Modern workplaces are embracing more technology to improve employees’ experiences and productivity as well as to support hybrid workforces. This digital transformation across the enterprise drives greener, safer and more efficient operations with the help of cloud and IoT technologies, such as collaboration tools, real-time monitoring and connected office IoT devices.
Corporate networks are seeing a spike in consumer IoT devices. These range from connected printers and coffee makers to smart speakers and cars. And their numbers are growing. IoT devices are projected to be over 30% of total devices on corporate networks.
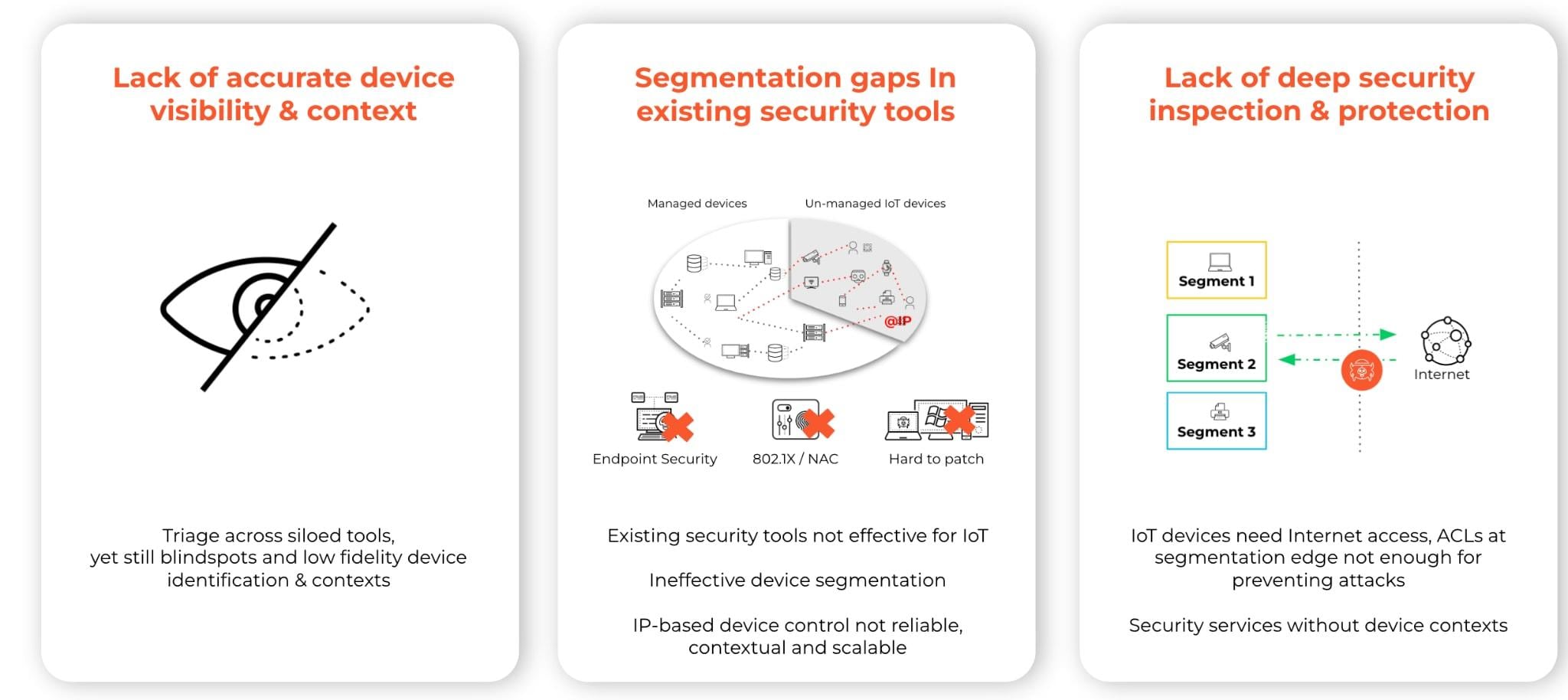
While connected devices deliver undeniable benefits, they also represent an unprecedented risk as IoT devices are often overlooked and not fully integrated into overall IT security strategies. The result is that connected devices are one of the weakest links of the enterprise network for several reasons, including IoT devices that are:
- Often not visible and unmanaged, lacking the protection of enterprise security controls, such as endpoint security and vulnerability scanners.
- Reliant on unsupported operating systems that are difficult to patch.
- Lack of segmentation due to lack of visibility and accurate device identification.
- Susceptible due to gaps in existing security tools.
- Not subject to clear protocols for who should secure IoT devices.
- Using legacy security architectures that hinder compliance.
The scale of these vulnerabilities may come as a surprise. More than 70% of enterprises have experienced hacking attempts on their IoT devices, and 25% of attacks involve IoT in the kill chain.

These vulnerabilities, when not addressed, can cause a significant impact to your network. Many IoT devices have enough system resources to be a jump host for lateral movement to allow attacks to crawl into the rest of the enterprise network.
IoT security is often overlooked and has real challenges, like the following:
- IoT devices are not fully covered by existing enterprise security controls, like endpoint security or vulnerability scanners.
- Most enterprise InfoSec teams don't have the expertise or resources to investigate IoT vulnerabilities. In the end, it’s much more costly to patch these unmanaged IoT devices, compared to managed IT devices.
- Segmentation is a common technique used for IoT devices, but often not efficient due to lack of visibility, accurate device identification, lack of granular control and threat prevention.
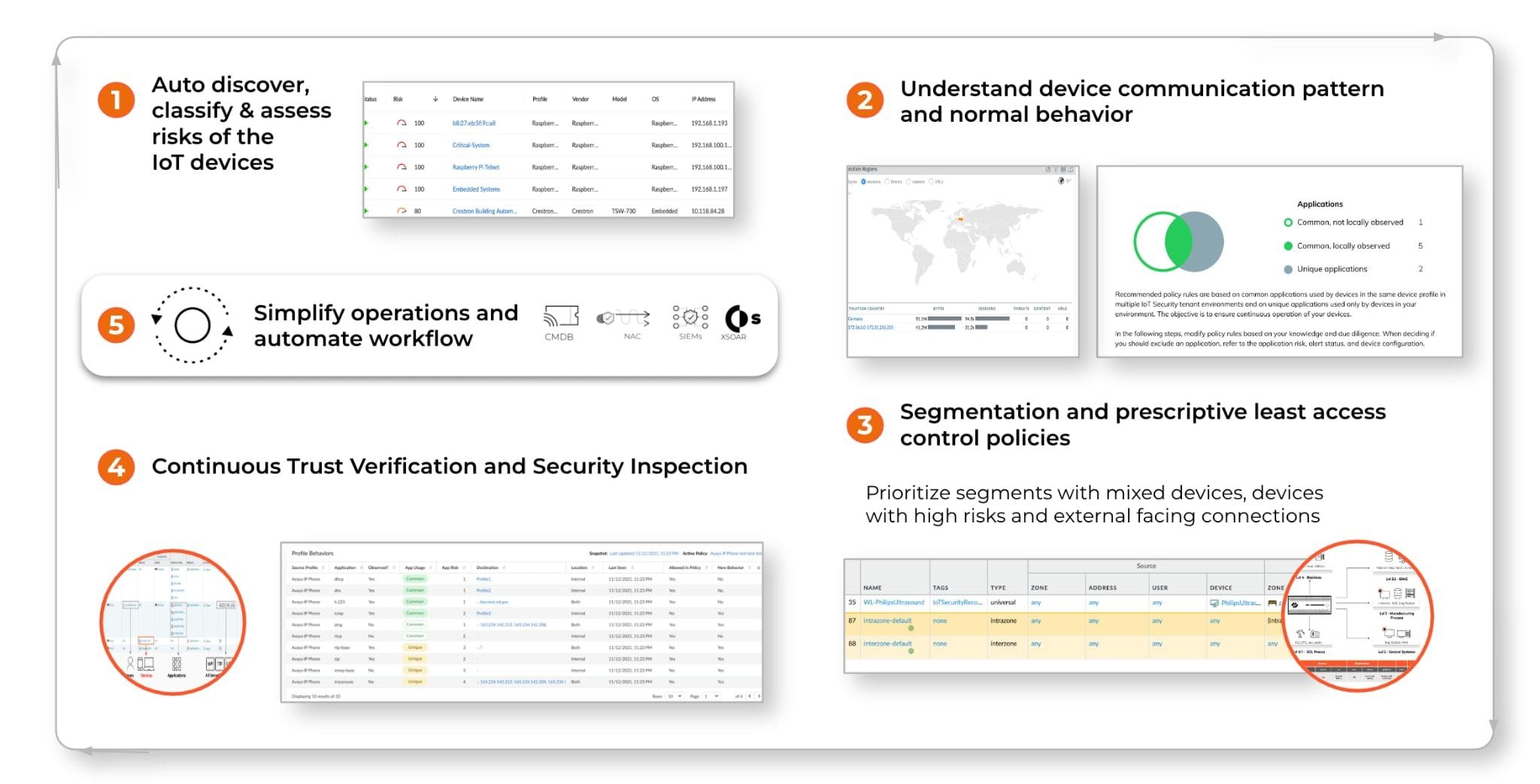
We need a different way to secure IoT devices with the right visibility, control and security protection. Here are some of the key considerations, leveraging a Zero Trust principle:
- First, establish a comprehensive and accurate inventory of your devices.
- Assume “not up to patch” is the norm for your IoT devices, and use contextual dynamic device segmentation and least privilege access control, augmented by the device visibility and risk contexts to help control (Internet) access, reduce threat surface and prevent lateral movement.
- Continuous monitoring for trust verification and security inspections, such as threat prevention and behavior anomaly detection.
- Automate your workflows.
One of the common questions we receive from customers is: “We have many types of IoT devices. Where do I start?” Here are a couple considerations to help you prioritize in your IoT security journey:
- Look for network segments where you have a mix of IoT and IT devices.
- Look for high risk IoT devices, especially the ones with high vulnerabilities that are already weaponized, that are exposed to external facing networks.
- Look for IoT blindspots from existing segmentation solutions, due to lack of accurate device identification.
Machine learning (ML) and AI can help you scale. IoT device behavior should be predictable and is a good use case to leverage ML to provide a high fidelity and scalable solution for device identification and behavior baseline and anomaly detection.
As IoT devices become mainstream devices in your enterprise workplace, it is also important to make sure IoT security is part of your security infrastructure and workflows, as opposed to being a siloed approach.
Palo Alto Networks Enterprise IoT Security Can Help You
Fully embedded in our Next-Generation Firewall (NGFW) and Prisma Access platforms, our Enterprise IoT Security closes the loop by combining IoT device visibility and risk insight, Device-ID based contextual segmentation and least privilege access policy with continuous trust verification, and threat prevention and behavior anomaly detection.
Palo Alto Networks Enterprise IoT Security, complemented by its Zero-Trust framework, is the only solution in the market today that enables maximum return on investment (ROI) and enhanced efficiency. This unique solution provides deep visibility, focused operational insights and enhanced security for all connected devices in one platform.