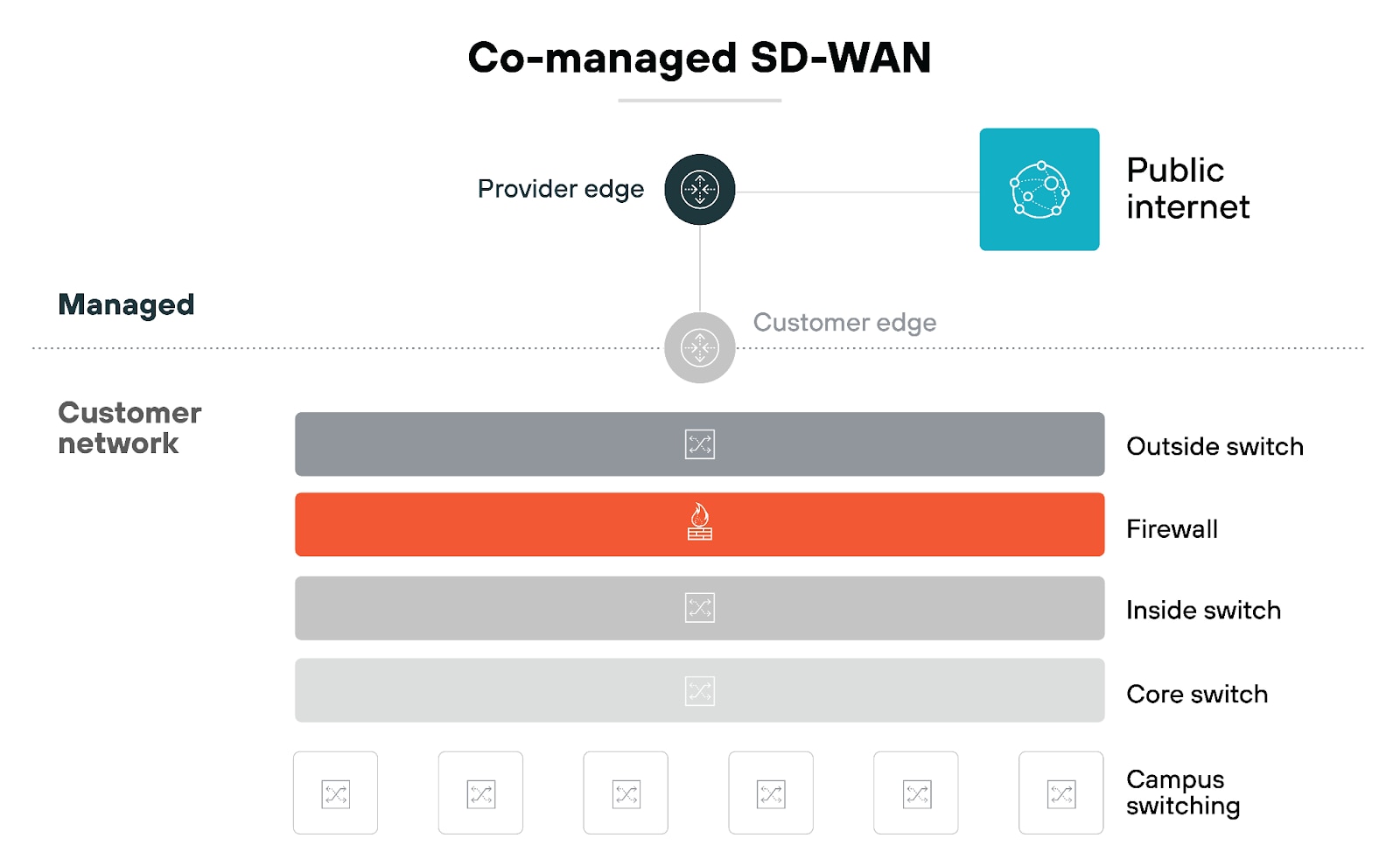
With this model, your provider takes care of the heavy lifting, but you still retain some control over day-to-day operations. It’s a balanced approach that lets your team focus on strategic tasks while the provider manages routine maintenance and complex issues. This option works well if you want to stay involved without being overwhelmed.
Managed CPE
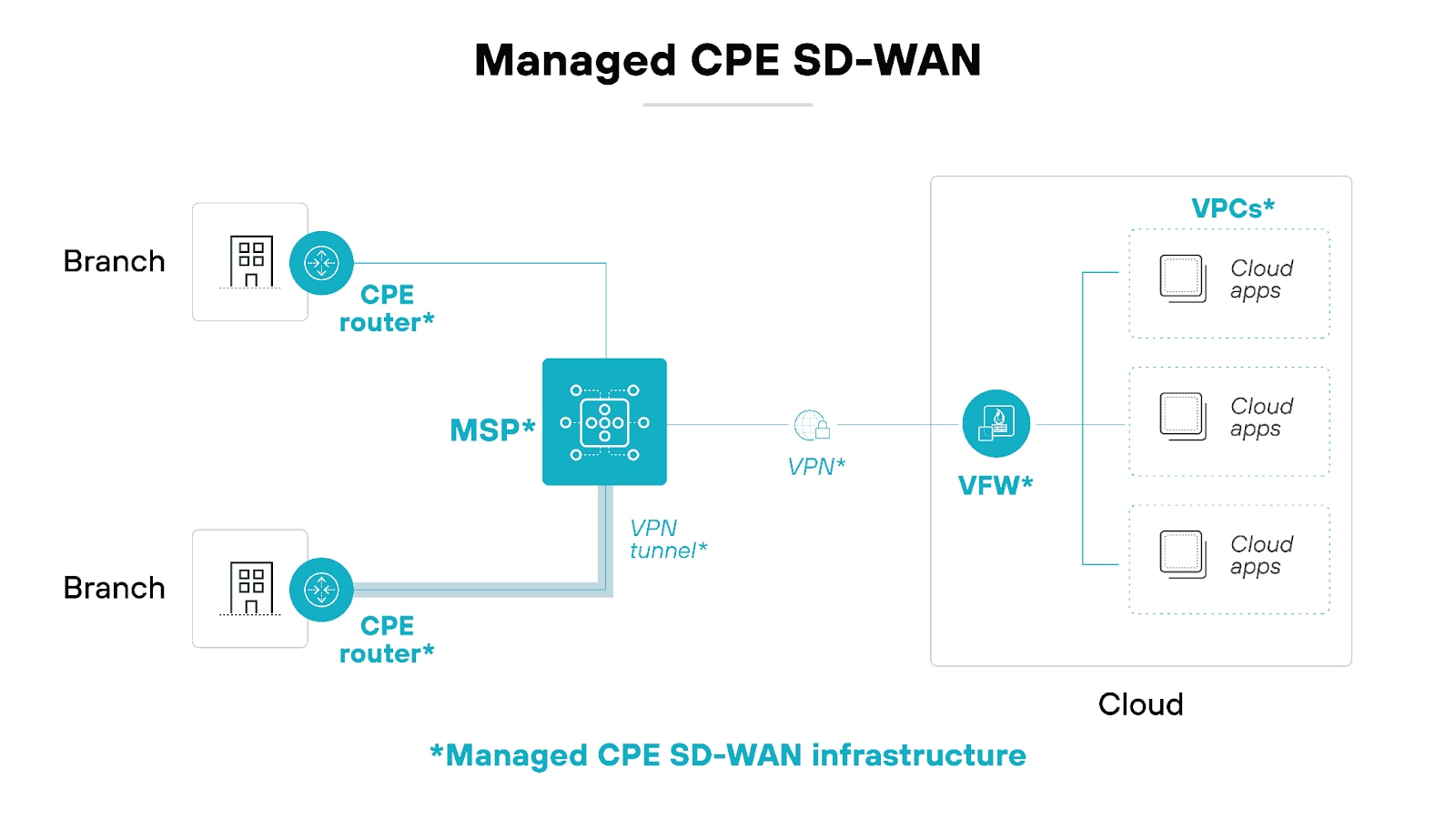
In a managed customer premises equipment (CPE) SD-WAN deployment, the provider manages the physical network equipment installed at the customer’s locations.
This approach is typically best for businesses with specific security and compliance requirements that require physical hardware and direct involvement from the IT team.
SD-WANaaS
SD-WAN as a Service (SD-WANaaS) is a cloud-delivered, subscription-based alternative to on-premises SD-WAN deployments.
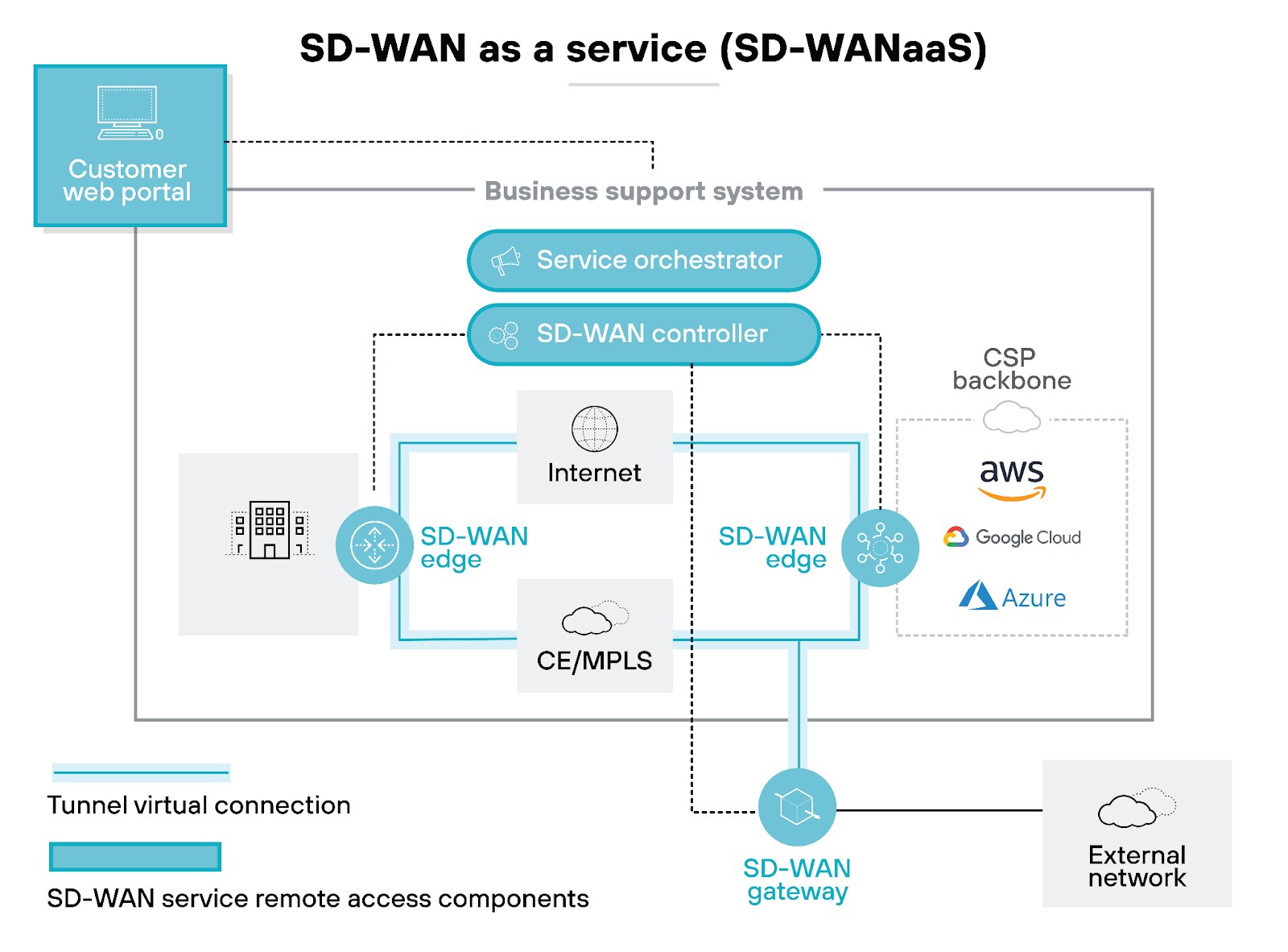
It provides SD-WAN functionality without the need for on-site appliances, installation, or management. This model offers flexible, easily scalable solutions with minimal upfront investment.
For small businesses lacking extensive in-house network and security resources, SD-WANaaS delivers the necessary network performance and security without the burden of maintaining an on-premises SD-WAN system.
SD-WANaaS can also potentially work well for companies with large, complex cloud infrastructures because it simplifies SD-WAN design and implementation.
SASE
Some managed SD-WAN MSPs offer SASE integration as part of their service offerings.
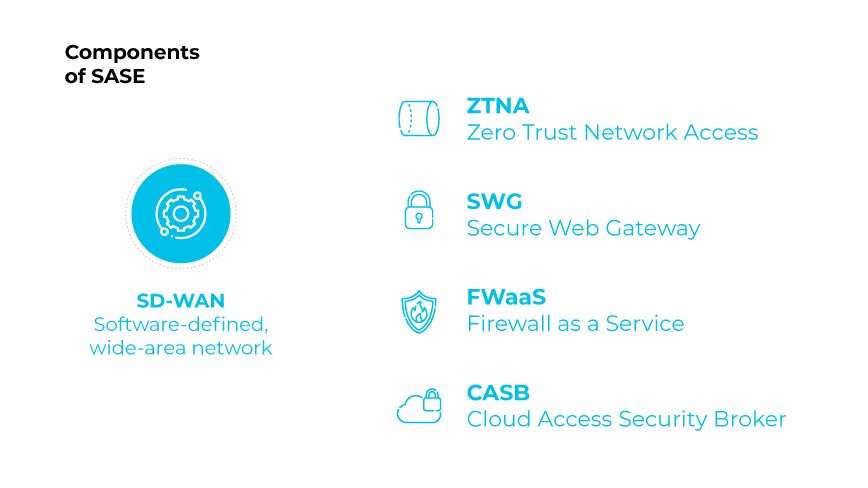
Secure access service edge (SASE) combines SD-WAN with a suite of integrated security services, including:
- Secure web gateway (SWG)
- Cloud access security broker (CASB)
- Next-generation firewall (NGFW)
- Zero trust network access (ZTNA)
SASE provides a comprehensive network security environment, addressing modern cybersecurity threats while delivering network performance and reliability.
The challenge is choosing the model that best aligns with your business needs.
Start by assessing your internal capabilities. Do you have the expertise and time to manage SD-WAN effectively?
If not, a fully managed or co-managed model might be more appropriate.
Also, consider your long-term goals. If flexibility and control are crucial, leaning towards DIY or co-managed options might make sense.
Tip: Don't forget to evaluate the vendor's offerings. Some vendors are better suited for DIY management, providing robust tools and support. Others excel in fully managed services, offering seamless integration and comprehensive support. Your choice of vendor should complement the management model you select.
Further reading:










