We’re quickly approaching the halfway point of 2024 and, with it, the advent of the summer security conference season. This got us thinking about our favorite go-to open-source security tools!
Whether we’re building a cloud application security workshop or taking part in a Kubernetes capture-the-flag, here are the tools we find ourselves wget-ing, brew installing, or yolo curling to bash.
We’ve split our hot-picks into three sections, whether you’re an offensive security professional, a defender, or looking for the latest training and personal development goodies, you should find something that suits you.
On the Defensive
Let explore open-source security tools that empower organizations to build proactive defense strategies, fortifying their systems against an increasingly sophisticated array of cyberthreats. By utilizing these versatile tools, companies can enhance their threat detection and response capabilities, ensuring a resilient security posture.
OpenSSF Scorecard
Victory loves preparation, as they say, and security preparation is no exception! We often see small teams or individuals stuck with the question, What's the first security step?
The OpenSSF Scorecard project gets a special mention here, especially now that their checks are automated for repeat testing of your repository in CI/CD. The simplicity of a project that checks for a variety of security issues for OSS maintainers, plus the growing community around the project is a great step toward better security mindfulness and understanding.
Cosign by Sigstore
Unless you’ve been living in a bunker for the past couple of years, you are now well aware of the risks supply chain attacks pose to our modern technology ecosystems. While it’s not the most exciting of topics, it may be one of the most important.
Cosign gets a mention here because it reduces the barrier and complexities traditionally associated with building and maintaining your own code signing solution. (CA Certs, request APIs, transparency logs, etc). Out of the box, it uses keyless signing based on a publicly viewable transparency log.
While binary and artifact signing isn’t the end all, be all of security, it’s an important piece that we should include in our builds. Signed artifacts build a good foundation for other important factors, such as CI security, so read on for tools that will help you to trust your signing pipelines.
Checkov by Prisma Cloud
OK, so we’re a little biased but Checkov remains one of the industry’s go-to tools for infrastructure as code, secrets and more. Let’s face it, not many tools can improve your DevOps security posture as quickly, nor do many include configuration files you can tailor to each repository and a baseline feature to block only newly discovered issues in CI. Checkov is a great open-source cloud security multitool.
The New, Free Prisma Cloud IDE Plugin:
After community feedback, we’ve removed the need to have an API key for use of the Checkov scanning features for the VSCode Prisma Cloud plugin (Support for the IntelliJ plugin coming soon!). You can now have your Kubernetes and infrastructure as code annotated as you edit, which also gives the ability to quickly create inline suppressions on a per-policy basis!
Trufflehog
In the words of Truffle Security, “TruffleHog™ is a [open-source] secrets scanning tool that digs deep into your code repositories to find secrets, passwords and sensitive keys.” It can of course scan GitHub repositories performing complex multibranch analysis, but it can also dig into S3 buckets, filesystems and Docker images in a flash.
✅ Found verified result
Detector Type: AWS
Decoder Type: PLAIN
Raw result: AKIAXYZDQCEN4B6XXXX
Resource_type: Access key
Account: 534212345678
…
Kubescape
Kubescape is a CNCF Sandbox project designed to run as part of your CI/CD pipeline, protecting your cluster with a Kubernetes operator for ongoing scanning of existing cluster workloads.
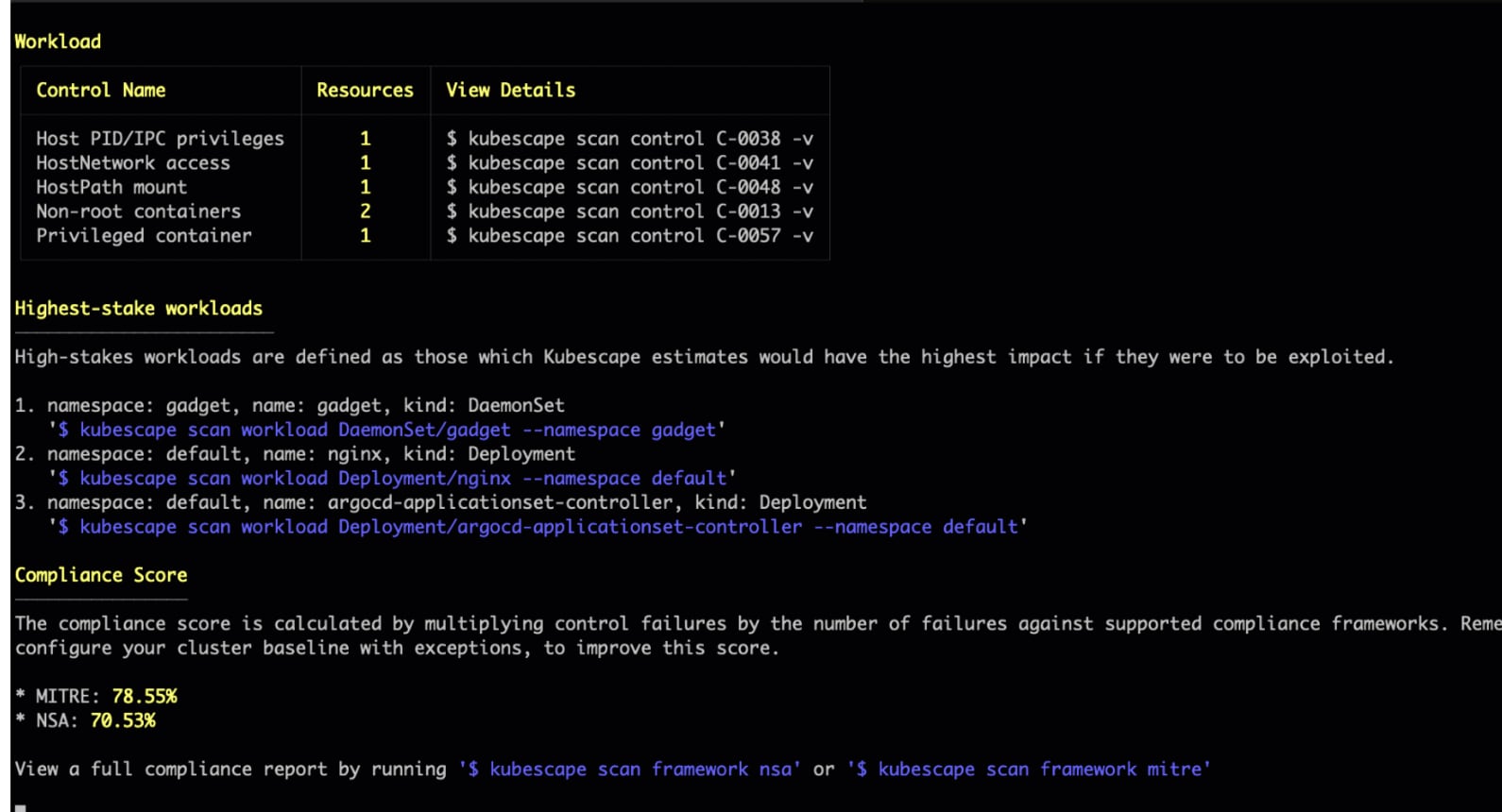
While Kubernetes doesn’t exist in a vacuum, and cloud infrastructure, data security and API security must be considered, Kubescape earns its place on this list as a great starting point for CNCF-backed Kubernetes security.
We especially like the highlight of the high-stake workloads that pose the most post-exploitation risk to the cluster (As you know, we like context here!).
Trivy
The brainchild of Teppei Fukuda, Trivy went from relative obscurity to having over 21.7K stars (when writing this blog post) and becoming the defacto open-source scanner for images. Its differentiating feature is speed. Trivy achieves this by caching vulnerability signatures locally and only downloading occasional delta updates on each execution.
Since its inception as a container image scanner, the feature set expanded its capacity to hunt for known vulnerabilities, misconfigurations and secrets and now covers:
- Filesystem
- Git Repositories (remote)
- VMs
- Kubernetes
- SBOMs
- Terraform
Trivy even has an interesting client/server mode. It allows a single instance to act as a server that harbors the vulnerability database in one location while client Trivys can reference it via a server flag to avoid multiple local copies of the database.
While the IaC may not match Checkov’s breadth and depth, and the secret scanning may not reach the diversity of a TruffleHog, Trivy has become an excellent image scanner. Additionally, it’s matured into a swiss army knife for the open-source security community.
Cilium
Cilium is a great place to start when you move from a single node dev cluster to real Kubernetes workloads and need answers to “what's going on in my cluster”.
BadRobot by ControlPlane
The first of a number of ControlPlane OSS goodies in this list. BadRobot performs static security tests — specifically against Kubernetes operator manifests, as operators are often deployed with a lot of access to the cluster.
BadRobot README.md excerpt: The risk analysis that BadRobot evaluates is primarily focused on the likelihood that a compromised Operator would be able to carry out privilege escalation and obtain full control over every resource in the cluster and in all namespaces.
Let's Put Our Black Hats On
Now let's look at tools that can be used to identify vulnerabilities, simulate attacks, and enhance their overall security posture, turning potential threats into valuable learning opportunities.
AmIcontained
Have a shell? In a container? Manually finding and translating information about your shells permissions is a pain. AmIContained will do the hard work for you: capabilities, blocked syscalls, weather apparmor and seccomp are enabled.
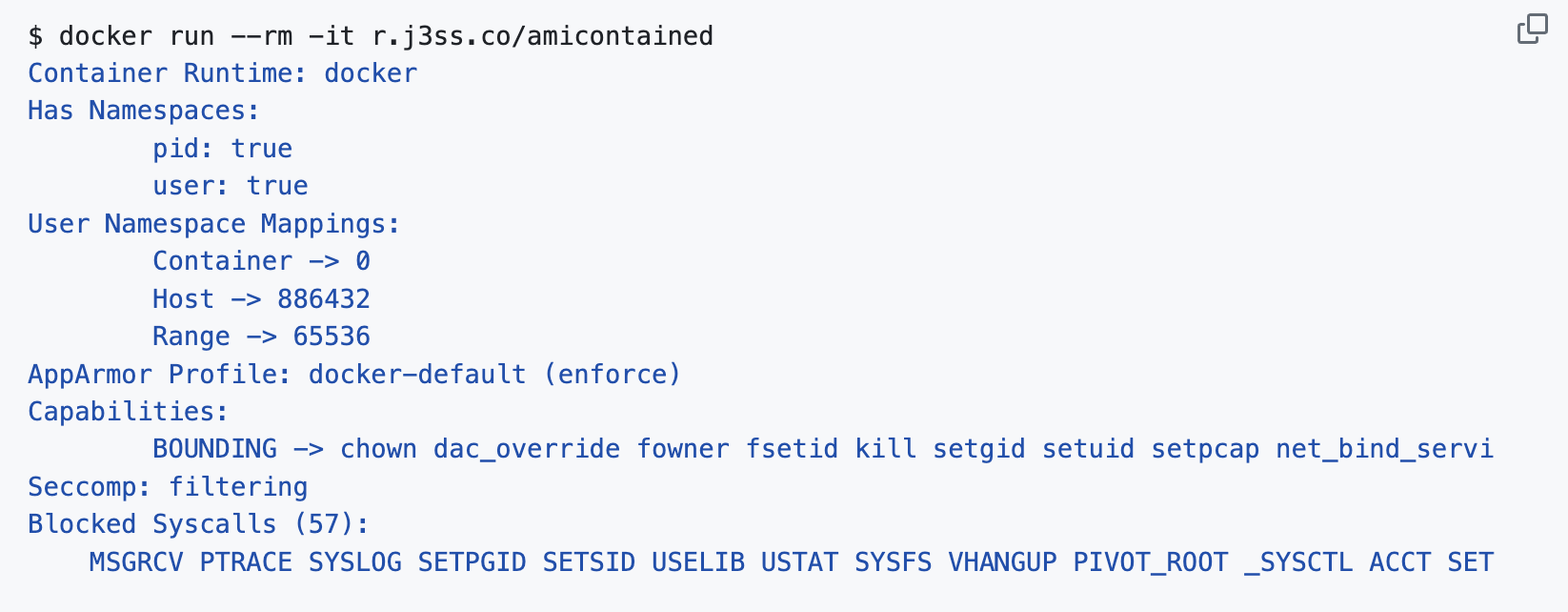
As a second benefit, trying to fetch it from the web also tells you if you have outbound network connectivity. As far as we are aware, there isn’t an official distribution by DNS TXT record.
ZAP
Sometimes you just need to see what's going on between a client and server, maybe mess around with a payload or two and see what sticks.
While ZAP has many more advanced features than that, it’s still a go-to when needing to debug something outside a browser. It’s also worth noting that their documentation and community is first rate.
We’re also big fans of the OWASP community, for which ZAP is a flagship project.
Training & Development
In the ever-evolving landscape of cybersecurity, leveraging open-source security tools for training and development has become essential for organizations aiming to enhance their defenses and stay ahead of potential threats. These tools not only provide cost-effective solutions but also offer extensive community support and adaptability, making them invaluable for building robust security protocols.
CI/CD Goat
The rise in supply chain attacks, such as SolarWinds and the Linux SSH XZ near-miss, emphasizes that the security of pipelines and build tooling is as critical as production systems. To this end, CI/CD Goat provides a testing range of intentionally vulnerable CI/CD configurations — all created using infrastructure as code to create an isolated security training ground.
Kubernetes Goat
A great place to get started with offensive Kubernetes Security, Kubernetes Goat is a purposely vulnerable set of Kubernetes deployments, cluster setups and training materials to explore common Kubernetes security issues. It also serves as a great repository for testing other Kubernetes-capable security scanners, such as Checkov and Kubescape.
Simulator by ControlPlane
Simulator is a Kubernetes security testing automation and simulation tool that powers all official CNCF SecurityCon and KubeCon capture-the-flags. They’re always a highlight of the shows for me, with amazing insights from the ControlPlane team. It’s awesome to see tools like this being made open source, and I’m looking forward to using it for our own learning and training exercises.
Learn More
We hope you enjoyed scouting out our OSS shortlist. Don’t forget to check out our new open-source page for Palo Alto Networks projects, community contributions and more.
And whether you’re new to containers or a cloud-native veteran, you'll want to download a copy of The Definitive Guide to Container Security, your essential resource for implementing and mastering security in a containerized environment. This book-length guide lays out in-depth insights and practical advice to empower developers, DevOps, cloud teams and security professionals to effectively protect their cloud-native applications.