Recently, the discussion surrounding application visibility and control provided by next-generation firewalls has become deafening. Now, every stateful inspection based firewall vendor is calling themselves a next-generation firewall that can identify and control applications. A remarkable feat, given that they are all still using port and protocol as the primary traffic classification mechanism and that all application identification is being done by a bolt-on IPS engine.
In some respects, the added discussion is beneficial because it means that the traditional vendors recognize that their existing, port-based products are relatively ineffective at classifying the traffic on corporate networks. However, the increased noise means it is even more important to clarify the fundamental differences between App-ID, the traffic classification technology used in Palo Alto Networks next-generation firewalls and the classification mechanisms used in other offerings [learn more about how App-ID works].
The fundamental differences can be summarized by the Rule of All.
- All App-IDs are always on: Every one of the App-IDs are always enabled. They are not optional, there is no need enable a series of signatures to look for an application.
- Always the first action taken: App-ID traffic classification is always the first action taken when traffic hits the Palo Alto Networks next-generation firewall. Like all firewalls, our device is default deny all traffic. Policies are enabled to begin allowing traffic, at which time, all App-IDs begin to classify traffic without any additional configuration efforts.
- All of the traffic: App-ID is always classifying all of the traffic - not just a subset of the traffic (like HTTP for IPS). All App-IDs are looking at all of the traffic passing through the device, business applications, consumer applications, network protocols, and everything in between. There is no need to configure App-ID to look at a specific subset of traffic. It automatically looks at all of it.
- All ports: App-ID is always looking at every port. Again, there is no need to configure App-ID to look for an application on a non-standard port. It is automatic.
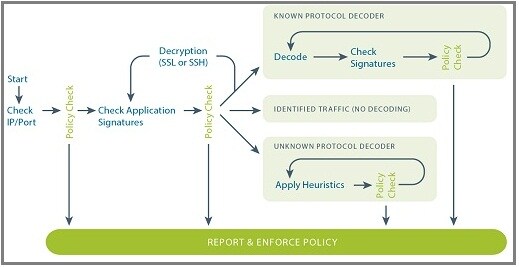
- All versions, all OSes: App-ID operates at the services layer, monitoring how the application interacts between the client and the server. This means that App-ID is indifferent to new features, and it is client or server operating system agnostic. The result is that a single App-ID for BitTorrent is going to be roughly equal to the many BitTorrent signatures that need to be enabled to try and control this application.
- All classification techniques: Each App-ID is not just an IPS-like signature. Every App-ID will automatically use up to four different traffic classification mechanisms to determine the exact identity of the application. There is no need to apply specific settings for a specific application, App-ID systematically applies the appropriate mechanism.
Palo Alto Networks users will initially see the result of App-ID and the Rule of All in ACC where, with a single firewall rule of any-any-allow, the details on applications, users, threats can be viewed quickly and easily with a few clicks of a mouse. The Rule of All is then extended into the policy editor where, with equal ease, an administrator can establish positive control model policies to enable the use of applications. Finally, logging, reporting and analysis takes full advantage of the Rule of All, allowing an administrator to investigate security incidents, perform traffic and threat analysis and generate reports based on the exact application identity [learn more about how App-ID works].
So how can you clarify the discussion and determine what the other vendors are saying? Ask these questions:
- Are all of the application identification techniques enabled by default?
- Is the application identification technique looking at all traffic or a subset thereof?
- Are the application identification techniques automatically applied across all ports, or is that a configuration setting?
- How many steps will it take to enable all the application identification techniques for all traffic for all ports?
Thanks for reading.
Matt