Understanding and visualizing your cloud risks can be difficult to do. And, even if you have overcome those issues, the more data you collect often means more alerts and more work for your security team. It's time consuming to manually prioritize large volumes of cloud security alerts based on criteria such as whether the impacted resource had a public IP, host vulnerability, or attached identity and access management (IAM) permissions.
Your security team gets a lot of rich data regarding your cloud network and servers from Prisma Cloud. This includes alerts on issues such build misconfigurations or untrusted network traffic. But, extracting and correlating all the data from Prisma Cloud to determine severity and prioritize each alert doesn’t need to be a time consuming task that requires browsing between several screens when performed manually.
With the Prisma Cloud and Cortex XSOAR integration, enrichment, correlation and severity scoring can be fully automated with a playbook using API custom queries based on each alert data.
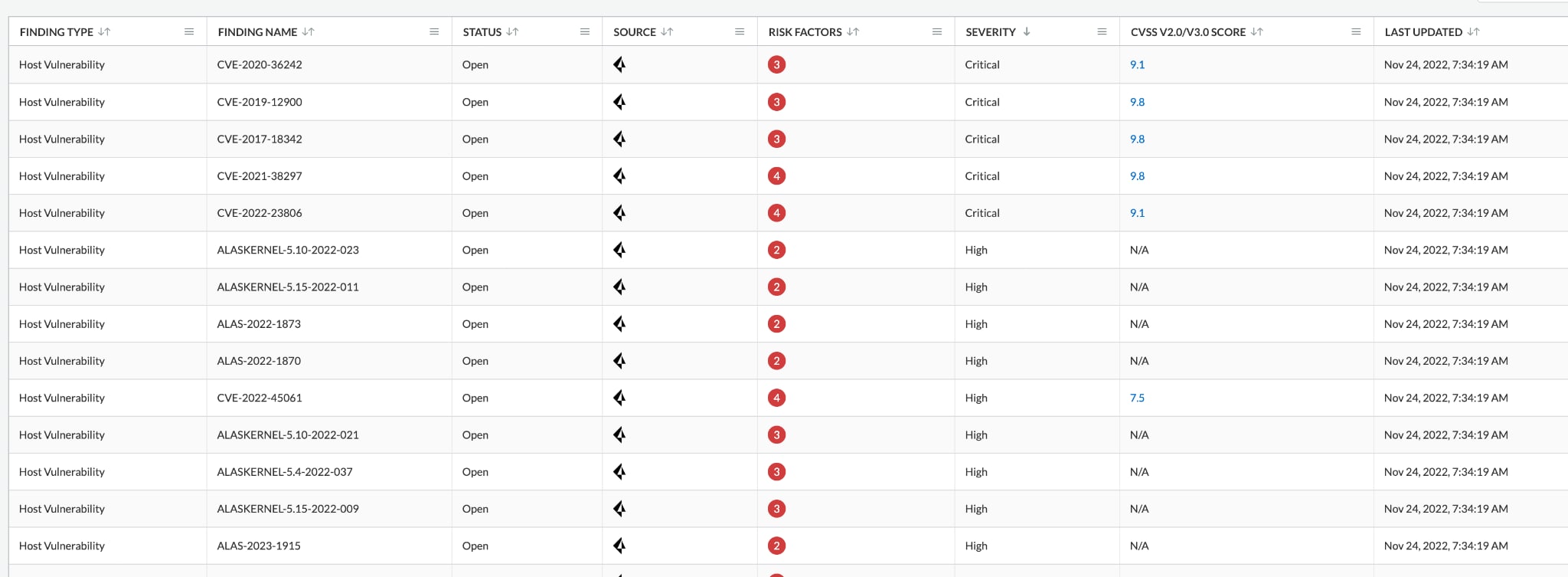
In addition, most organizations have separate teams (and even sub-teams) involved in the remediation of such alerts, spanning security, network, infrastructure, etc.
Cortex XSOAR provides a central location for case management and cross-team collaboration. Cortex XSOAR can automate the process of communications and ticketing, for example, creating a Jira issue or sending a Slack message with all of the enriched data to the relevant stakeholders.
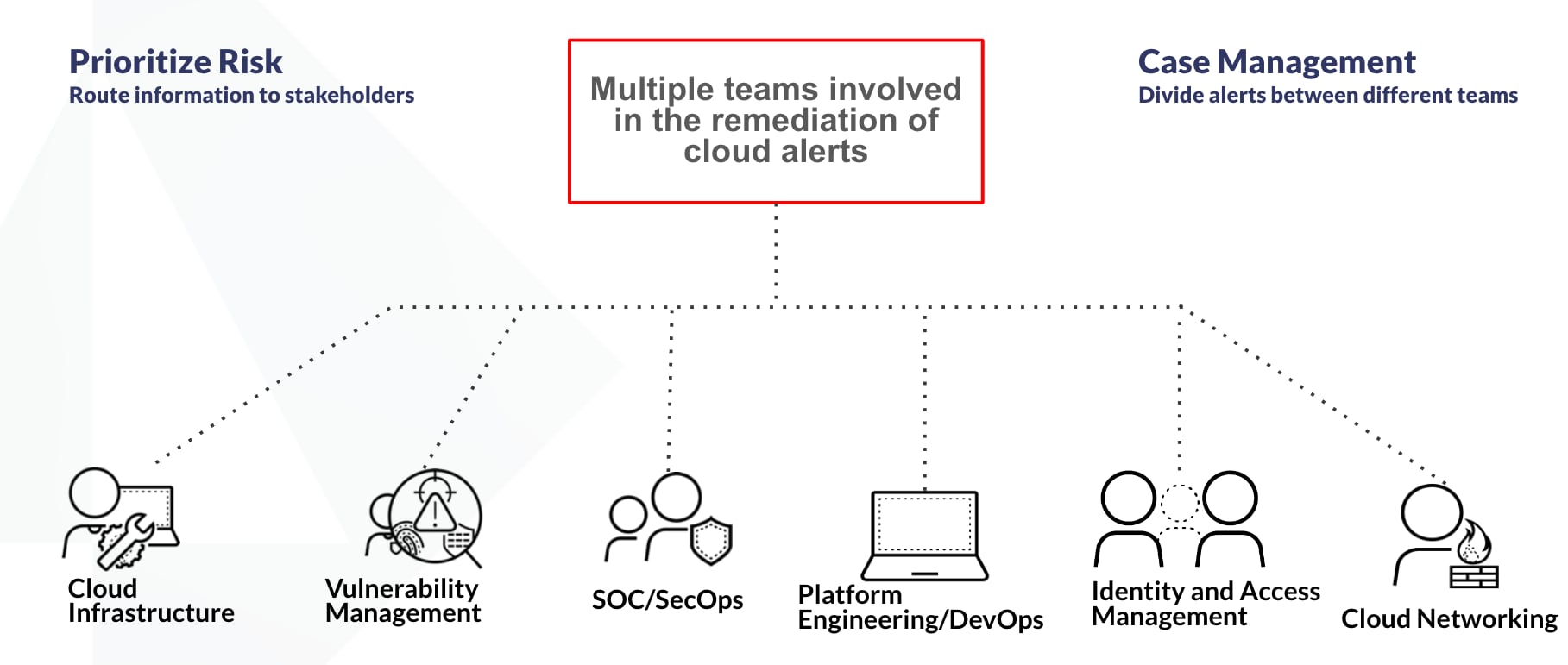
What Does the Playbook Do?
- This playbook will handle incidents related to dozens of Prisma Cloud public virtual machine (VM) alerts.
- It will first determine the severity of the ingested alert based on these conditions:
- Does a public IP exist on the instance?
- Are there any host vulnerabilities or findings related to the instance?
- Are there any IAM permissions attached to the instance?
- After setting the severity, it will create new ticket/issues on third-party systems, such as Slack and Jira, with all the relevant information.
- When the alert is ingested and during the playbook run, the Cortex XSOAR incident layout will be updated with relevant information to assist the analyst investigating the incident.
- It will also extract and enrich indicators using existing configured integrations.
- At the end, the playbook will close the alert.
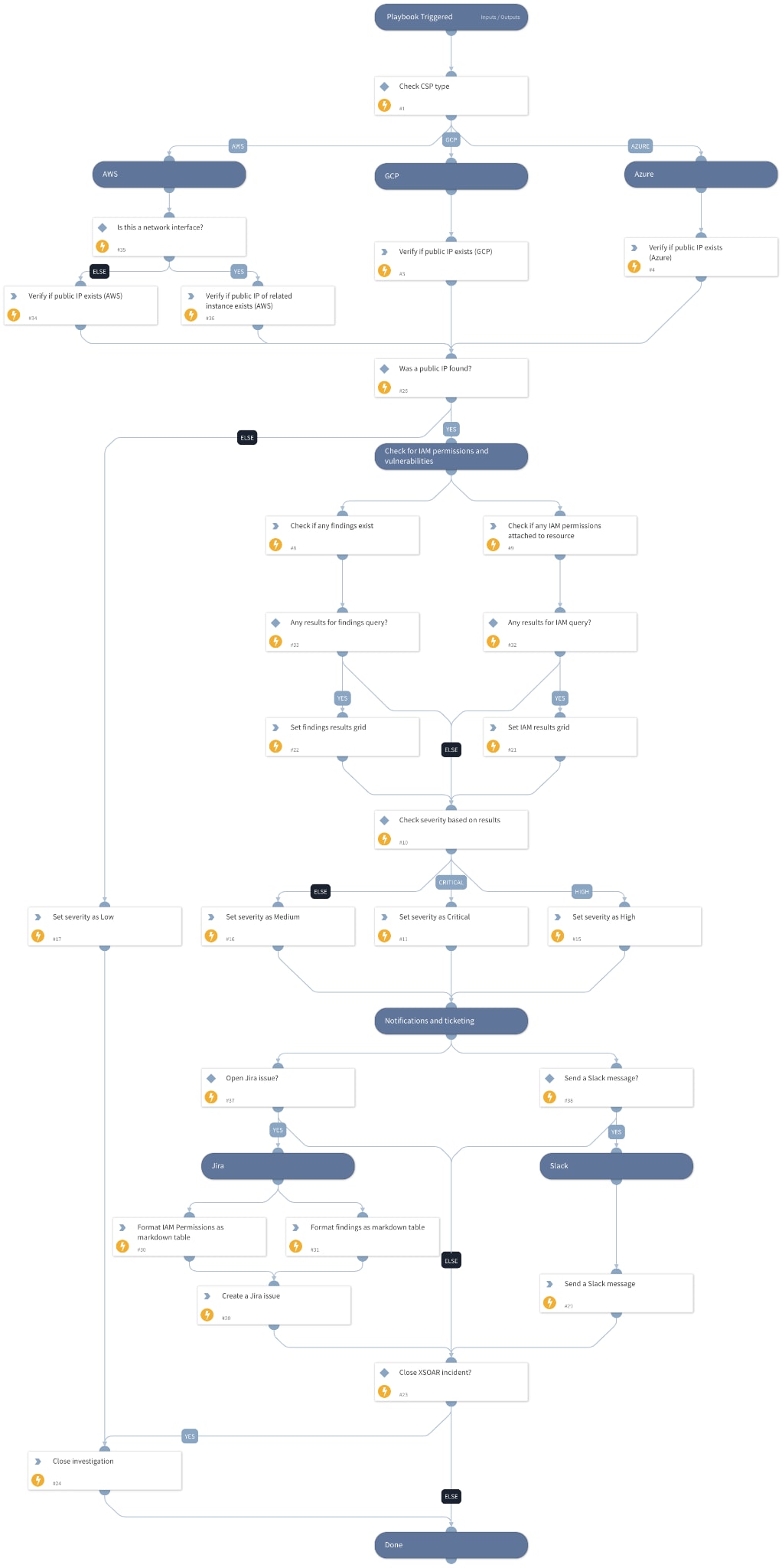
The Incident Layout
Cortex XSOAR provides detailed incident layout views to aid analysts further their investigation. There are two main tabs: Case Info and Investigation.
The Case Info tab presents high level data, such as enrichment, notifications, and communications results:
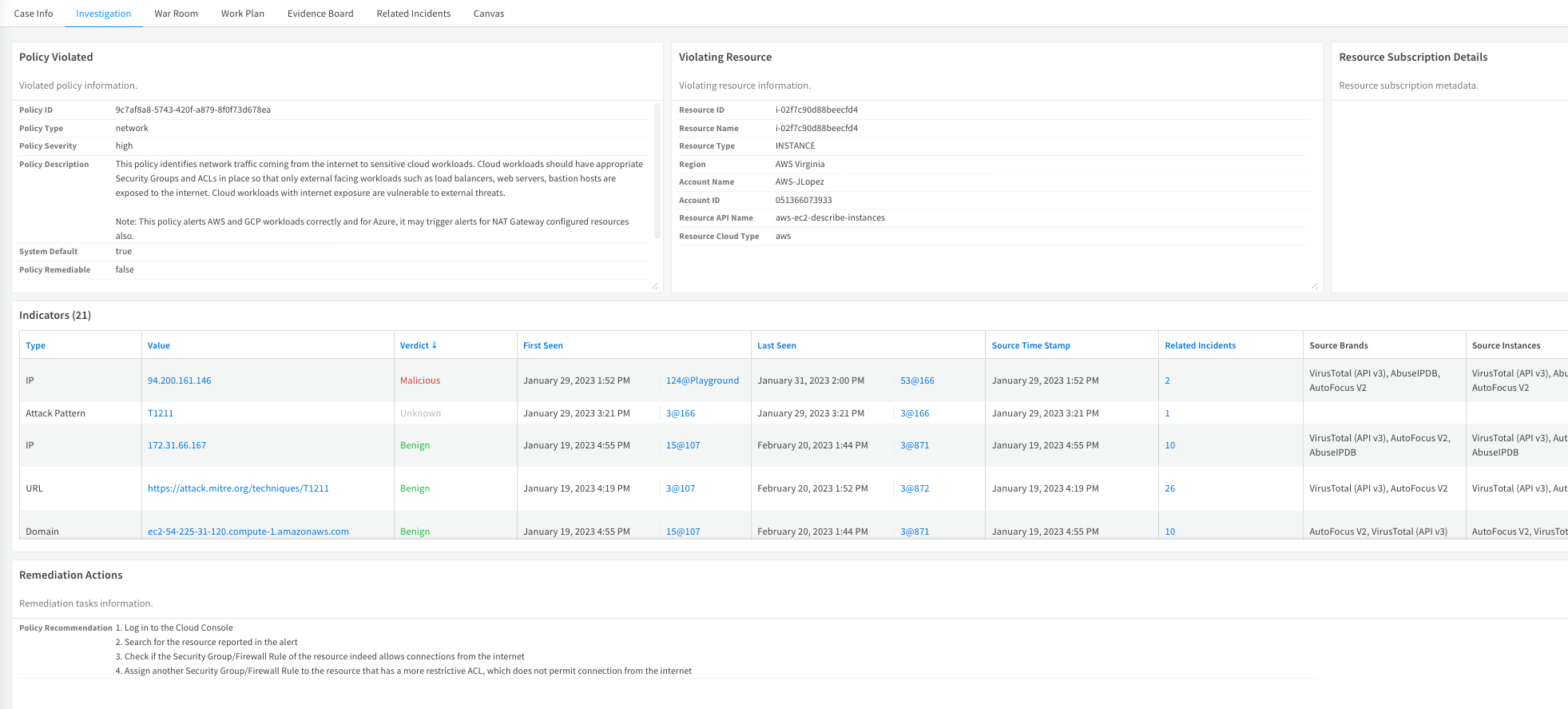
The Investigation tab presents more detailed information, including policy data, violating resources, and indicators:
Conclusion
Combining Prisma Cloud with Cortex XSOAR facilitates the process of handling cloud security incidents and alerts, which can save multiple teams precious time and also prevent human errors while remediating threats.
This playbook is part of the Prisma Cloud content pack which can be located in the Cortex Marketplace. For more information about the Prisma Cloud and XSOAR integration, please read this blog.
To learn more about how you can automate security operations with Cortex XSOAR, check out our virtual self-guided XSOAR Product Tour
We also host virtual and in-person events, so check here for upcoming ones.