New Capabilities That Protect Vulnerable Medical Devices without Disrupting Patient Care
In today’s hyperconnected healthcare environment, medical devices aren’t just endpoints—they’re lifelines.
The explosion of connected medical devices is transforming patient care—but it’s also creating a growing attack surface that cybercriminals are actively exploiting. With the number of connected medical devices expected to reach 1.3 billion by 2030, hospitals and healthcare organizations are increasingly at risk from vulnerabilities in these critical assets.
Since medical devices aren’t architected for security, many may have inherent vulnerabilities and run outdated software, making them prime targets for cyberattacks. As threats continue to rise, healthcare providers need a robust and scalable security solution that helps ensure their critical medical devices remain secure while minimizing disruptions to their clinical operations.
To address this, we’re excited to announce recent innovations in our Medical IoT Security product designed to protect these vital but vulnerable lifelines:
- New end-to-end risk management workflow with Guided Virtual Patching for accurate risk assessment and network-level protection of vulnerable medical, internet of things (IoT) and operational technology (OT) devices.
- Enhanced Query Builder, combined with Strata Copilot, gives users two powerful ways to simplify their device security posture management and compliance reporting.
Track Effective Risk and Protect Vulnerable Medical Devices at the Network Level with Guided Virtual Patching
CISA, the FDA, and the FBI have repeatedly warned of the risk posed by vulnerable, unpatched and outdated medical devices. The most recent warning alerted to vulnerabilities found in patient monitors. In the EU, the NIS2 directive also cites aging technology and outdated systems as one of the main reasons healthcare systems are increasingly vulnerable to cyberattacks.
Devices, like infusion pumps and patient monitors, which administer life-saving medications and track vital signs, can’t be taken offline to update or patch for extended periods without risking patient safety. When a vulnerability is found in these devices, healthcare security teams face a dilemma: If they apply patches immediately, they may have to take critical devices offline for extended periods, delaying essential treatments and disrupting hospital operations. If they wait, they risk leaving the devices exposed to potential exploitation, putting patient data and lives at risk.
Guided Virtual Patching Provides Real-Time Protection Without Disrupting Device Operations
This is where our Guided Virtual Patching provides a game-changing solution. Instead of forcing hospitals to choose between security and patient care, this AI-driven approach applies virtual patches in real-time—protecting vulnerable medical devices at the network level without disrupting their operation.
Government agencies like the NIH and ENISA also agree that implementing least-privileged access and using intrusion detection systems (IDS) and intrusion prevention systems (IPS) at the network level via the NGFW is a best practice approach to securing medical devices at scale.
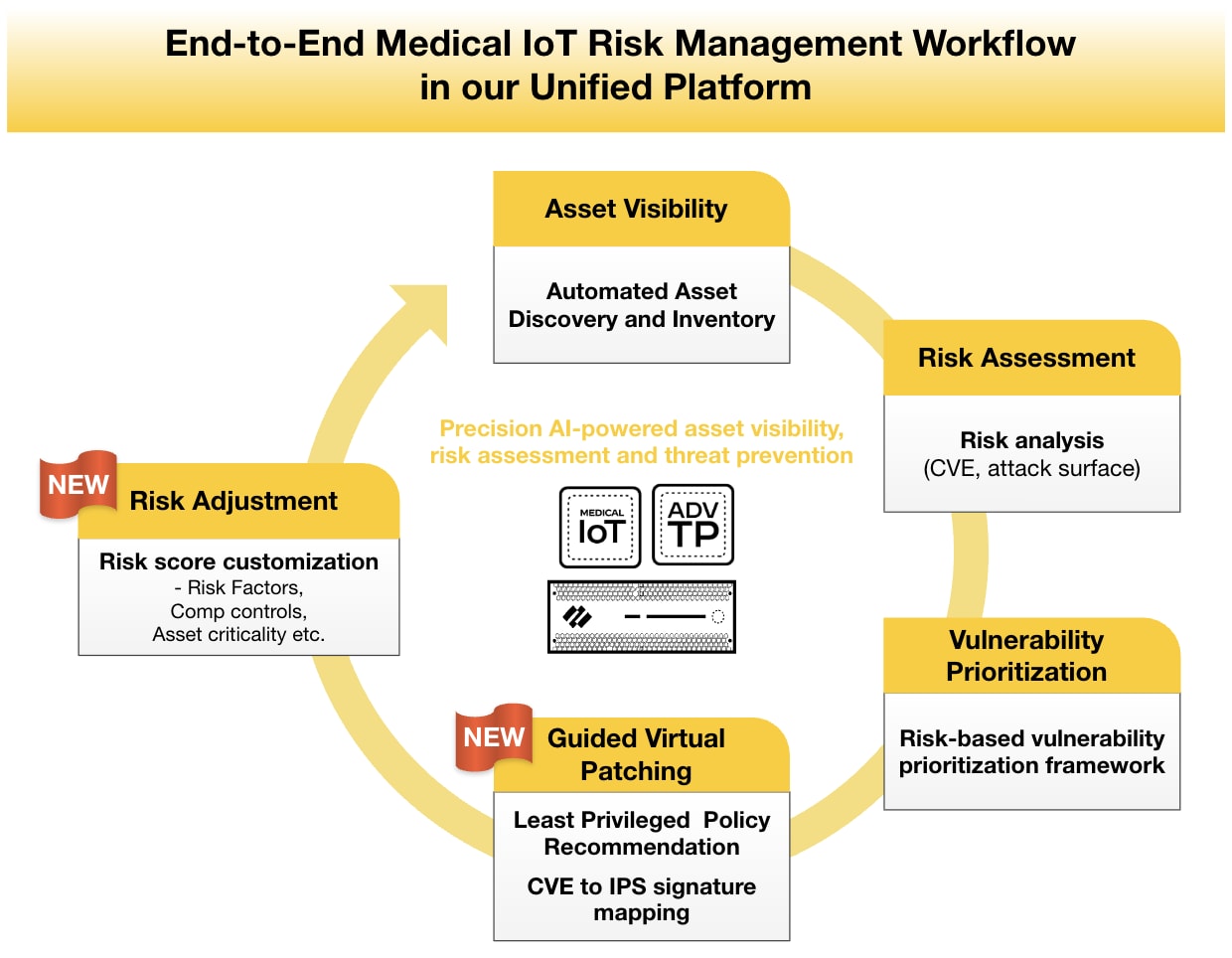
The new end-to-end risk management workflow with Guided Virtual Patching.
Guided Virtual Patching is a cornerstone of our new end-to-end risk management workflow. The process starts with comprehensive asset visibility, risk assessment and attack surface mapping of all connected medical, IoT and OT devices.
The next step in the workflow is a risk-based prioritization of critical vulnerabilities based on a multifactor risk score. This goes beyond just vulnerability metrics, taking into account factors like exploitability and asset criticality within the customer’s environment. Risk-based vulnerability prioritization enables overburdened security teams to focus their remediation efforts on the most critical vulnerabilities.
Then, Guided Virtual Patching leverages our Advanced Threat Prevention (ATP) to stop zero-day attacks inline in real time. This proactive approach incorporates tailored threat prevention profiles and least-privileged access policies to minimize exposure and effectively secure hard-to-patch medical devices, such as infusion pumps, patient monitors (collectively representing the biggest attack surface in hospitals), and imaging systems like MRI scanners—which represent some of the most expensive equipment.
With Guided Virtual Patching, healthcare organizations can benefit from robust, scalable network-level protection for medical and IoT devices. This not only ensures device protection at scale but also buys network security and biomedical teams much-needed time to apply software updates or patches to extend the useful cyber lifespan of these devices.
And finally, our new Risk Adjustment feature enables healthcare organizations to understand and customize the effective risk exposure of their connected devices to make informed and adaptive security decisions that reduce the attack surface.
Not all medical devices pose the same risk, and their impact varies across different healthcare environments. For example, a typically low-risk infusion pump, which lacks endpoint security, located in an intensive care unit (ICU) might become a high-priority risk if connected to the internet. In contrast, a more traditionally critical imaging system, such as an MRI scanner, might pose a lower risk if it is isolated within a segmented network and has endpoint security. Factors like asset criticality, network exposure and existing security controls can significantly alter a device's actual risk to a healthcare organization.
Customizable risk scores enable security teams to tailor risk parameters based on various factors, such as a device’s criticality, existing compensating controls and other elements contributing to asset risk. These factors include whether a device is connected to the internet, lacks endpoint security, or has other vulnerabilities. Each risk factor is assigned a specific weight, ensuring that the overall effective risk score accurately reflects the actual threat to the healthcare organization. This fine-tuning allows security teams to better assess risks and implement effective mitigation strategies.

The risk score details page shows the breakdown of the device risk score and the contributing risk factors.

![]() The risk score configuration page enables users to customize the weight of each risk factor, ensuring an accurate calculation of the effective risk score.
The risk score configuration page enables users to customize the weight of each risk factor, ensuring an accurate calculation of the effective risk score.
Medical IoT Security automatically detects risks, weak security posture and potential mitigations. Customers can use the flexible rules to modify or assign weights to the risk factors and compensating controls. This streamlined, end-to-end workflow helps healthcare organizations cut through the noise, focus on top-priority vulnerabilities, and manage risks effectively and efficiently to help ensure mission-critical medical devices remain secure and fully operational without disrupting patient care.
Simplify Device Security Posture Management and Compliance Reporting with Strata Copilot and Enhanced Query Builder
Today, healthcare organizations face a cumbersome, manual and error-prone approach to managing their device security hygiene reporting and compliance. This can significantly strain their IT and security resources and impact their ability to protect their patient lifelines effectively.
With this in mind, we’re offering users two powerful ways that simplify how they retrieve, analyze and report on medical and IoT device security-related data:
- Strata Copilot enables users to access actionable device security insights using simple conversational prompts
- Enhanced Query Builder makes it easy for users to build and repeat structured queries ensuring consistency and precision
Strata Copilot
Strata Copilot provides users with a simple natural-language interface to access actionable device security insights. This powerful tool draws from real-time product data and a broad set of almost 50,000 vetted sources, including Palo Alto Networks technical documentation and LIVEcommunity blogs, to put all that knowledge at network security practitioners' fingertips. With Strata Copilot, healthcare organizations can quickly assess device security posture through natural-language queries and customize how the information is displayed.
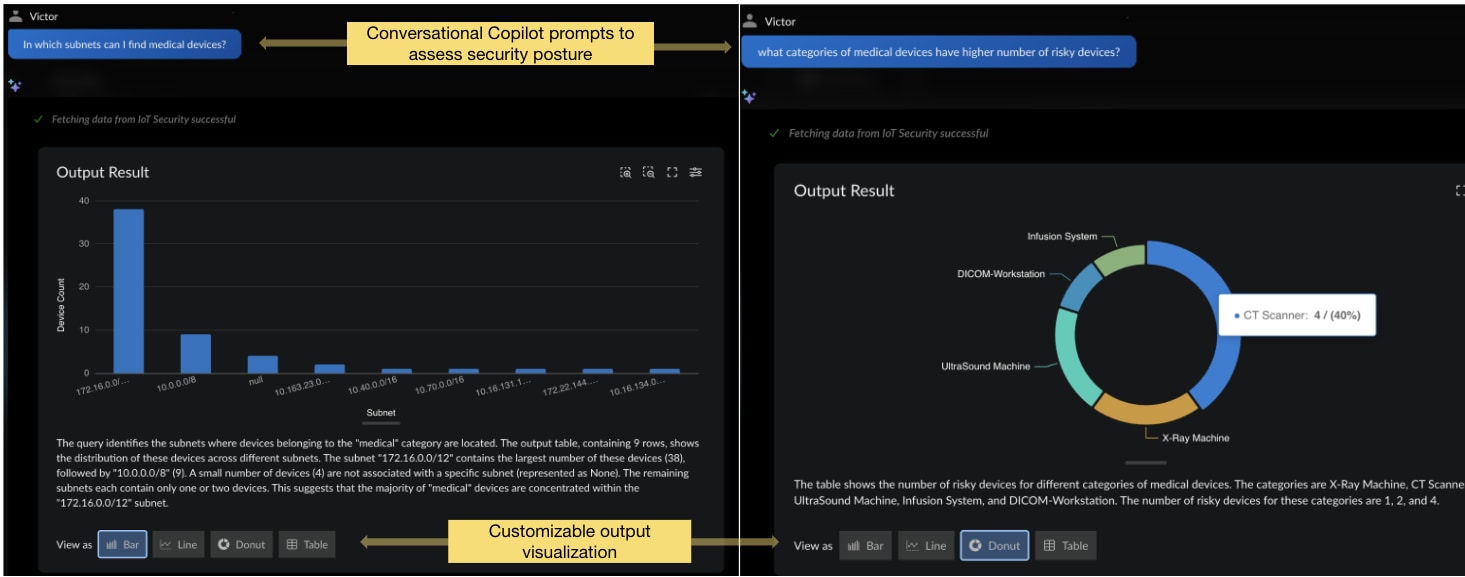
Strata Copilot provides a conversational interface for users to access device security hygiene insights and customize the visualization.
Query Builder
Our enhanced Query Builder tool enables users who prefer a more structured query language to fine-tune their analysis with precise device and risk attributes. Users can now easily perform complex and targeted searches in a consistent and repeatable way using our refined Query Library to pinpoint device security hygiene issues. Maintaining and reporting on security compliance is now easier than ever with our new scheduled queries, custom dashboards and out-of-box compliance reports.
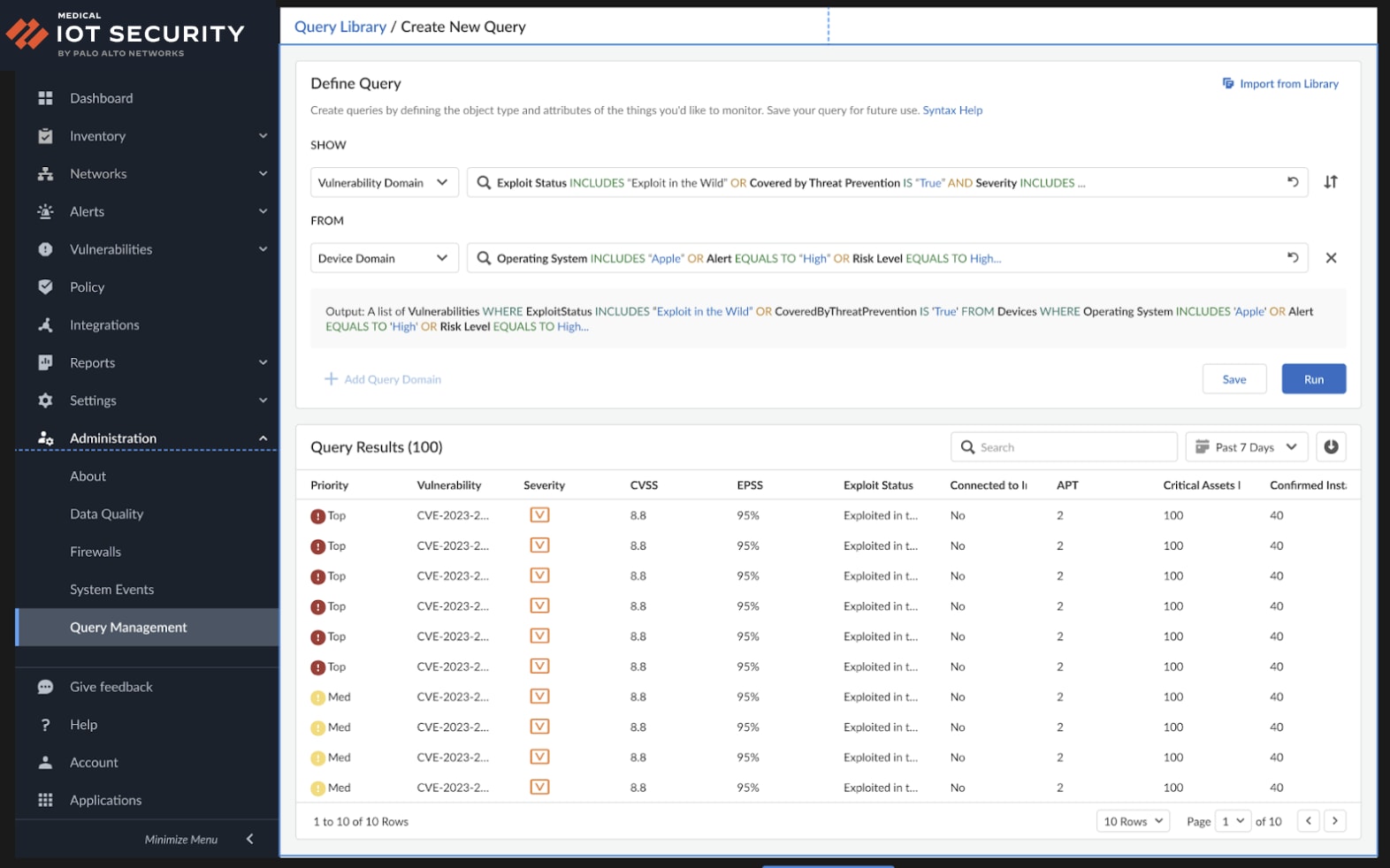
The query library within Query Builder offers prewritten standardized queries that users can select and execute immediately, saving time and effort.
These enhancements provide customers with precise device security hygiene insights instantly at their fingertips empowering hospitals to proactively manage their device security posture and help ensure compliance.
The Management Benefits of Strata Copilot and Query Builder
Strata Copilot and Query Builder radically simplify medical device security posture management through:
- Proactivity that allows for early detection of vulnerabilities and compliance issues.
- Precision to tailor the data retrieved to exact specifications, reducing noise and focusing on areas of concern.
- Efficiency with automated data retrieval processes allows healthcare cybersecurity professionals to act swiftly on findings rather than manually compiling reports.
Keep Healthcare Lifelines Secure with Palo Alto Networks Medical IoT Security
Integrating these innovative features into Medical IoT Security not only sets a new standard in medical device security, but also transforms how healthcare professionals manage and interact with their connected devices.
Register for our upcoming hands-on workshops or sign up for a free trial to experience how enhanced Medical IoT Security can revolutionize your medical device security strategy.