Microsoft Graph API provides developers an interface to interact with various services, including Entra ID and Office 365. It enables programmatic access to organizational data such as user information, emails, OneDrive files, and more, making it a highly powerful tool that can also be abused by threat actors.
In October 2023, Microsoft introduced the Graph activity logs which record all HTTP requests made to the Microsoft Graph service in a tenant. They provide a history of all Microsoft Graph API requests, offering visibility into actions performed by users and applications authorized in the tenant. These logs are not collected by default but can be configured to via Azure Monitor's diagnostic settings.
In the past, customers had limited visibility into these operations which made it difficult to effectively investigate and respond to incidents. With this data now available, these logs can be valuable for tracking the activity of a suspicious user, identifying anomalous Microsoft Graph API calls by application, and much more.
Microsoft Graph API as an Attack Vector
Microsoft Graph API has become a significant attack surface for threat actors granting access to a range of Microsoft services like Entra ID and Office 365. Once an attacker gains an initial foothold in a tenant, they can abuse their permissions to gain unauthorized access to sensitive organizational data such as mailboxes, files in OneDrive or SharePoint, Teams chats, and more.
Attacks observed in the past have demonstrated how threat actors have used Microsoft Graph API to perform malicious actions within tenants. In the following sections of this blog we’ll analyze an attack flow observed in the wild to highlight the importance of monitoring Microsoft Graph activity logs to uncover attack chains that leverage the Graph API. This example clearly demonstrates how tracking Graph API logs not only gives you valuable context for Graph API operations within your tenant, but also plays a critical role in detecting and responding to potential security threats.
Microsoft Graph Activity Logs in Cortex
Microsoft Graph activity logs are collected and standardized into cloud_audit_logs - a dataset that contains the enriched and normalized cloud logs. The logs contain various fields including application ID, Service Principal ID or user ID, request URI, IP address, user agent, and others, giving you a clear visibility into all requests made to the Microsoft Graph service in your tenant. This visibility enables security analysts to quickly detect and respond to any suspicious activity.
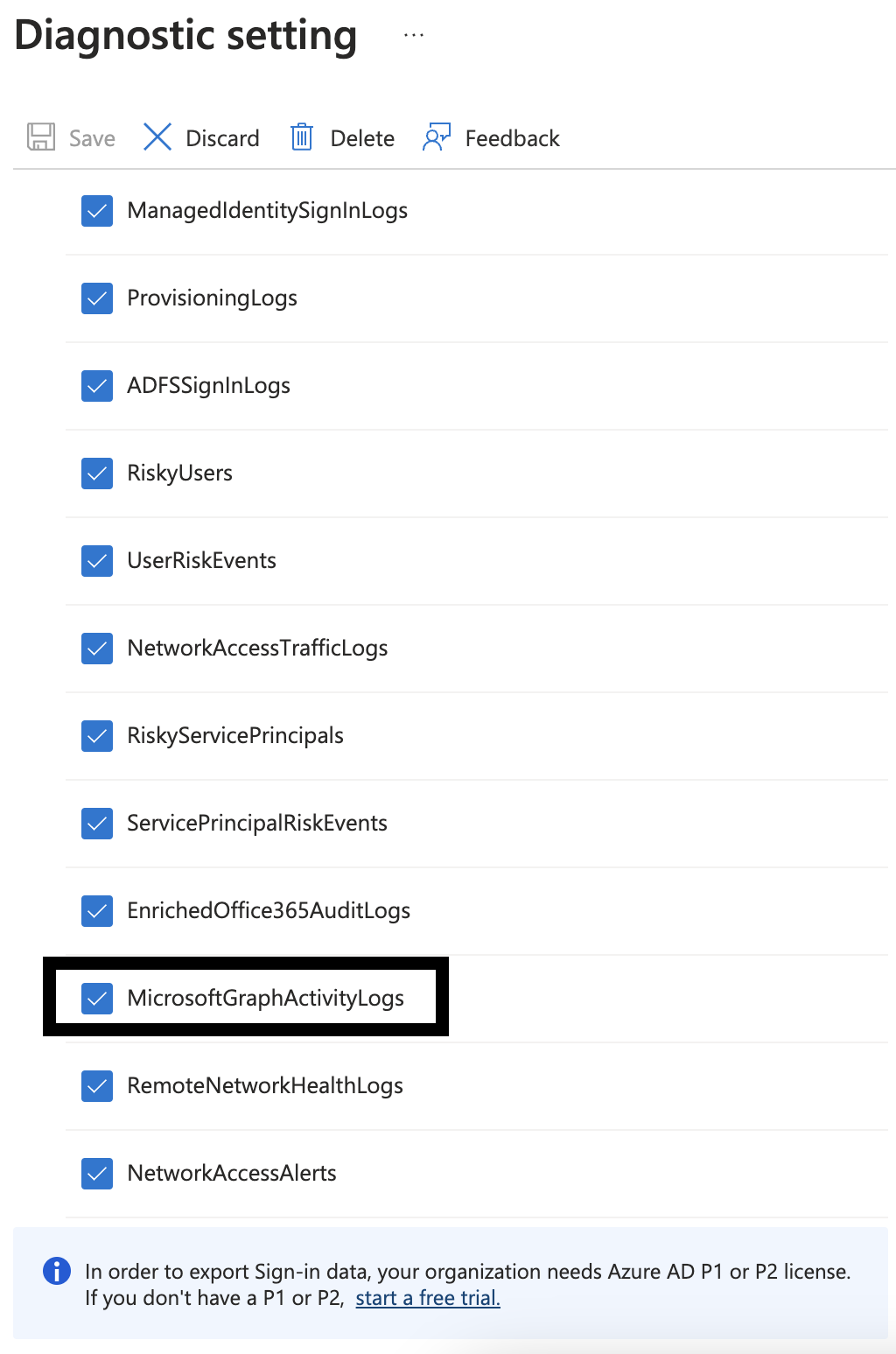
Enabling Microsoft Graph activity logs can be done through Entra ID Diagnostics settings, configured to stream to an Event Hub:
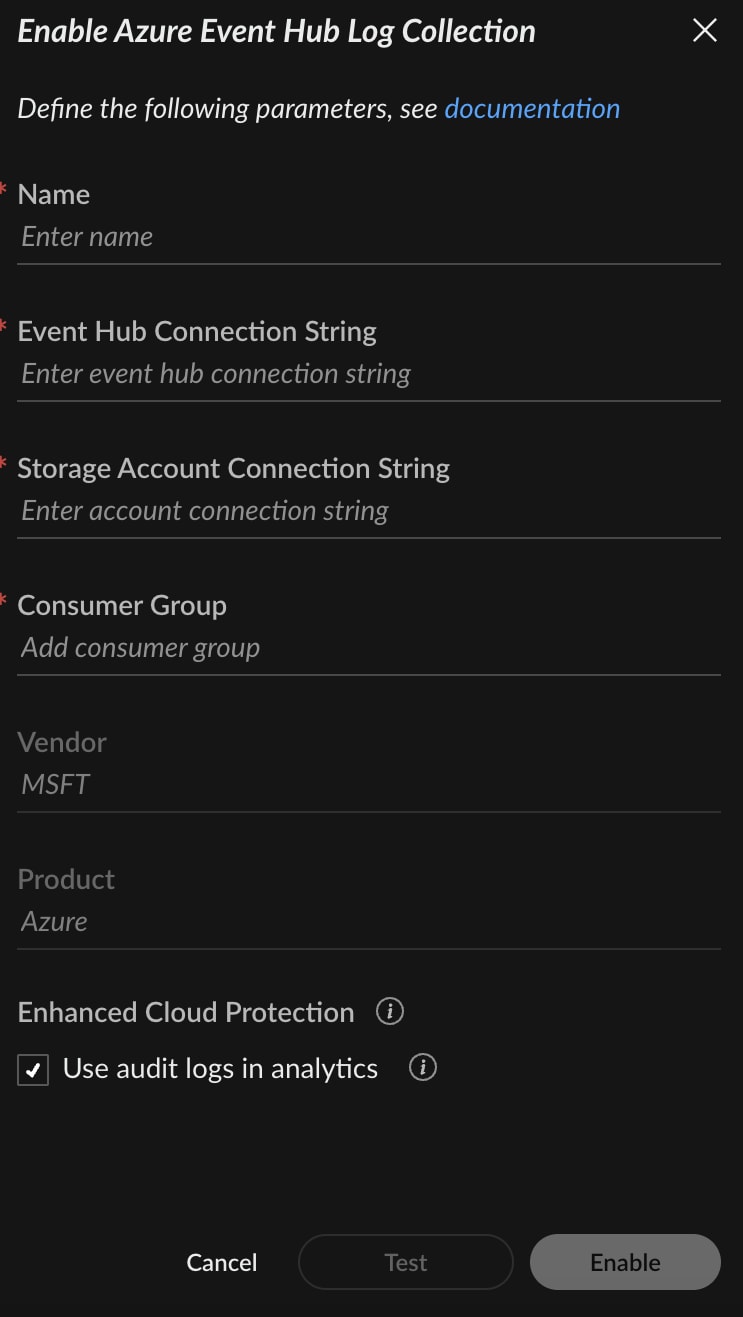
To collect these logs from Azure, configure the Azure Event Hub log collection through Cortex:
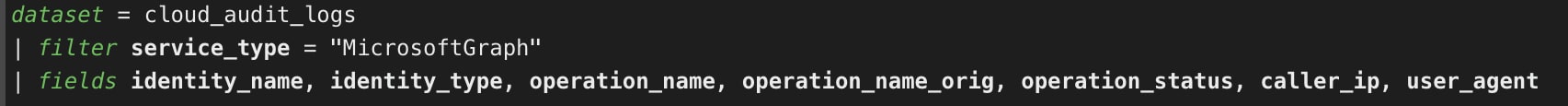
To access Microsoft Graph data, the XQL query below provides an example of fields found in the Microsoft Graph activity logs:
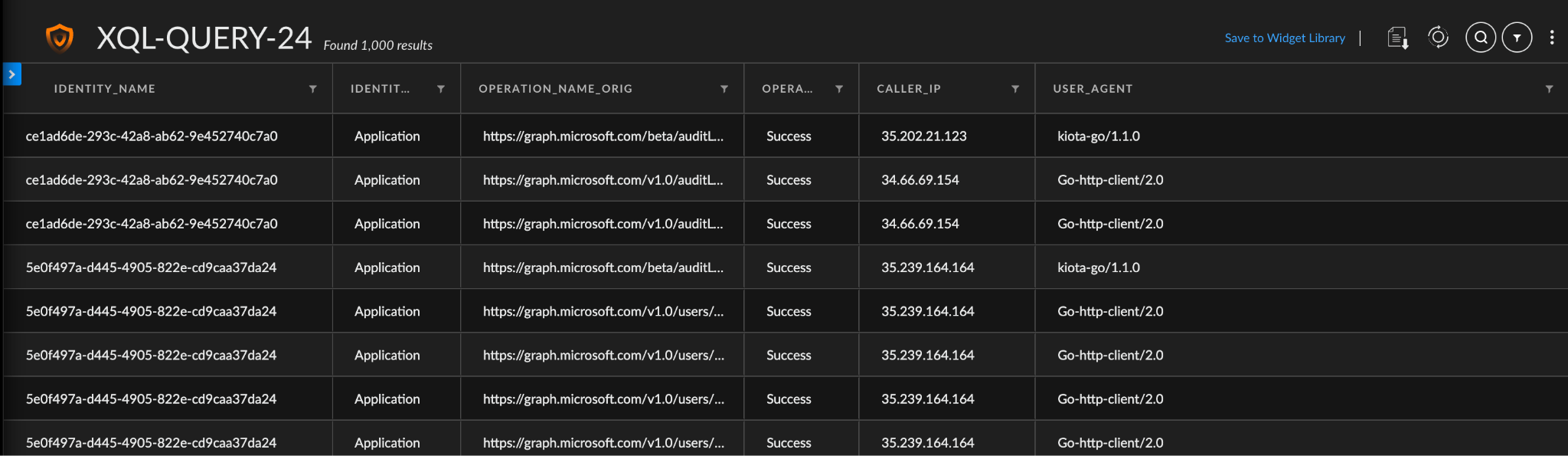
Microsoft Graph Threat Detection in Cortex
With the increase in security threats and a growing number of attacks leveraging Microsoft Graph API, Cortex provides tailored detections to address different attack vectors, which will be demonstrated through a real-world attack scenario.
Initial Access
In one use case we observed, the attack began when a threat actor compromised a system-assigned Managed Identity of an Azure virtual machine, by exfiltrating its token through the Instance Metadata Service (IMDS) and abusing it.
Tenant Discovery
The attacker used an open-source attack framework and custom scripts leveraging Microsoft Graph API to enumerate the environment, extracting tenant information including users, groups, applications, and more. However, some of their operations were denied due to insufficient permissions. During this process they also performed privilege discovery. The following Microsoft Graph APIs were observed during the enumeration process:
- https://graph.microsoft.com/v1.0/organization
- https://graph.microsoft.com/v1.0/users/{id}
- https://graph.microsoft.com/v1.0/groups/{id}
- https://graph.microsoft.com/v1.0/applications/{id}
- https://graph.microsoft.com/v1.0/directoryRoles
Service-specific Enumeration
Following the enumeration of the tenant, which indicated that the service principal possessed privileged permissions, the attacker shifted focus to a service-specific enumeration, primarily targeting OneDrive and SharePoint. This involved enumerating various OneDrive drives and SharePoint sites. The Microsoft Graph APIs shown below were observed during this phase, covering only part of the attacker’s activities:
- https://graph.microsoft.com/v1.0/users/{id}/drive
- https://graph.microsoft.com/v1.0/drive/items/{item-id}
- https://graph.microsoft.com/v1.0/sites/{site-id}
Exfiltration
After completing the enumeration sequences, the threat actor proceeded to exfiltrate files from users’ OneDrive drives and SharePoint sites. This included the following Microsoft Graph APIs:
- https://graph.microsoft.com/v1.0/drive/items/{item-id}/content
- https://graph.microsoft.com/v1.0/sites/{site-id}/drive/{drive-id}/items/{item-id}/content
Persistence
In the final phase, the attacker created a backdoor by adding a password to an additional Entra ID application using the Microsoft Graph API:
- https://graph.microsoft.com/v1.0/applications/{id}/addPassword
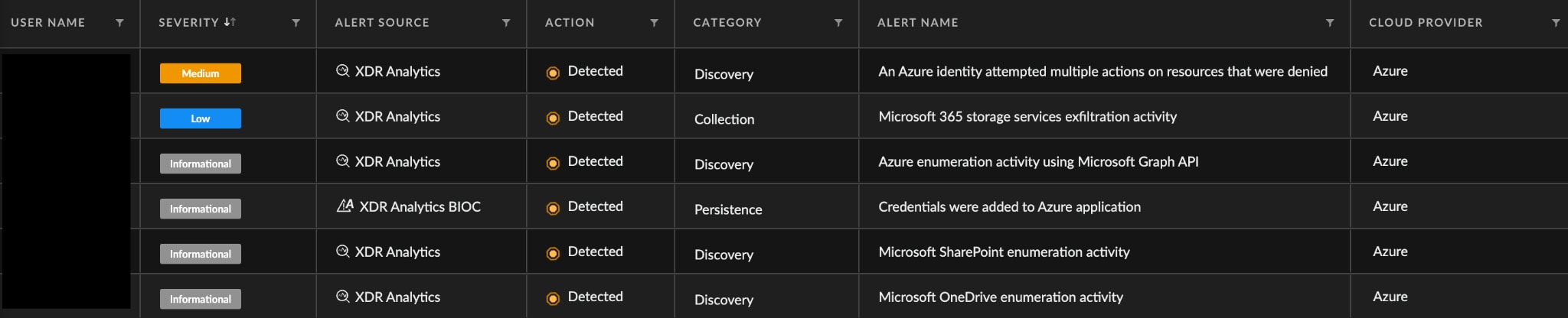
Through an analysis into penetration testing tools leveraging Microsoft Graph along with Azure and Office 365-specific TTPs, we have developed tailored detections, which some include:
| Tactic | Detections Names |
|---|---|
| Discovery | Azure enumeration activity using Microsoft Graph API Microsoft SharePoint enumeration activity Microsoft OneDrive enumeration activity Mailbox enumeration activity |
| Persistence | Authentication method was added to Azure account Credentials were added to Azure application |
| Exfiltration | Microsoft 365 storage services exfiltration activity Azure high-volume data transfer |
Figure 6. Microsoft Graph Detections
Using Cortex to Investigate Microsoft Graph Activity
The Cortex Query Language (XQL) enables you to query for information stored in a wide variety of data sources in Cortex XDR, including Microsoft Graph activity logs. The following XQL queries can be used for data exploration, as well as for investigation or hunting.
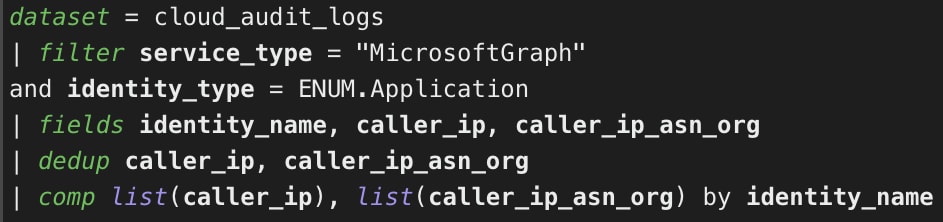
Identify the IP Addresses and ASNs Associated with Each Azure Application
This query can be useful for investigating unusual application activity originating from unknown infrastructure, such as unfamiliar IP addresses, or ASNs, which may indicate token theft attempts.
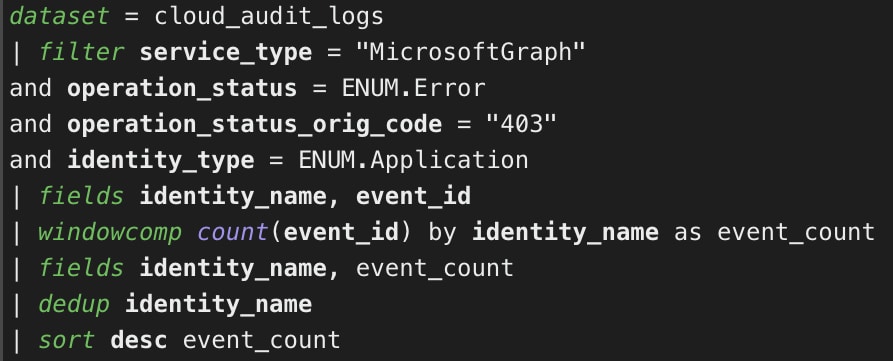
Identify Azure Applications with Denied Request Attempts
This query can help identify abnormal application denied operations, which are often seen during enumeration attempts.
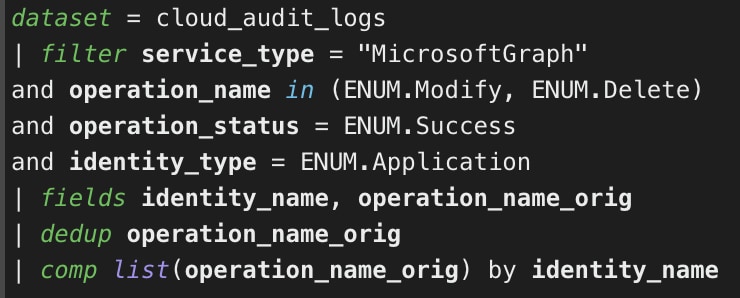
Identify Successful Changes Made by Azure Applications
This query could assist in investigating changes (modification or deletion) made to resources in the tenant performed by an application suspected of anomalous behavior.
Summary
Microsoft Graph activity logs provide detailed records of Graph API calls made within Azure tenants, offering a thorough view of all Microsoft Graph activities in the environment. Collecting and monitoring these logs is essential for identifying suspicious behavior and responding to security threats. Together with Azure sign-in and activity logs, Microsoft Graph activity logs give a complete view of tenant activity.
Cortex XDR® and Cortex XSIAM® offer a comprehensive security solution with specialized detections for Microsoft Graph threats, enabling security analysts to effectively detect, respond to suspicious activity while ensuring seamless incident investigation and management.