A new report by the Digital Citizens Alliance uses the payment structure (fees and credit card processing) of the top 30 cyberlockers to show how they profit illicitly from direct download or streaming of copyrighted materials. Cyberlockers are part of the browser-based filesharing categorization within our taxonomy and we find many of them on the networks we analyze. In short, these cyberlockers put both your company and your users at risk.
The report is very explicit in the view that the use of cyberlockers is primarily for theft, stating, “At least 78.6 percent of files on direct download cyberlockers and 83.7 percent of files on streaming cyberlockers infringed copyright.” Delving further into the report the researchers analyzed the fee structures and user base and were able to uncover the following revenue statistics:
- The approximate profit ratios for streaming and direct download cyberlockers was 87.6% and 63.4% respectively.
- Both types of applications make money through premium subscriptions and advertising, but the volume of each is polar opposite.
- 6 percent of direct download cyberlockers generate 70.6% and 29.4% of their revenue from subscription services and advertising respectively. Nearly the exact opposite was found in the streaming cyberlocker analysis 71.1% came from advertising and 23.1% from premium account subscriptions.
Cyberlockers Found on Customer Networks
Of the cyberlockers analyzed in the report, we saw five of them on 25% to 54% of the 5,551 customer networks analyzed in the 2014 Application Usage and Threat Report. (Table 1)
- 4shared and Mega, the replacement for MegaUpload, are found on 54% and 29% of the networks we analyze. In the report, these two applications are the 2 most heavily visited direct download cyberlockers.
- Depositfiles, the 11th most popular cyberlocker was found on 29% of the networks we analyze.
- Putlocker, the most popular streaming cyberlocker in the Digital Alliance report was found on 31% of the networks we analyze while FilesTube, a metasearch site supporting cyberlockers was found 23% of the time.
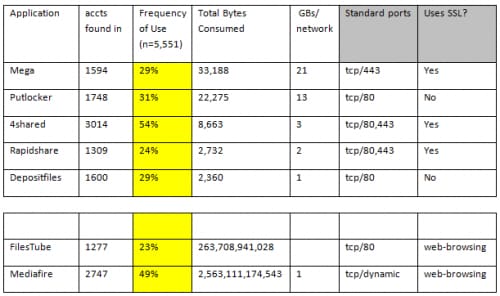
Table 1.
In previous blog posts I have made the assertion that browser-based filesharing applications would supplant P2P for accessing copyrighted files because they are easier to use and they use port 80 or port 443, making them harder detect. P2P still consumes more bandwidth than any other set of applications, but cyberlockers are gaining in popularity and represent security and business.
According to the copyright alert guidelines, users of P2P services are given a series of six warnings before to prove they are not in violation of the law. If a user is on your network, you will be responsible for finding that user and providing the necessary information to address the allegation. Responding to copyright infringement allegations takes time, costs money and if left unchecked may result in damage to your reputation.
Protecting Your Users and Your Company From Copyright Infringement
With our Next-Generation Firewall, users can exert enablement policies for filesharing/file transfer applications using security best practices and a variety of standard features.
Learn which filesharing applications are in use and who the users are. We identify 232 filesharing applications, including those that are client/server-based, those that use P2P and those that are browser-based. Based on the 2014 Application Usage and Threat Report, 93% of the networks we analyzed had an average of 25 filesharing applications appearing. The breakdown is as follows:
- An average of 8 client/server filesharing applications on 91% of the networks analyzed.
- On 77% of the networks we analyzed, there were 5 P2P applications found.
- An average of 12 browser-based filesharing applications were found on 91% of the networks.
Understand the use case for so many variants. There are few if any business reasons for 23 variantts of a single type of application to reside on any one given network. Once you know the applications in use, there will be some – like Putlocker, or Mega – that you may summarily block. Others, like Dropbox or Box.net, or Hightail are more business oriented and warrant added conversation with the user community. The key here is to work with the business groups in order to find out why the applications are in use –what do they need it for. Once more data is collected, build a case to securely enable it or get rid of it.
Establish policy and enforce it using technology. Once the agreement has been reached on which filesharing applications are allowed, and the policy has been documented, you can use technology to enforce it using a combination of rules.
- Allow, based on application name and perhaps user group, a small set of filesharing applications.
- Explicitly block a larger group, such as P2P filesharing using dynamic filters. These are rules that are dynamically updated as your content (App-ID, threat signatures, etc,) minimizing the time you would need to spend manually updating block policies.
- Create custom URL blacklists to block those cyberlockers not included as part of the App-ID database.
Continually monitor and update the policy. The application landscape continually changes as do user requirements, so it is important to monitor the applications and maintain a regular dialog with the user groups.